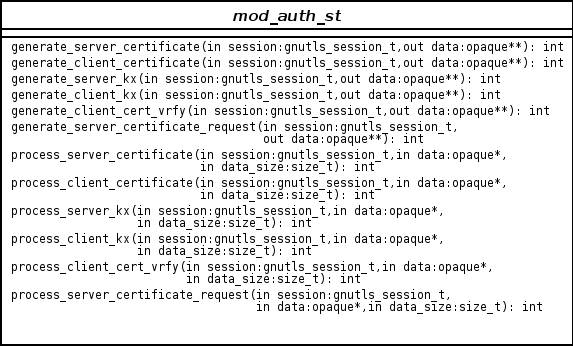
In GnuTLS authentication methods can be implemented quite easily. Since the required changes to add a new authentication method affect only the handshake protocol, a simple interface is used. An authentication method needs only to implement the functions as seen in the figure below.

The functions that need to be implemented are the ones responsible for
interpreting the handshake protocol messages. It is common for such
functions to read data from one or more credentials_t
structures1 and write data,
such as certificates, usernames etc. to auth_info_t structures.
Simple examples of existing authentication methods can be seen in
auth_psk.c for PSK ciphersuites and auth_srp.c for SRP
ciphersuites. After implementing these functions the structure holding
its pointers has to be registered in gnutls_algorithms.c in the
_gnutls_kx_algorithms structure.