

Edition 1.6
Copyright © 2010 Red Hat, Inc.
1801 Varsity Drive
Raleigh, NC 27606-2072 USA
Phone: +1 919 754 3700
Phone: 888 733 4281
Fax: +1 919 754 3701
Mono-spaced Bold
To see the contents of the filemy_next_bestselling_novelin your current working directory, enter thecat my_next_bestselling_novelcommand at the shell prompt and press Enter to execute the command.
Press Enter to execute the command.Press Ctrl+Alt+F2 to switch to the first virtual terminal. Press Ctrl+Alt+F1 to return to your X-Windows session.
mono-spaced bold. For example:
File-related classes includefilesystemfor file systems,filefor files, anddirfor directories. Each class has its own associated set of permissions.
Choose → → from the main menu bar to launch Mouse Preferences. In the Buttons tab, click the Left-handed mouse check box and click to switch the primary mouse button from the left to the right (making the mouse suitable for use in the left hand).To insert a special character into a gedit file, choose → → from the main menu bar. Next, choose → from the Character Map menu bar, type the name of the character in the Search field and click . The character you sought will be highlighted in the Character Table. Double-click this highlighted character to place it in the Text to copy field and then click the button. Now switch back to your document and choose → from the gedit menu bar.
Mono-spaced Bold ItalicProportional Bold Italic
To connect to a remote machine using ssh, typesshat a shell prompt. If the remote machine isusername@domain.nameexample.comand your username on that machine is john, typessh [email protected].Themount -o remountcommand remounts the named file system. For example, to remount thefile-system/homefile system, the command ismount -o remount /home.To see the version of a currently installed package, use therpm -qcommand. It will return a result as follows:package.package-version-release
Publican is a DocBook publishing system.
mono-spaced roman and presented thus:
books Desktop documentation drafts mss photos stuff svn books_tests Desktop1 downloads images notes scripts svgs
mono-spaced roman but add syntax highlighting as follows:
package org.jboss.book.jca.ex1; import javax.naming.InitialContext; public class ExClient { public static void main(String args[]) throws Exception { InitialContext iniCtx = new InitialContext(); Object ref = iniCtx.lookup("EchoBean"); EchoHome home = (EchoHome) ref; Echo echo = home.create(); System.out.println("Created Echo"); System.out.println("Echo.echo('Hello') = " + echo.echo("Hello")); } }
6.
ls -l command to view file permissions:
$ ls -l file1 -rwxrw-r-- 1 user1 group1 0 2010-01-29 09:17 file1
rwx, control the access rights that the Linux user1 user (in this case, the owner) has to file1. The next three permission bits, rw-, control the access rights that the Linux group1 group has to file1. The last three permission bits, r--, control the access rights that everyone else has to file1, which includes all users and processes.
ls -Z command:
$ ls -Z file1 -rwxrw-r-- user1 group1 unconfined_u:object_r:user_home_t:s0 file1
unconfined_u), a role (object_r), a type (user_home_t), and a level (s0) for the file1 file. This information is used to make access control decisions. This example also displays the DAC rules, which are shown in the SELinux context via the ls -Z command. SELinux policy rules are checked after DAC rules. SELinux policy rules are not applied if DAC rules deny access first.
[1] "Integrating Flexible Support for Security Policies into the Linux Operating System", by Peter Loscocco and Stephen Smalley. This paper was originally prepared for the National Security Agency and is, consequently, in the public domain. Refer to the original paper for details.
[2] "Meeting Critical Security Objectives with Security-Enhanced Linux", by Peter Loscocco and Stephen Smalley. This paper was originally prepared for the National Security Agency and is in the public domain. Refer to the original paper for details.
unconfined_t domain, and system processes started by init run in the initrc_t domain - both of these domains are unconfined.
semanage command, which is provided by the policycoreutils-python package. This command is discussed throughout this guide using detailed configuration examples.
root user and perform tasks for users, such as the passwd application, are confined. When a process is confined, it runs in its own domain, such as the httpd process running in the httpd_t domain. If a confined process is compromised by an attacker, depending on SELinux policy configuration, an attacker's access to resources and the possible damage they can do is limited.
