 |  |  |  |  |
This section describes how to configure the HTTP transport to use SSL/TLS security, a combination usually referred to as HTTPS. In FUSE Services Framework, HTTPS security is configured by specifying settings in XML configuration files.
The following topics are discussed in this chapter:
A basic prerequisite for using SSL/TLS security is to have a collection of X.509 certificates available to identify your server applications and, optionally, to identify your client applications. You can generate X.509 certificates in one of the following ways:
Use a commercial third-party to tool to generate and manage your X.509 certificates.
Use the free openssl utility (which can be downloaded from http://www.openssl.org) and the Java keystore utility to generate certificates (see Use the CA to Create Signed Certificates in a Java Keystore).
![[Note]](imagesdb/note.gif) | Note |
|---|---|
The HTTPS protocol mandates a URL integrity check, which requires a certificate’s identity to match the hostname on which the server is deployed. See Special Requirements on HTTPS Certificates for details. |
In the Java runtime, you must deploy X.509 certificate chains and trusted CA certificates in the form of Java keystores. See Configuring HTTPS for details.
A prerequisite for enabling HTTPS on a WSDL endpoint is that the endpoint address must be specified as a HTTPS URL. There are two different locations where the endpoint address is set and both must be modified to use a HTTPS URL:
HTTPS specified in the WSDL contract—you must specify the endpoint
address in the WSDL contract to be a URL with the https: prefix, as
shown in Example 1.1.
Example 1.1. Specifying HTTPS in the WSDL
<wsdl:definitions name="HelloWorld"
targetNamespace="http://apache.org/hello_world_soap_http"
xmlns:soap="http://schemas.xmlsoap.org/wsdl/soap/"
xmlns:wsdl="http://schemas.xmlsoap.org/wsdl/" ... >
...
<wsdl:service name="SOAPService">
<wsdl:port binding="tns:Greeter_SOAPBinding"
name="SoapPort">
<soap:address location="https://localhost:9001/SoapContext/SoapPort"/>
</wsdl:port>
</wsdl:service>
</wsdl:definitions>Where the location attribute of the soap:address element is configured to use a HTTPS URL.
For bindings other than SOAP, you edit the URL appearing in the location attribute of the http:address element.
HTTPS specified in the server code—you must ensure that the URL
published in the server code by calling
Endpoint.publish() is defined with a
https: prefix, as shown in Example 1.2.
Example 1.2. Specifying HTTPS in the Server Code
// Java
package demo.hw_https.server;
import javax.xml.ws.Endpoint;
public class Server {
protected Server() throws Exception {
Object implementor = new GreeterImpl();
String address = "https://localhost:9001/SoapContext/SoapPort";
Endpoint.publish(address, implementor);
}
...
}For example, consider the configuration for a secure HTTPS client with no certificate, as shown in Example 1.3.
Example 1.3. Sample HTTPS Client with No Certificate
<?xml version="1.0" encoding="UTF-8"?>
<beans xmlns="http://www.springframework.org/schema/beans"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns:sec="http://cxf.apache.org/configuration/security"
xmlns:http="http://cxf.apache.org/transports/http/configuration"
xmlns:jaxws="http://java.sun.com/xml/ns/jaxws"
xsi:schemaLocation="...">
 <http:conduit name="{http://apache.org/hello_world_soap_http}SoapPort.http-conduit">
<http:conduit name="{http://apache.org/hello_world_soap_http}SoapPort.http-conduit">
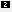 <http:tlsClientParameters>
<http:tlsClientParameters>
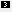 <sec:trustManagers>
<sec:keyStore type="JKS" password="password"
file="certs/truststore.jks"/>
</sec:trustManagers>
<sec:trustManagers>
<sec:keyStore type="JKS" password="password"
file="certs/truststore.jks"/>
</sec:trustManagers>
 <sec:cipherSuitesFilter>
<sec:include>.*_WITH_3DES_.*</sec:include>
<sec:include>.*_WITH_DES_.*</sec:include>
<sec:exclude>.*_WITH_NULL_.*</sec:exclude>
<sec:exclude>.*_DH_anon_.*</sec:exclude>
</sec:cipherSuitesFilter>
</http:tlsClientParameters>
</http:conduit>
</beans>
<sec:cipherSuitesFilter>
<sec:include>.*_WITH_3DES_.*</sec:include>
<sec:include>.*_WITH_DES_.*</sec:include>
<sec:exclude>.*_WITH_NULL_.*</sec:exclude>
<sec:exclude>.*_DH_anon_.*</sec:exclude>
</sec:cipherSuitesFilter>
</http:tlsClientParameters>
</http:conduit>
</beans>The preceding client configuration is described as follows:
The TLS security settings are defined on a specific WSDL port. In this
example, the WSDL port being configured has the QName,
| ||||
The | ||||
The The
| ||||
The |
Consider a secure HTTPS client that is configured to have its own certificate. Example 1.4 shows how to configure such a sample client.
