Certification authority (CA)¶
Public Key Infrastructure (PKI)¶
Zentyal uses OpenSSL [4] for the management of the Certification Authority and the life cycle of the certificates issued by it.
| [4] | http://www.openssl.org/ |
Certification Authority configuration with Zentyal¶
In Zentyal, the module Certification Authority is self-managed, which means that it does not need to be enabled in Module status but in order to start using this service, you should initialize the CA. The functionality in the module will not be available until you have carried out this action.
Go to Certification Authority ‣ General and you will find the form to create the CA. It is required to fill in the Organization Name and Days to expire fields. Optionally, it is possible to specify the Country code (a two-letter acronym following the ISO-3166-1 standard [5]), City and State.
When setting the expiration date you have to take into account that at the moment of expiration all certificates issued by this CA will be revoked, stopping all services depending on those certificates.
Once the CA has been initialized, you will be able to issue certificates. The required data are the Common Name of the certificate and the Days to expire. This last field is limited by the fact that no certificate can be valid for longer time than the CA. In case you are using the certificate for a service server such as a web server or mail server, the Common Name of the certificate should match the domain name of that server. For example, if you are using the domain name zentyal.home.lan to access the web administration interface in Zentyal, you will need a certificate with the same Common Name. In case you are setting a user certificate, the Common Name will usually be the user’s email address.
Optionally, you could set Alternative Subject Names [6] for the certificate. These are useful to set common names to a certificate: a domain name or an IP address for a HTTP virtual host or an email address to sign the email messages.
Once the certificate is issued, it will appear in the list of certificates and it will be available for the administrator and for the rest of modules. Through the certificate list you can perform several actions on the certificates:
- Download a the public key, private key and the certificate.
- Renew the certificate.
- Revoke the certificate.
- Reissue a previously revoked or expired certificate.
The downloadable package with the keys contains also a PKCS12 file with the private key and the certificate and it can be installed directly into other programs such as web browsers, mail clients, etc.
If you renew a certificate, the current one will be revoked and a new one with the new expiration date will be issued. And if you renew the CA, all certificates will be renewed with the new CA trying to keep the old expiration date. If this is not possible because it is after the date of expiry of the CA, then the date of expiration is set as the one of the CA.
If you revoke a certificate you won’t be able to use it anymore as this action is permanent and you can’t undo. Optionally you can select the reason of the certificate revocation:
- unspecified: reason non specified,
- keyCompromise: the private key has been compromised,
- CACompromise: the private key for the certification authority has been compromised,
- affilliationChanged: The issued certificate has changed its affiliation to another certification authority from other organization,
- superseded: the certificate has been renewed and it is now replaced by a new one,
- cessationOfOperation: the certification authority has ceased its operations,
- certificateHold: certified suspended,
- removeFromCRL: currently unimplemented, it provides delta CRLs support, that is, lists of certificates whose revoked status has changed.
When a certificate expires all the modules are notified. The expiration date of each certificate is automatically checked once a day and every time you access the certificate list page.
| [5] | http://en.wikipedia.org/wiki/ISO_3166-1 |
| [6] | For more information about subject alternative names, visit http://www.openssl.org/docs/apps/x509v3_config.html#Subject_Alternative_Name |
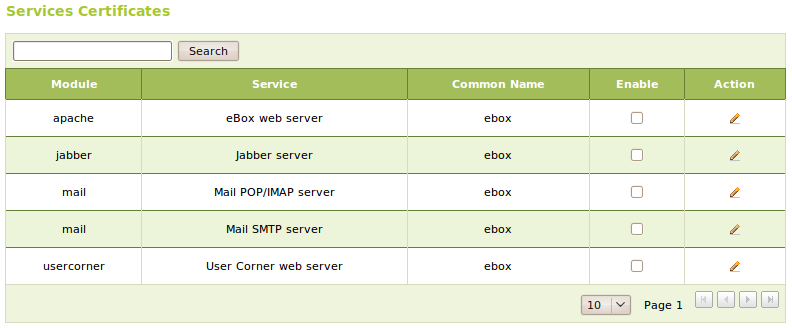
Services Certificates¶
On Certification Authority ‣ Services Certificates we can find the list of Zentyal modules using certificates for their operation. Each module generates its own self-signed certificates, but you can replace them with others issued by your CA.
You can generate a certificate for each service by defining its Common Name. If there does not exist previously a certificate with such name, the CA will create it automatically.
Once activated, you need to restart the service to force the module using the new certificate. This also applies if you renew a certificate for a module.