httpd) from reading files that are not correctly labeled, such as files intended for use by Samba. This is an example, and should not be used in production. It assumes that the httpd, wget, setroubleshoot-server and audit packages are installed, that the SELinux targeted policy is used, and that SELinux is running in enforcing mode:
sestatus command to confirm that SELinux is enabled, is running in enforcing mode, and that targeted policy is being used:
$ /usr/sbin/sestatus SELinux status: enabled SELinuxfs mount: /selinux Current mode: enforcing Mode from config file: enforcing Policy version: 24 Policy from config file: targeted
SELinux status: enabled is returned when SELinux is enabled. Current mode: enforcing is returned when SELinux is running in enforcing mode. Policy from config file: targeted is returned when the SELinux targeted policy is used.
touch /var/www/html/testfile command to create a file.
ls -Z /var/www/html/testfile command to view the SELinux context:
-rw-r--r-- root root unconfined_u:object_r:httpd_sys_content_t:s0 /var/www/html/testfile
testfile file is labeled with the SELinux unconfined_u user because a Linux user that is mapped to the unconfined_u SELinux user created the file. Role-Based Access Control (RBAC) is used for processes, not files. Roles do not have a meaning for files - the object_r role is a generic role used for files (on persistent storage and network file systems). Under the /proc/ directory, files related to processes may use the system_r role.[3] The httpd_sys_content_t type allows the httpd process to access this file.
service httpd start command to start the httpd process. The output is as follows if httpd starts successfully:
# /sbin/service httpd start Starting httpd: [ OK ]
wget http://localhost/testfile command. Unless there are changes to the default configuration, this command succeeds:
--2009-12-01 11:40:28-- http://localhost/testfile Resolving localhost... 127.0.0.1 Connecting to localhost|127.0.0.1|:80... connected. HTTP request sent, awaiting response... 200 OK Length: 0 [text/plain] Saving to: `testfile' [ <=> ] 0 --.-K/s in 0s 2009-12-01 11:40:28 (0.00 B/s) - `testfile' saved [0/0]
chcon command relabels files; however, such label changes do not survive when the file system is relabeled. For permanent changes that survive a file system relabel, use the semanage command, which is discussed later. As the root user, run the following command to change the type to a type used by Samba:
chcon -t samba_share_t /var/www/html/testfile
ls -Z /var/www/html/testfile command to view the changes:
-rw-r--r-- root root unconfined_u:object_r:samba_share_t:s0 /var/www/html/testfile
httpd process access to testfile. Change into a directory where your Linux user has write access to, and run the wget http://localhost/testfile command. Unless there are changes to the default configuration, this command fails:
--2009-12-01 11:43:18-- http://localhost/testfile Resolving localhost... 127.0.0.1 Connecting to localhost|127.0.0.1|:80... connected. HTTP request sent, awaiting response... 403 Forbidden 2009-12-01 11:43:18 ERROR 403: Forbidden.
rm /var/www/html/testfile command to remove testfile.
httpd to be running, as the root user, run the service httpd stop command to stop httpd:
# /sbin/service httpd stop Stopping httpd: [ OK ]
httpd process access to testfile in step 5, but because the file was then labeled with a type that the httpd process does not have access to, SELinux denied access. After step 7, if the setroubleshoot-server package is installed, an error similar to the following is logged to /var/log/messages:
setroubleshoot: SELinux is preventing httpd (httpd_t) "getattr" to /var/www/html/testfile (samba_share_t). For complete SELinux messages run sealert -l c05911d3-e680-4e42-8e36-fe2ab9f8e654
/var/log/httpd/error_log:
[Tue Dec 01 11:43:18 2009] [error] [client 127.0.0.1] (13)Permission denied: access to /testfile denied
init programs run in the unconfined initrc_t domain, unconfined kernel processes run in the kernel_t domain, and unconfined Linux users run in the unconfined_t domain. For unconfined processes, SELinux policy rules are still applied, but policy rules exist that allow processes running in unconfined domains almost all access. Processes running in unconfined domains fall back to using DAC rules exclusively. If an unconfined process is compromised, SELinux does not prevent an attacker from gaining access to system resources and data, but of course, DAC rules are still used. SELinux is a security enhancement on top of DAC rules - it does not replace them.
