| Oracle GlassFish Server Quick Start Guide Release 3.1.2 Part Number E24937-01 |
|
|
View PDF |
| Oracle GlassFish Server Quick Start Guide Release 3.1.2 Part Number E24937-01 |
|
|
View PDF |
The examples and procedures in Quick Start for Basic Features introduce the features and capabilities of GlassFish Server, but are not intended for production deployments. This chapter provides examples of how GlassFish Server can be used in production.
The following topics are addressed here:
This example provides all the steps for configuring a cluster in which iPlanet Web Server is used with the load balancer plug-in for load balancing of two GlassFish Server instances. A simple web application is deployed to this cluster. Users of this application access the application through a virtual server.
Note:
In this example, line breaks are included for enhanced readability. These line breaks are not part of the syntax of the commands.
The assumptions for this example are as follows:
The domain administration server (DAS) will run on the host dashost.example.com.
The web server and load balancer plug-in will run on the host lbhost.example.com.
The instances will run on the hosts sj01.example.com and sj02.example.com
All steps are performed by the user gfuser.
On the DAS host, the parent of the base installation directory of the Oracle GlassFish Server software is /home/gfuser/glassfish3.
The path of user gfuser contains the directory /home/gfuser/glassfish3/bin.
Secure shell (SSH) software is installed and configured on each host.
The SSH Server Daemon sshd is running on each host.
The configuration of the cluster in this example is shown in the following figure.
The following topics are addressed here:
All steps in this procedure are performed from the DAS host.
Start the asadmin utility in multiple command mode (multimode).
dashost$ asadmin
Use "exit" to exit and "help" for online help.
Set up public key authentication without encryption on the hosts where the instances will run.
asadmin> setup-ssh sj01.example.com sj02.example.com SSH key not found for user gfuser Would you like to generate a SSH key pair (without a key passphrase) for gfuser to access [sj01.example.com, sj02.example.com]? [y/n]: yes Enter SSH password for [email protected]> Created directory /home/gfuser/.ssh /usr/bin/ssh-keygen successfully generated the identification /home/gfuser/.ssh/id_rsa Copied keyfile /home/gfuser/.ssh/id_rsa.pub to [email protected] Successfully connected to [email protected] using keyfile /home/gfuser/.ssh/id_rsa Successfully connected to [email protected] using keyfile /home/gfuser/.ssh/id_rsa SSH public key authentication is already configured for [email protected] Command setup-ssh executed successfully.
Copy the installation of GlassFish Server software from the DAS host to the hosts where the instances will run.
asadmin> install-node --installdir /export/glassfish3 sj01.example.com sj02.example.com Created installation zip /home/gfuser/glassfish3033977962688704206.zip Successfully connected to [email protected] using keyfile /home/gfuser/.ssh/id_rsa Copying /home/gfuser/glassfish3033977962688704206.zip (90012883 bytes) to sj01.example.com:/export/glassfish3 Installing glassfish3033977962688704206.zip into sj01.example.com:/export/glassfish3 Removing sj01.example.com:/export/glassfish3/glassfish3033977962688704206.zip Fixing file permissions of all files under sj01.example.com:/export/glassfish3/bin Successfully connected to [email protected] using keyfile /home/gfuser/.ssh/id_rsa Copying /home/gfuser/glassfish3033977962688704206.zip (90012883 bytes) to sj02.example.com:/export/glassfish3 Installing glassfish3033977962688704206.zip into sj02.example.com:/export/glassfish3 Removing sj02.example.com:/export/glassfish3/glassfish3033977962688704206.zip Fixing file permissions of all files under sj02.example.com:/export/glassfish3/bin Command install-node executed successfully.
Start the domain domain1.
asadmin> start-domain domain1
Waiting for domain1 to start ............................
Successfully started the domain : domain1
domain Location: /home/gfuser/glassfish3/glassfish/domains/domain1
Log File: /home/gfuser/glassfish3/glassfish/domains/domain1/logs/server.log
Admin Port: 4848
Command start-domain executed successfully.
Enable secure administration for the DAS host.
asadmin> enable-secure-admin
Command enable-secure-admin executed successfully.
Restart the domain domain1.
asadmin> restart-domain domain1
Successfully restarted the domain
Command restart-domain executed successfully.
Add the cluster pmdcluster to the DAS configuration.
asadmin> create-cluster pmdcluster
Command create-cluster executed successfully.
Create a node for each host on which the instances will run.
