- 14.1. Overview
- 14.2. Establishing an Ethernet Connection
- 14.3. Establishing an ISDN Connection
- 14.4. Establishing a Modem Connection
- 14.5. Establishing an xDSL Connection
- 14.6. Establishing a Token Ring Connection
- 14.7. Establishing a Wireless Connection
- 14.8. Managing DNS Settings
- 14.9. Managing Hosts
- 14.10. Working with Profiles
- 14.11. Device Aliases
- 14.12. Saving and Restoring the Network Configuration
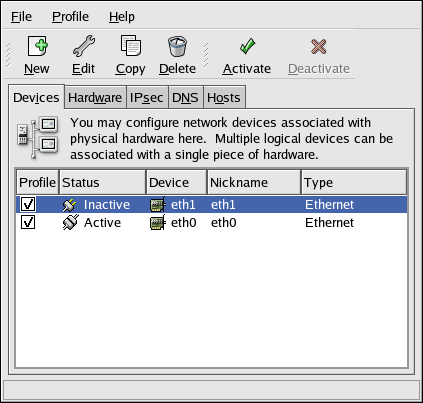
To communicate with each other, computers must have a network connection. This is accomplished by having the operating system recognize an interface card (such as Ethernet, ISDN modem, or token ring) and configuring the interface to connect to the network.
The Network Administration Tool can be used to configure the following types of network interfaces:
-
Ethernet
-
ISDN
-
modem
-
xDSL
-
token ring
-
CIPE
-
wireless devices
It can also be used to configure IPsec connections, manage DNS settings, and manage the /etc/hosts file used to store additional hostnames and IP address combinations.
To use the Network Administration Tool, you must have root privileges. To start the application, go to the Applications (the main menu on the panel) => System Settings => Network, or type the command system-config-network at a shell prompt (for example, in an XTerm or a GNOME terminal). If you type the command, the graphical version is displayed if X is running; otherwise, the text-based version is displayed.
To use the command line version, execute the command system-config-network-cmd --help as root to view all of the options.
Tip
Use the Red Hat Hardware Compatibility List (http://hardware.redhat.com/hcl/) to determine if Red Hat Enterprise Linux supports your hardware device.
To configure a network connection with the Network Administration Tool, perform the following steps:
-
Add a network device associated with the physical hardware device.
-
Add the physical hardware device to the hardware list, if it does not already exist.
-
Configure the hostname and DNS settings.
-
Configure any hosts that cannot be looked up through DNS.
This chapter discusses each of these steps for each type of network connection.