httpd) can access data intended for use by Samba, when running unconfined. Note: in Red Hat Enterprise Linux, the httpd process runs in the confined httpd_t domain by default. This is an example, and should not be used in production. It assumes that the httpd and wget packages are installed, that SELinux targeted policy is used, and that SELinux is running in enforcing mode:
sestatus command to confirm that SELinux is enabled, is running in enforcing mode, and that targeted policy is being used:
$ /usr/sbin/sestatus SELinux status: enabled SELinuxfs mount: /selinux Current mode: enforcing Mode from config file: enforcing Policy version: 24 Policy from config file: targeted
SELinux status: enabled is returned when SELinux is enabled. Current mode: enforcing is returned when SELinux is running in enforcing mode. Policy from config file: targeted is returned when the SELinux targeted policy is used.
touch /var/www/html/test2file command to create a file.
ls -Z /var/www/html/test2file command to view the SELinux context:
-rw-r--r-- root root unconfined_u:object_r:httpd_sys_content_t:s0 /var/www/html/test2file
test2file is labeled with the SELinux unconfined_u user because a Linux user that is mapped to the unconfined_u SELinux user created the file. RBAC is used for processes, not files. Roles do not have a meaning for files - the object_r role is a generic role used for files (on persistent storage and network file systems). Under the /proc/ directory, files related to processes may use the system_r role.[4] The httpd_sys_content_t type allows the httpd process to access this file.
chcon command relabels files; however, such label changes do not survive when the file system is relabeled. For permanent changes that survive a file system relabel, use the semanage command, which is discussed later. As the root user, run the following command to change the type to a type used by Samba:
chcon -t samba_share_t /var/www/html/test2file
ls -Z /var/www/html/test2file command to view the changes:
-rw-r--r-- root root unconfined_u:object_r:samba_share_t:s0 /var/www/html/test2file
service httpd status command to confirm that the httpd process is not running:
$ /sbin/service httpd status httpd is stopped
service httpd stop command as the root user to stop the httpd process:
# /sbin/service httpd stop Stopping httpd: [ OK ]
httpd process run unconfined, run the following command as the root user to change the type of /usr/sbin/httpd, to a type that does not transition to a confined domain:
chcon -t unconfined_exec_t /usr/sbin/httpd
ls -Z /usr/sbin/httpd command to confirm that /usr/sbin/httpd is labeled with the unconfined_exec_t type:
-rwxr-xr-x root root system_u:object_r:unconfined_exec_t /usr/sbin/httpd
service httpd start command to start the httpd process. The output is as follows if httpd starts successfully:
# /sbin/service httpd start Starting httpd: [ OK ]
ps -eZ | grep httpd command to view the httpd processes running in the unconfined_t domain:
$ ps -eZ | grep httpd unconfined_u:system_r:unconfined_t7721? 00:00:00 httpd unconfined_u:system_r:unconfined_t7723? 00:00:00 httpd unconfined_u:system_r:unconfined_t7724? 00:00:00 httpd unconfined_u:system_r:unconfined_t7725? 00:00:00 httpd unconfined_u:system_r:unconfined_t7726? 00:00:00 httpd unconfined_u:system_r:unconfined_t7727? 00:00:00 httpd unconfined_u:system_r:unconfined_t7728? 00:00:00 httpd unconfined_u:system_r:unconfined_t7729? 00:00:00 httpd unconfined_u:system_r:unconfined_t7730? 00:00:00 httpd
wget http://localhost/test2file command. Unless there are changes to the default configuration, this command succeeds:
--2009-12-01 11:55:47-- http://localhost/test2file Resolving localhost... 127.0.0.1 Connecting to localhost|127.0.0.1|:80... connected. HTTP request sent, awaiting response... 200 OK Length: 0 [text/plain] Saving to: `test2file.1' [ <=> ]--.-K/s in 0s 2009-12-01 11:55:47 (0.00 B/s) - `test2file.1' saved [0/0]
httpd process does not have access to files labeled with the samba_share_t type, httpd is running in the unconfined unconfined_t domain, and falls back to using DAC rules, and as such, the wget command succeeds. Had httpd been running in the confined httpd_t domain, the wget command would have failed.