Create the node sj01 to represent the host sj01.example.com.
asadmin> create-node-ssh --nodehost sj01.example.com --installdir /export/glassfish3 sj01 Command create-node-ssh executed successfully.
Create the node sj02 to represent the host sj02.example.com.
asadmin> create-node-ssh --nodehost sj02.example.com --installdir /export/glassfish3 sj02 Command create-node-ssh executed successfully.
Add the instances pmd-i1 and pmd-i2 to the cluster pmdcluster.
Add the instance pmd-i1 on the node sj01.
asadmin> create-instance --node sj01 --cluster pmdcluster pmd-i1
Command _create-instance-filesystem executed successfully.
Port Assignments for server instance pmd-i1:
JMX_SYSTEM_CONNECTOR_PORT=28686
JMS_PROVIDER_PORT=27676
HTTP_LISTENER_PORT=28080
ASADMIN_LISTENER_PORT=24848
JAVA_DEBUGGER_PORT=29009
IIOP_SSL_LISTENER_PORT=23820
IIOP_LISTENER_PORT=23700
OSGI_SHELL_TELNET_PORT=26666
HTTP_SSL_LISTENER_PORT=28181
IIOP_SSL_MUTUALAUTH_PORT=23920
The instance, pmd-i1, was created on host sj01.example.com
Command create-instance executed successfully.
Add the instance pmd-i2 on the node sj02.
asadmin> create-instance --node sj02 --cluster pmdcluster pmd-i2
Command _create-instance-filesystem executed successfully.
Port Assignments for server instance pmd-i2:
JMX_SYSTEM_CONNECTOR_PORT=28686
JMS_PROVIDER_PORT=27676
HTTP_LISTENER_PORT=28080
ASADMIN_LISTENER_PORT=24848
JAVA_DEBUGGER_PORT=29009
IIOP_SSL_LISTENER_PORT=23820
IIOP_LISTENER_PORT=23700
OSGI_SHELL_TELNET_PORT=26666
HTTP_SSL_LISTENER_PORT=28181
IIOP_SSL_MUTUALAUTH_PORT=23920
The instance, pmd-i2, was created on host sj02.example.com
Command create-instance executed successfully.
Start the cluster pmdcluster.
asadmin> start-cluster pmdcluster
Command start-cluster executed successfully.
Confirm that the instances in the cluster pmdcluster are running.
asadmin> list-instances
pmd-i1 running
pmd-i2 running
Command list-instances executed successfully.
End the multimode session for the asadmin utility.
asadmin> exit
Command multimode executed successfully.
All steps in this procedure are performed from the host where the web server and load balancer plug-in will run.
This example assumes that the path of user gfuser contains the /home/gfuser/webserver7/bin directory.
Download the web server software from the Oracle iPlanet Web Server download page.
Extract the contents of the download file.
lbhost$ unzip iplanet_webserver_sun_sparc_7.0.12_64.zip
Start the iPlanet Web Server installation wizard.
lbhost$ setup &
Follow the onscreen instructions in the installation wizard to install iPlanet Web Server.
Other steps in this procedure assume the following option settings:
Installation Directory: /home/gfuser/webserver7
Type of Installation: Express
Administrator User Name: admin
Start Administration Server: checked
Start the wadm utility in multimode.
lbhost$ wadm --user=admin
Please enter admin-user-password>
Connected to localhost:8989
Oracle iPlanet Web Server 7.0.12 B07/04/2010 02:15
Create a self-signed certificate for secure communication between the load balancer plug-in and the DAS.
wadm> create-selfsigned-cert --server-name=lbhost.example.com --nickname cert-lbhost --token=internal --config=lbhost CLI201 Command 'create-selfsigned-cert' ran successfully
Create a secure HTTP listener for the iPlanet Web Server instance lbhost.
wadm> create-http-listener --server-name lbhost.example.com --default-virtual-server-name=lbhost --listener-port 8082 --config lbhost http-listener-ssl CLI201 Command 'create-http-listener' ran successfully
Enable SSL with optional client authentication and assign the certificate for the HTTP listener.
wadm> set-ssl-prop --http-listener http-listener-ssl --config lbhost enabled=true client-auth=optional server-cert-nickname=cert-lbhost CLI201 Command 'set-ssl-prop' ran successfully
Deploy the configuration for the iPlanet Web Server instance lbhost.
wadm> deploy-config lbhost
CLI201 Command 'deploy-config' ran successfully
End the multimode session for the wadm utility.
wadm> exit
Unless otherwise stated, all steps in this procedure are performed from the host where the web server and load balancer plug-in will run.
