 |  |
During a Google summer of Code project (GSoC) Maurus Rohner implemented an LDAP interface for OLAT. The following features are supported:
Bulk user import / synchronization from the LDAP directory both as one-time jobs or as a scheduled recurrent operation (configurable, can be disabled). Synchronizaton can also be started from the GUI.
On-the-fly user generation on first user login (alternative to configuration above)
Login and real-time authentication agains the LDAP directory
Caching of LDAP password to protect OLAT from tremporarily LDAP downtime (configurable, can be disabled)
Migrating of existing OLAT users with LDAP users (configurable, can be disabled)
Mapping of LDAP attributes to OLAT user properties (configurable)
Support for multiple LDAP bases to define which user groups shold be synchronized / are allowed to log in (configurable)
Support for various LDAP servers including Microsoft Active Directory or OpenLDAP
SSL support
The implementation does not cover group synchronization or LDAP group to OLAT group mappings. If you need such features, ask for commercial help, frentix GmbH who supervised and integrated the project into OLAT can develop it for you.
To enable LDAP login and user synchronization you mus edit the
following variables in the OLAT build.properties
file
Table 3.1. LDAP configuration parameters in build.properties
ldap.enable=true | Enable / disable LDAP support. |
ldap.ldapUrl=ldap://openldap.olattest.org:389 | The URL to your LDAP server, including port |
ldap.ldapSystemDN=cn=Administrator,dc=olattest,dc=org | System user: used for getting all users and connection testing |
ldap.ldapSystemPW=mySuperPassword | The LDAP password of the system user |
ldap.ldapBases=
ou=person,dc=olattest,dc=org | List of bases where to find users. To use multiple bases you must edit the config file manually |
ldap.sslEnabled = false | Enable SSL connection |
ldap.trustStoreLocation=/usr/lib/j2sdk1.5-sun/jre/lib/security/cacerts | Location of the Java trust store |
ldap.trustStorePwd=changeit | The Java trust store password |
ldap.trustStoreType=JKS | The Java trust store type |
ldap.cacheLDAPPwdAsOLATPwdOnLogin=true | When users log in via LDAP, the system can keep a copy of
the password as encrypted hash in the database. This makes OLAT
more independent from an offline LDAP server and users can use
their LDAP password to use the WebDAV functionality. When setting
to true (recommended), make sure you configured
password.change.allowed=false |
ldap.convertExistingLocalUsersToLDAPUsers=true | When the system detects an LDAP user that does already exist in OLAT but is not marked as LDAP user, the OLAT user can be converted to an LDAP managed user. When enabling this feature you should make sure that you don't have a user 'administrator' in your ldapBases (not a problem but not recommended) |
ldap.deleteRemovedLDAPUsersOnSync=false | Users that have been created vial LDAP sync but now can't be found on the LDAP anymore can be deleted automatically. If unsure, set to false and delete those users manually in the LDAP administration panel. |
ldap.deleteRemovedLDAPUsersPercentage=50
| Sanity check when deleteRemovedLDAPUsersOnSync is set to 'true': if more than the defined percentages of user accounts are not found on the LDAP server and thus recognized as to be deleted, the LDAP sync will not happen and require a manual triggering of the delete job from the admin interface. This should prevent accidential deletion of OLAT user because of temporary LDAP problems or user relocation on the LDAP side. Value= 0 (never delete) to 100 (always delete). |
ldap.ldapSyncOnStartup=true | Should users be created and synchronized automatically on startup? If you set this and the cron configuration to false, the users will be generated on-the-fly when they log in the first time. |
ldap.ldapSyncCronSync=true | Should users be created and synchronized periodically, not just during startup? If you set this and the startup configuration to false, the users will be generated on-the-fly when they log in the first time. |
ldap.ldapSyncCronSyncExpression=0 0 * * *
? | Set the rule how often the LDAP synchronization should take place. Default is every hour. For the cron syntax see quartz cron syntax documentation |
ldap.ldapUserObjectClass=person | Configuration for syncing user attributes during login or cron and batch sync. The user object class to use. |
ldap.ldapUserCreatedTimestampAttribute=createdTimestamp | The LDAP attribute that tells the creation date of the LDAP user. In active Directory this is typically "whenCreated", in OpenLDAP "createdTimestamp". If not available, use the same as for the last modified date. |
ldap.ldapUserLastModifiedTimestampAttribute=modifyTimestamp | The LDAP attribute that tells the creation date of the LDAP user. In active Directory this is typically "whenChanged", in OpenLDAP "modifiedTimestamp" |
ldap.attributename.useridentifyer=uid | Mapping of the LDAP user identifyer to an OLAT user. In Active Directory this is typically "sAMAccountName", in OpenLDAP "uid". |
ldap.attributename.email=mail | Mapping of the mandatory OLAT user properties. In this example the LDAP attribute "mail" will be mapped to the OLAT user property "email" |
ldap.attributename.firstName=givenName | Mapping of the mandatory OLAT user properties. In this example the LDAP attribute "givenName" will be mapped to the OLAT user property "firstname" |
ldap.attributename.lastName=sn | Mapping of the mandatory OLAT user properties. In this example the LDAP attribute "sn" will be mapped to the OLAT user property "lastName" |
olatprovider.enable=false | Disable the normal OLAT login screen. When you set
ldap.cacheLDAPPwdAsOLATPwdOnLogin=true, a fallback to
the normal OLAT login is made in case the LDAP server can not be
reached. You can set this variable also to true to have the OLAT
and the LDAP login screen available |
default.auth.provider=LDAP | Use the LDAP login screen as the default login screen. |
Now type:
ant config-all
ant restart tomcat. Have a look at the olat logfile to see if the
configuration was accepted. A common error is to use whitespace in the
configuration, e.g. ldap.ldapSystemPW=mySuperPassword is not
the same as ldap.ldapSystemPW = mySuperPassword...