restorecon command restores the default SELinux context for files. As the root user, run the restorecon -v /usr/sbin/httpd command to restore the default SELinux context for /usr/sbin/httpd:
# /sbin/restorecon -v /usr/sbin/httpd restorecon reset /usr/sbin/httpd context system_u:object_r:unconfined_exec_t:s0->system_u:object_r:httpd_exec_t:s0
ls -Z /usr/sbin/httpd command to confirm that /usr/sbin/httpd is labeled with the httpd_exec_t type:
$ ls -Z /usr/sbin/httpd -rwxr-xr-x root root system_u:object_r:httpd_exec_t /usr/sbin/httpd
/sbin/service httpd restart command to restart httpd. After restarting, run the ps -eZ | grep httpd to confirm that httpd is running in the confined httpd_t domain:
# /sbin/service httpd restart Stopping httpd: [ OK ] Starting httpd: [ OK ] # ps -eZ | grep httpd unconfined_u:system_r:httpd_t 8880 ? 00:00:00 httpd unconfined_u:system_r:httpd_t 8882 ? 00:00:00 httpd unconfined_u:system_r:httpd_t 8883 ? 00:00:00 httpd unconfined_u:system_r:httpd_t 8884 ? 00:00:00 httpd unconfined_u:system_r:httpd_t 8885 ? 00:00:00 httpd unconfined_u:system_r:httpd_t 8886 ? 00:00:00 httpd unconfined_u:system_r:httpd_t 8887 ? 00:00:00 httpd unconfined_u:system_r:httpd_t 8888 ? 00:00:00 httpd unconfined_u:system_r:httpd_t 8889 ? 00:00:00 httpd
rm /var/www/html/test2file command to remove test2file.
httpd to be running, as the root user, run the service httpd stop command to stop httpd:
# /sbin/service httpd stop Stopping httpd: [ OK ]
rpm -q httpd to see if the httpd package is installed. If it is not installed and you want to use the Apache HTTP Server, run the following command as the root user to install it:
yum install httpd
httpd) runs confined by default. Confined processes run in their own domains, and are separated from other confined processes. If a confined process is compromised by an attacker, depending on SELinux policy configuration, an attacker's access to resources and the possible damage they can do is limited. The following example demonstrates the httpd processes running in their own domain. This example assumes the httpd, setroubleshoot, setroubleshoot-server and policycoreutils-python packages are installed:
getenforce to confirm SELinux is running in enforcing mode:
$ getenforce Enforcing
getenforce command returns Enforcing when SELinux is running in enforcing mode.
service httpd start as the root user to start httpd:
# service httpd start Starting httpd: [ OK ]
ps -eZ | grep httpd to view the httpd processes:
$ ps -eZ | grep httpd unconfined_u:system_r:httpd_t:s02850? 00:00:00 httpd unconfined_u:system_r:httpd_t:s02852? 00:00:00 httpd unconfined_u:system_r:httpd_t:s02853? 00:00:00 httpd unconfined_u:system_r:httpd_t:s02854? 00:00:00 httpd unconfined_u:system_r:httpd_t:s02855? 00:00:00 httpd unconfined_u:system_r:httpd_t:s02856? 00:00:00 httpd unconfined_u:system_r:httpd_t:s02857? 00:00:00 httpd unconfined_u:system_r:httpd_t:s02858? 00:00:00 httpd unconfined_u:system_r:httpd_t:s02859? 00:00:00 httpd
httpd processes is unconfined_u:system_r:httpd_t:s0. The second last part of the context, httpd_t, is the type. A type defines a domain for processes and a type for files. In this case, the httpd processes are running in the httpd_t domain.
httpd_t) interact with files, other processes, and the system in general. Files must be labeled correctly to allow httpd access to them. For example, httpd can read files labeled with the httpd_sys_content_t type, but can not write to them, even if Linux (DAC) permissions allow write access. Booleans must be turned on to allow certain behavior, such as allowing scripts network access, allowing httpd access to NFS and CIFS file systems, and httpd being allowed to execute Common Gateway Interface (CGI) scripts.