From the DAS host, export the self-signed certificate of the DAS to enable secure communication between the HTTP listener and the DAS.
dashost$ keytool -export -rfc -alias s1as -keystore /home/gfuser/glassfish3/glassfish/domains/domain1/config/keystore.jks -file ./s1as.rfc Enter keystore password: Certificate stored in file <./s1as.rfc>
Transfer the DAS certificate file s1as.rfc from the DAS host to the host where the web server and load balancer plug-in will run.
Download the GlassFish Loadbalancer Configurator 3.1 from the Components section of the Oracle GlassFish Downloads page.
Extract the contents of the download file.
lbhost$ unzip glassfish-lbconfigurator-3_1.zip
Archive: glassfish-lbconfigurator-3_1.zip
inflating: glassfish-lbconfigurator-3_1.jar
Start the GlassFish Loadbalancer Configurator.
lbhost$ java -jar glassfish-lbconfigurator-3_1.jar
Follow the onscreen instructions in the GlassFish Loadbalancer Configurator to install and configure the load balancer plug-in.
Other steps in this procedure assume the following option settings:
Web Server Instance Directory: /home/gfuser/webserver7/https-lbhost
DAS Certificate File: s1as.rfc
Start the iPlanet Web Server instance lbhost, to which the load balancer plug-in was installed.
lbhost$ wadm start-instance --user=admin --config=lbhost
Please enter admin-user-password>
CLI204 Successfully started the server instance.
All steps in this procedure are performed from the DAS host.
This example assumes that the host name pmd.example.com is registered with the DNS server for the example.com domain.
Start the asadmin utility in multimode.
dashost$ asadmin
Use "exit" to exit and "help" for online help.
Create the virtual server pmdserver to represent the virtual host pmd.example.com.
asadmin> create-virtual-server --hosts pmd.example.com --networklisteners http-listener-1 --target pmdcluster pmdserver Command create-virtual-server executed successfully.
Deploy the hello application to the cluster pmdcluster.
asadmin> deploy --availabilityenabled=true --target pmdcluster --virtualservers pmdserver /home/gfuser/apps/hello.war Application deployed with name hello. Command deploy executed successfully.
Create the HTTP load balancer configuration pmdcluster-lb-config for the cluster pmdcluster.
asadmin> create-http-lb --devicehost lbhost.example.com --deviceport 8082 --target pmdcluster --lbenableallinstances --lbenableallapplications=hello pmdcluster-lb-config Command create-http-lb executed successfully.
Apply the HTTP load balancer configuration pmdcluster-lb-config.
asadmin> apply-http-lb-changes pmdcluster-lb-config
Command apply-http-lb-changes executed successfully.
End the multimode session for the asadmin utility.
asadmin> exit
Command multimode executed successfully.
To access the application, open the location https://pmd.example.com:8082/hello/ in a web browser.
This example demonstrates how to configure an Oracle 11 database as a JDBC resource for an application. The information in this example is based on "Administering Database Connectivity" in Oracle GlassFish Server Administration Guide, which explains how to configure any database that is supported by GlassFish Server as a JDBC resource.
The database in this example is used by the HR application perk-olator, which provides information to employees about special savings the company has arranged for its employees.
The assumptions for this example are as follows:
GlassFish Server has been installed and configured according to the example Deploying an Application to a Two-Instance Cluster.
The details about the database that the application uses are as follows:
The Oracle 11 database is running on empdb.example.com and listening for connections on the default port (1521).
The name of the database is EMP_PERKS.
The database user name is perk_app, and this user's password is perks4emps.
The perk-olator application looks up the JNDI name jdbc/emp_perks to access the data source.
The configuration of the components in this example is shown in the following figure.
Figure 2-2 Sample Two-Instance Cluster Accessing an Oracle Database
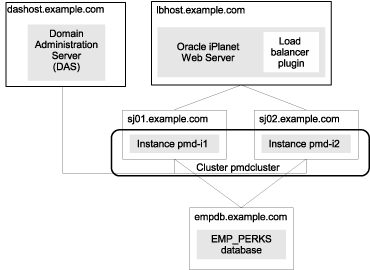
Configuring the Oracle 11 database as a JDBC resource for the perk-olator application involves the following tasks:
Integrating the JDBC driver for Oracle 11 into GlassFish Server.
Creating a JDBC connection pool for the resource.
Creating the JDBC resource.
Note:
In this example, line breaks are included for enhanced readability. These line breaks are not part of the syntax of the commands.
