To capitalize on the capabilities of HDFS data at rest encryption, you will need two separate types of HDFS administrative accounts:
HDFS administrative user: an account in the
hdfssupergroup that is used to manage encryption keys and encryption zones. Examples in this chapter use an administrative user account namedencr.HDFS service user: the system-level account traditionally associated with HDFS. By default this is user
hdfsin HDP. This account owns the HDFS DataNode and NameNode processes.![[Important]](../common/images/admon/important.png)
Important This is a system-only account. Physical users should not be given access to this account.
Complete the following steps to create a new HDFS administrative user.
Note: These steps use sample values for group
(operator) and user account (opt1).
Create a new group called
operator.Add a new user (for example,
opt1) to the group.Add principal
[email protected]and create a keytab.Login as
opt1, and do akinitoperation.In Ambari, add
operatortodfs.permissions.superusergroup.In Ambari, add
hdfs, operatortodfs.cluster.administrators: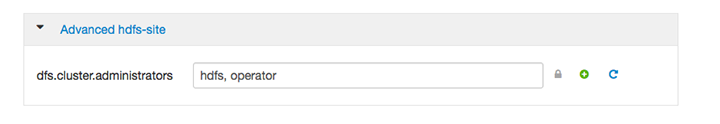
Add
opt1to the KMS blacklist. Set the corresponding property in Ambari:hadoop.kms.blacklist.DECRYPT_EEK=opt1Restart HDFS.
Validation
Make sure the opt1 account has HDFS administrative access:
hdfs dfsadmin -report
Make sure the opt1 account cannot access encrypted files. For
example, if /data/test/file.txt is in an encryption zone, the
following command should return an error:
hdfs dfs -cat /data/test/file.txt
Additional Administrative User Accounts
If you plan to use HDFS data at rest encryption with YARN, we recommend that you create a separate administrative user account for YARN administration.
If you plan to use HDFS data at rest encryption with Oozie, refer to the Oozie section of this chapter.