/etc/httpd/conf/httpd.conf is configured so httpd listens on a port other than TCP ports 80, 443, 488, 8008, 8009, or 8443, the semanage port command must be used to add the new port number to SELinux policy configuration. The following example demonstrates configuring httpd to listen on a port that is not already defined in SELinux policy configuration for httpd, and, as a consequence, httpd failing to start. This example also demonstrates how to then configure the SELinux system to allow httpd to successfully listen on a non-standard port that is not already defined in the policy. This example assumes the httpd package is installed. Run each command in the example as the root user:
service httpd status to confirm httpd is not running:
# service httpd status httpd is stopped
service httpd stop to stop the process:
# service httpd stop Stopping httpd: [ OK ]
semanage port -l | grep -w http_port_t to view the ports SELinux allows httpd to listen on:
# semanage port -l | grep -w http_port_t http_port_t tcp 80, 443, 488, 8008, 8009, 8443
/etc/httpd/conf/httpd.conf as the root user. Configure the Listen option so it lists a port that is not configured in SELinux policy configuration for httpd. In this example, httpd is configured to listen on port 12345:
# Change this to Listen on specific IP addresses as shown below to # prevent Apache from glomming onto all bound IP addresses (0.0.0.0) # #Listen 12.34.56.78:80 Listen 127.0.0.1:12345
service httpd start to start httpd:
# service httpd start Starting httpd: (13)Permission denied: make_sock: could not bind to address 127.0.0.1:12345 no listening sockets available, shutting down Unable to open logs [FAILED]
setroubleshoot: SELinux is preventing the httpd (httpd_t) from binding to port 12345. For complete SELinux messages. run sealert -l f18bca99-db64-4c16-9719-1db89f0d8c77
httpd to listen on port 12345, as used in this example, the following command is required:
# semanage port -a -t http_port_t -p tcp 12345
service httpd start again to start httpd and have it listen on the new port:
# service httpd start Starting httpd: [ OK ]
httpd to listen on a non-standard port (TCP 12345 in this example), httpd starts successfully on this port.
httpd is listening and communicating on TCP port 12345, open a telnet connection to the specified port and issue a HTTP GET command, as follows:
# telnet localhost 12345 Trying 127.0.0.1... Connected to localhost. Escape character is '^]'. GET / HTTP/1.0 HTTP/1.1 200 OK Date: Wed, 02 Dec 2009 14:36:34 GMT Server: Apache/2.2.13 (Red Hat) Accept-Ranges: bytes Content-Length: 3985 Content-Type: text/html; charset=UTF-8 [...continues...]
/var/www/html/ directory, and shows the file inheriting the httpd_sys_content_t type from its parent directory (/var/www/html/):
ls -dZ /var/www/html to view the SELinux context of /var/www/html/:
$ ls -dZ /var/www/html drwxr-xr-x root root system_u:object_r:httpd_sys_content_t:s0 /var/www/html
/var/www/html/ is labeled with the httpd_sys_content_t type.
touch /var/www/html/file1 as the root user to create a new file.
ls -Z /var/www/html/file1 to view the SELinux context:
$ ls -Z /var/www/html/file1 -rw-r--r-- root root unconfined_u:object_r:httpd_sys_content_t:s0 /var/www/html/file1
ls -Z command shows file1 labeled with the httpd_sys_content_t type. SELinux allows httpd to read files labeled with this type, but not write to them, even if Linux permissions allow write access. SELinux policy defines what types a process running in the httpd_t domain (where httpd runs) can read and write to. This helps prevent processes from accessing files intended for use by another process.
httpd can access files labeled with the httpd_sys_content_t type (intended for the Apache HTTP Server), but by default, can not access files labeled with the samba_share_t type (intended for Samba). Also, files in user home directories are labeled with the user_home_t type: by default, this prevents httpd from reading or writing to files in user home directories.
httpd. Different types allow you to configure flexible access:
httpd_sys_content_t.html files used by a static website. Files labeled with this type are accessible (read only) to httpd and scripts executed by httpd. By default, files and directories labeled with this type can not be written to or modified by httpd or other processes. Note: by default, files created in or copied into /var/www/html/ are labeled with the httpd_sys_content_t type.
httpd_sys_script_exec_thttpd to execute. This type is commonly used for Common Gateway Interface (CGI) scripts in /var/www/cgi-bin/. By default, SELinux policy prevents httpd from executing CGI scripts. To allow this, label the scripts with the httpd_sys_script_exec_t type and turn the httpd_enable_cgi Boolean on. Scripts labeled with httpd_sys_script_exec_t run in the httpd_sys_script_t domain when executed by httpd. The httpd_sys_script_t domain has access to other system domains, such as postgresql_t and mysqld_t.
httpd_sys_content_rw_thttpd_sys_script_exec_t type, but can not be modified by scripts labeled with any other type. You must use the httpd_sys_content_rw_t type to label files that will be read from and written to by scripts labeled with the httpd_sys_script_exec_t type.