To integrate the JDBC driver, you copy its JAR file into the domain and then restart the domain and instances to make the driver available.
On dashost.example.com, copy the JAR file for the JDBC driver into the domain's lib subdirectory.
dashost$ cd /home/gfuser/glassfish3 dashost$ cp oracle-jdbc-drivers/ojdbc6.jar glassfish/domains/domain1/lib
Start the asadmin utility in multiple command mode (multimode).
dashost$ asadmin
Use "exit" to exit and "help" for online help.
Restart the domain to make the JDBC driver available to the domain administration server (DAS).
asadmin> restart-domain domain1
Command restart-domain executed successfully.
Restart instances in the domain to make the JDBC driver available to them.
asadmin> list-instances pmd-i1 running pmd-i2 running Command list-instances executed successfully. asadmin> restart-instance pmd-i1 Command restart-instance executed successfully. asadmin> restart-instance pmd-i1 Command restart-instance executed successfully.
Exit the multimode session for the asadmin utility.
asadmin> exit
Command multimode executed successfully.
Use the create-jdbc-connection-pool(1) subcommand to create the JDBC connection pool, specifying the database connectivity values provided to you.
On dashost.example.com, start the asadmin utility in multiple command mode (multimode).
dashost$ asadmin
Use "exit" to exit and "help" for online help.
Create the JDBC connection pool.
asadmin> create-jdbc-connection-pool --restype javax.sql.DataSource --datasourceclassname oracle.jdbc.pool.OracleDataSource --property "user=perk_app:password=perks4emps: url=jdbc\\:oracle\\:thin\\:@empdb.example.com\\:1521\\:EMP_PERKS" Emp_Perks-Pool JDBC connection pool Emp_Perks-Pool created successfully. pmd-i1: JDBC connection pool Emp_Perks-Pool created successfully. pmd-i2: JDBC connection pool Emp_Perks-Pool created successfully. Command create-jdbc-connection-pool executed successfully.
In this command, note the use of two backslashes (\\) preceding the colons in the url property value. These backslashes cause the colons to be interpreted as part of the property value instead of as separators between property=value pairs.
Verify connectivity to the database.
asadmin> ping-connection-pool Emp_Perks-Pool
Command ping-connection-pool executed successfully.
Exit the multimode session for the asadmin utility.
asadmin> exit
Command multimode executed successfully.
Use the create-jdbc-resource(1) subcommand to create the JDBC resource, making sure to name it so that the perk-olator application can discover it using JNDI lookup.
On dashost.example.com, create the JDBC resource and target it to the pmdcluster cluster.
dashost$ asadmin create-jdbc-resource --connectionpoolid Emp_Perks-Pool --target pmdcluster jdbc/emp_perks JDBC resource jdbc/emp_perks created successfully. pmd-i1: JDBC resource jdbc/emp_perks created successfully. pmd-i2: JDBC resource jdbc/emp_perks created successfully. Command create-jdbc-resource executed successfully.
After creating the Oracle data source for the perk-olator application, you need to deploy the application itself. Then, as the application is used over time, you can set a variety of JDBC connection pool features to optimize performance. For information about these features, see "Configuring Specific JDBC Connection Pool Features" in Oracle GlassFish Server Administration Guide.
As described in "Certificates and SSL" in Oracle GlassFish Server Security Guide, Secure Sockets Layer (SSL) is the most popular standard for securing Internet communications and transactions. Secure web applications use HTTPS (HTTP over SSL). The HTTPS protocol uses certificates to ensure confidential and secure communications between server and clients. The newest version of the SSL standard is called Transport Layer Security (TLS). GlassFish Server supports the SSL 3.0 and the TLS 1.0 encryption protocols.
The following procedure lists the major tasks for configuring GlassFish Server for TLS/SSL. The procedure also provides cross-references to detailed instructions for performing each task.
Set up the keystore and truststore for a domain.
By default, the keystore (keystore.jks) and truststore (cacerts.jks) for a domain are created in the domain-dir/config directory when you create the domain. The domain creation process creates a primary (private) key and a self-signed certificate for the DAS, and a separate private key and self-signed certificate for remote instances.
When you create a domain you can use the create-domain(1) subcommand --keytooloptions to specify the common name (CN) of the host that is to be used for the self-signed certificate. By default, the name is the fully-qualified name of the host where you run the create-domain subcommand.