Advanced LDAP configuration can be made in the LDAP spring config
file locate under
webapp/WEB-INF/src/serviceconfig/org/olat/ldap/_spring/olatextconfig.xml
reqAttrs: Define which OLAT user properties are
required to be available. Default is is the userid and email, but
you could define that the phone number is also mandatory.
userAttributeMapper: Define the mapping from LDAP user attributes to OLAT user properties. In the build.properties you can define the mapping only for the user ID, the email, first name and last name. But you can define any kind of attribute mapping, e.g the students organization or his phone number. Add a new line for each additional mapping.
staticUserProperties: Sometimes it is
handy to give all users that are synched via LDAP a special OLAT
user property so that you can later diffenentiate those users from
the ones you create manually in OLAT. Define a static user property
that is added to the OLAT users that are synced via LDAP
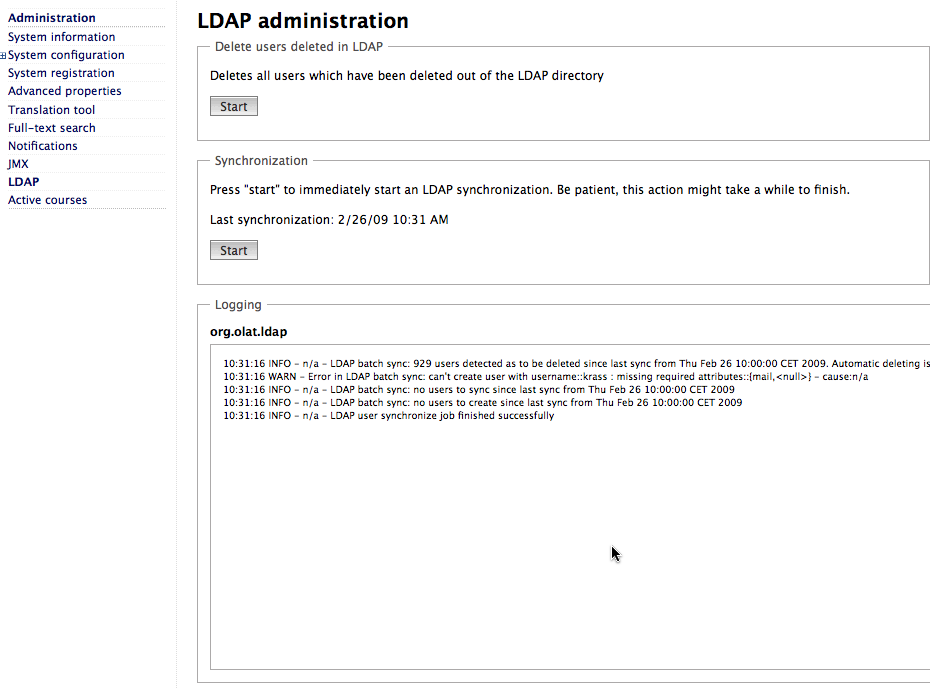
The LDAP module offers an administration GUI that lets you manually
synchronize LDAP users. The LDAP admin panel can be found under
Administration > LDAP.
To manually delete users in OLAT that do not exist on the LDAP server anymore, press the Start button in the section Delete users deleted in LDAP.
To manually create new and synchronize existing users in OLAT compared to the server, press the Start button in the section Synchronization.
At the bottom you see a logging panel that shows all logging messages regarding the LDAP module. For example, here you see that a certain user could not be synced from the LDAP server because a required attribute was missing.
To manually delete users in OLAT that do not exist on the LDAP server anymore, press the To manually delete users in OLAT that do not exist on the LDAP server anymore, press the Start button in the section Delete users deleted in LDAP.Start button in the section Delete users deleted in LDAP.