Example 1.4. Sample HTTPS Client with Certificate
<?xml version="1.0" encoding="UTF-8"?>
<beans xmlns="http://www.springframework.org/schema/beans"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns:sec="http://cxf.apache.org/configuration/security"
xmlns:http="http://cxf.apache.org/transports/http/configuration"
xmlns:jaxws="http://java.sun.com/xml/ns/jaxws"
xsi:schemaLocation="...">
<http:conduit name="{http://apache.org/hello_world_soap_http}SoapPort.http-conduit">
<http:tlsClientParameters>
<sec:trustManagers>
<sec:keyStore type="JKS" password="password"
file="certs/truststore.jks"/>
</sec:trustManagers>
 <sec:keyManagers keyPassword="password">
<sec:keyManagers keyPassword="password">
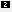 <sec:keyStore type="JKS" password="password"
file="certs/wibble.jks"/>
</sec:keyManagers>
<sec:cipherSuitesFilter>
<sec:include>.*_WITH_3DES_.*</sec:include>
<sec:include>.*_WITH_DES_.*</sec:include>
<sec:exclude>.*_WITH_NULL_.*</sec:exclude>
<sec:exclude>.*_DH_anon_.*</sec:exclude>
</sec:cipherSuitesFilter>
</http:tlsClientParameters>
</http:conduit>
<bean id="cxf" class="org.apache.cxf.bus.CXFBusImpl"/>
</beans>
<sec:keyStore type="JKS" password="password"
file="certs/wibble.jks"/>
</sec:keyManagers>
<sec:cipherSuitesFilter>
<sec:include>.*_WITH_3DES_.*</sec:include>
<sec:include>.*_WITH_DES_.*</sec:include>
<sec:exclude>.*_WITH_NULL_.*</sec:exclude>
<sec:exclude>.*_DH_anon_.*</sec:exclude>
</sec:cipherSuitesFilter>
</http:tlsClientParameters>
</http:conduit>
<bean id="cxf" class="org.apache.cxf.bus.CXFBusImpl"/>
</beans>The preceding client configuration is described as follows:
The | ||||
The The For details of how to create such a keystore file, see Use the CA to Create Signed Certificates in a Java Keystore.
|
Consider a secure HTTPS server that requires clients to present an X.509 certificate. Example 1.5 shows how to configure such a server.
Example 1.5. Sample HTTPS Server Configuration
<?xml version="1.0" encoding="UTF-8"?> <beans xmlns="http://www.springframework.org/schema/beans" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:sec="http://cxf.apache.org/configuration/security" xmlns:http="http://cxf.apache.org/transports/http/configuration" xmlns:httpj="http://cxf.apache.org/transports/http-jetty/configuration" xmlns:jaxws="http://java.sun.com/xml/ns/jaxws" xsi:schemaLocation="..."> <httpj:engine-factory bus="cxf"><httpj:engine port="9001">
<httpj:tlsServerParameters>
<sec:keyManagers keyPassword="password">
<sec:keyStore type="JKS" password="password" file="certs/cherry.jks"/> </sec:keyManagers>
<sec:trustManagers> <sec:keyStore type="JKS" password="password" file="certs/truststore.jks"/> </sec:trustManagers>
<sec:cipherSuitesFilter> <sec:include>.*_WITH_3DES_.*</sec:include> <sec:include>.*_WITH_DES_.*</sec:include> <sec:exclude>.*_WITH_NULL_.*</sec:exclude> <sec:exclude>.*_DH_anon_.*</sec:exclude> </sec:cipherSuitesFilter>
<sec:clientAuthentication want="true" required="true"/> </httpj:tlsServerParameters> </httpj:engine> </httpj:engine-factory> <!-- We need a bean named "cxf" --> <bean id="cxf" class="org.apache.cxf.bus.CXFBusImpl"/> </beans>
The preceding server configuration is described as follows:
On the server side, TLS is not configured for each WSDL
port. Instead of configuring each WSDL port, the TLS security settings are
applied to a specific IP port, which is
| ||||
The | ||||
The | ||||
The The
For details of how to create such a keystore file, see Use the CA to Create Signed Certificates in a Java Keystore. | ||||
The The
| ||||
The | ||||
The
|