GlassFish Server generates self-signed certificates suitable for internal testing. The self-signed certificates that GlassFish Server generates are typically not trusted by clients by default because a certificate authority does not vouch for the authenticity of the certificate. For example, browsers will warn you, let you view the certificate, and ask you to reject the certificate, accept it once, or accept it indefinitely.
You can use your tool of choice, such as keytool, to list the default self-signed certificates in the keystore, similar to the following:
Note:
You can list some limited contents of the keystore without supplying a password. However, for a request that affects the private key, such as the keytool.exe --certreq option, the keystore password is required.
keytool.exe -list -v -keystore keystore.jks
Enter keystore password:
Keystore type: JKS
Keystore provider: SUN
Your keystore contains 2 entries
Alias name: glassfish-instance
Creation date: Apr 14, 2011
Entry type: PrivateKeyEntry
Certificate chain length: 1
Certificate[1]:
Owner: CN=system01.somedomain-instance, OU=GlassFish, O=Oracle Corporation,
L=Santa Clara, ST=California, C=US
Issuer: CN=system01.somedomain-instance, OU=GlassFish, O=Oracle Corporation,
L=Santa Clara, ST=California, C=US
Serial number: 4da74a98
Valid from: Thu Apr 14 15:27:20 EDT 2011 until: Sun Apr 11 15:27:20 EDT 2021
Certificate fingerprints:
MD5: 00:FA:CF:65:19:7B:B2:02:62:66:DE:68:7B:BA:AE:93
SHA1: 11:E2:06:54:84:B3:67:8C:2E:AD:B6:4C:E9:E1:B9:A0:07:A7:CE:B9
Signature algorithm name: SHA1withRSA
Version: 3
Extensions:
#1: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 5D 37 CB 75 70 B8 52 4B 91 C6 A7 D3 FB BF 22 3F ]7.up.RK......"?
0010: 5D AE D7 74 ]..t
]
]
*******************************************
*******************************************
Alias name: s1as
Creation date: Apr 14, 2011
Entry type: PrivateKeyEntry
Certificate chain length: 1
Certificate[1]:
Owner: CN=system01.somedomain, OU=GlassFish, O=Oracle Corporation, L=Santa C
lara, ST=California, C=US
Issuer: CN=system01.somedomain, OU=GlassFish, O=Oracle Corporation, L=Santa
Clara, ST=California, C=US
Serial number: 4da74a94
Valid from: Thu Apr 14 15:27:16 EDT 2011 until: Sun Apr 11 15:27:16 EDT 2021
Certificate fingerprints:
MD5: 23:EA:3F:89:E6:34:31:21:C8:D6:47:88:30:05:3B:50
SHA1: 8B:9E:86:AE:E4:71:C4:8E:70:99:DB:3E:93:6C:BC:E3:DB:15:D1:B6
Signature algorithm name: SHA1withRSA
Version: 3
Extensions:
#1: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 87 BB 44 61 54 3C 09 15 8C 4F 1E 13 8B 37 46 AB ..DaT<...O...7F.
0010: 66 27 F9 A2 f'..
]
]
You can instead have GlassFish Server use trusted certificates for this purpose by adding one or more valid certificates and CA root in the keystore and truststore, respectively. Oracle strongly recommends that you use certificates signed by an accepted CA in a production environment.
Keep the following points in mind:
If GlassFish Server uses self-signed certificates, you need to include them directly in the client-side truststore.
If GlassFish Server uses certificates that are signed using a CA, import the CA root certificate into the client's truststore.
If you use certificates other than the GlassFish Server defaults, take note of the alias names you use. You will need the alias names later in this procedure when you configure the HTTP Listener for SSL.
For more information on using your own certificates, see the following documentation:
"To Generate a Certificate by Using keytool" in Oracle GlassFish Server Security Guide
"To Sign a Certificate by Using keytool" in Oracle GlassFish Server Security Guide
Optionally, configure the client for two-way SSL.
With two-way SSL (SSL with client authentication), GlassFish Server presents a certificate to the client and the client presents a certificate to GlassFish Server.
In this case, you must ensure that GlassFish Server is able to validate the certificate that the client uses to digitally sign its request, and that GlassFish Server in turn uses to encrypt its responses to the client. Do one of the following:
Make sure the client uses a digital certificate that GlassFish Server automatically trusts because it has been issued by a trusted certificate authority.
Make sure the client uses an individual certificate that is already in the GlassFish Server keystore and therefore already trusted.
Create a Listener Port
See "To Create an Internet Connection" in Oracle GlassFish Server Administration Guide.
Note:
An HTTP listener, also known as a network listener, is a listen socket that has an Internet Protocol (IP) address, a port number, a server name, and a default virtual server. Each virtual server provides connections between the server and clients through one or more listeners.
Each HTTP listener has an associated HTTP protocol.
Ensure that the server is running.
Remote subcommands require a running server.
Create an HTTPS protocol by using the create-protocol(1) subcommand with the --securityenabled option.
(The listener named http-listener-2 has security (SSL) enabled by default. To use this built-in http-listener-2 HTTPS protocol, skip this step.)
See "To Create a Protocol" in Oracle GlassFish Server Administration Guide.
Create an HTTP configuration for this protocol by using the create-http(1) subcommand.
(If you used the built-in http-listener-2 HTTPS protocol, skip this step.)
See "To Create an HTTP Configuration" in Oracle GlassFish Server Administration Guide.
Optionally, create a transport by using the create-transport(1) subcommand.
To use the built-in tcp transport, skip this step. You generally do not need another transport in addition to the default tcp transport.
See "To Create a Transport" in Oracle GlassFish Server Administration Guide.
Optionally, create a thread pool by using the create-threadpool(1) subcommand.
To avoid using a thread pool, or to use the built-in http-thread-pool thread pool, skip this step.
For additional thread pool information, see "Administering Thread Pools" in Oracle GlassFish Server Administration Guide.
Create an HTTP listener by using the create-network-listener(1) subcommand.
Specify the previously chosen protocol, and optionally a transport and thread pool.
asadmin> create-network-listener --listenerport 7272 protocol http-listener-2 --enabled=true sampleListener Command create-network-listener executed successfully.
For more information, see "To Create an HTTP Network Listener" in Oracle GlassFish Server Administration Guide.
Configure the HTTP Listener for SSL
The create-ssl(1) subcommand creates and configures the SSL element in the selected HTTP listener, IIOP listener, or IIOP service to enable secure communication on that listener/service.
You use the create-ssl subcommand to specify SSL2, SSL3, TLS, to set cipher suites, to enable two-way (client-auth) SSL, and so forth. By default, SSL3 and TLS are enabled and all cipher suites are enabled.
If you enabled two-way SSL for the client, you must also enable it for GlassFish Server by setting the -clientauthenabled option.
You must specify the alias (--certname) of the certificate in this subcommand.
For example, this example enables the HTTP listener named sampleListener for SSL with client authentication enabled. The alias name s1as identifies the default GlassFish Server certificate.
asadmin> create-ssl --type http-listener --certname s1as --clientauthenabled sampleListener Command create-ssl executed successfully.
To activate your changes, restart GlassFish Server.
You can use the create-http-listener(1) subcommand to create a network listener configured for SSL that uses the HTTPS protocol without having to first create a protocol, transport, or HTTP con figuration. This subcommand is a convenient shortcut, but it gives access to only a limited number of options.
Set up the keystore and truststore for a domain.
Optionally, configure the client for two-way SSL.
Create an HTTP Network Listener with the create-http-listener subcommand
Ensure that the server is running.
Remote subcommands require a running server.
Run create-http-listener with the --securityenabled option.
If the --securityenabled options is set to true, the HTTP listener runs SSL. The security setting globally enables or disables SSL by making certificates available to the server instance. The default value is false.
For example:
asadmin> create-http-listener --listeneraddress 0.0.0.0 --listenerport 443 --securityenabled=true --enabled=true --default-virtual-server server sampleListener Command create-http-listener executed successfully.
You cannot use the create-http-listener subcommand to specify SSL2, SSL3, TLS, to set cipher suites, or to enable client authentication. Instead, when you set --securityenabled to true, both SSL3 are TLS are enabled, all cipher suites are chosen, and client authentication is not enabled. With the exception of the client authentication case, these defaults should be acceptable in most cases.
To change the defaults, you need to explicitly set these elements. For example:
asadmin> get configs.config.server-config.network-con fig.protocols.protocol.sampleListener.ssl.client-auth-enabled configs.config.server-config.network-config.protocols.protocol.sampleListener.ss l.client-auth-enabled=false Command get executed successfully. asadmin> set configs.config.server-config.network-con fig.protocols.protocol.sampleListener.ssl.client-auth-enabled=true configs.config.server-config.network-config.protocols.protocol.sampleListener.ss l.client-auth-enabled=true Command set executed successfully.
For more information, see "To Create an HTTP Network Listener" in Oracle GlassFish Server Administration Guide.
To activate your changes, restart GlassFish Server.