httpd_sys_content_ra_thttpd_sys_script_exec_t type, but can not be modified by scripts labeled with any other type. You must use the httpd_sys_content_ra_t type to label files that will be read from and appended to by scripts labeled with the httpd_sys_script_exec_t type.
httpd_unconfined_script_exec_thttpd, or for the entire system.
grep httpd /etc/selinux/targeted/contexts/files/file_contexts
chcon command. Changes made with chcon do not survive a file system relabel or the restorecon command. SELinux policy controls whether users are able to modify the SELinux context for any given file. The following example demonstrates creating a new directory and an index.html file for use by httpd, and labeling that file and directory to allow httpd access to them:
mkdir -p /my/website as the root user to create a top-level directory structure to store files to be used by httpd.
default_t type. This type is inaccessible to confined services:
$ ls -dZ /my drwxr-xr-x root root unconfined_u:object_r:default_t:s0 /my
chcon -R -t httpd_sys_content_t /my/ as the root user to change the type of the /my/ directory and subdirectories, to a type accessible to httpd. Now, files created under /my/website/ inherit the httpd_sys_content_t type, rather than the default_t type, and are therefore accessible to httpd:
# chcon -R -t httpd_sys_content_t /my/ # touch /my/website/index.html # ls -Z /my/website/index.html -rw-r--r-- root root unconfined_u:object_r:httpd_sys_content_t:s0 /my/website/index.html
chcon.
semanage fcontext command (semanage is provided by the policycoreutils-python package) to make label changes that survive a relabel and the restorecon command. This command adds changes to file-context configuration. Then, run the restorecon command, which reads file-context configuration, to apply the label change. The following example demonstrates creating a new directory and an index.html file for use by httpd, and persistently changing the label of that directory and file to allow httpd access to them:
mkdir -p /my/website as the root user to create a top-level directory structure to store files to be used by httpd.
semanage fcontext -a -t httpd_sys_content_t "/my(/.*)?"
"/my(/.*)?" expression means the label change applies to the /my/ directory and all files and directories under it.
touch /my/website/index.html as the root user to create a new file.
restorecon -R -v /my/ as the root user to apply the label changes (restorecon reads file-context configuration, which was modified by the semanage command in step 2):
# restorecon -R -v /my/ restorecon reset /my context unconfined_u:object_r:default_t:s0->system_u:object_r:httpd_sys_content_t:s0 restorecon reset /my/website context unconfined_u:object_r:default_t:s0->system_u:object_r:httpd_sys_content_t:s0 restorecon reset /my/website/index.html context unconfined_u:object_r:default_t:s0->system_u:object_r:httpd_sys_content_t:s0
setsebool command. For example, to turn the allow_httpd_anon_write Boolean on, run the following command as the root user:
# setsebool -P allow_httpd_anon_write on
on to off in the command, as shown below:
# setsebool -P allow_httpd_anon_write off
-P option if you do not want setsebool changes to persist across reboots.
httpd is running:
allow_httpd_anon_writehttpd to only have read access to files labeled with the public_content_rw_t type. Enabling this Boolean will allow httpd to write to files labeled with the public_content_rw_t type, such as a public directory containing files for a public file transfer service.
allow_httpd_mod_auth_ntlm_winbindmod_auth_ntlm_winbind module in httpd.
allow_httpd_mod_auth_pammod_auth_pam module in httpd.
allow_httpd_sys_script_anon_writepublic_content_rw_t type, as used in a public file transfer service.
httpd_builtin_scriptinghttpd scripting. Having this Boolean enabled is often required for PHP content.
httpd_can_network_connecthttpd_can_network_connect_dbhttpd_can_network_relayhttpd is being used as a forward or reverse proxy.
httpd_can_sendmailhttpd. Turn this Boolean on to allow HTTP modules to send mail.
httpd_dbus_avahihttpd access to the avahi service via D-Bus. Turn this Boolean on to allow this access.
httpd_enable_cgihttpd from executing CGI scripts. Turn this Boolean on to allow httpd to execute CGI scripts (CGI scripts must be labeled with the httpd_sys_script_exec_t type).
httpd_enable_ftp_serverhttpd to listen on the FTP port and act as an FTP server.
httpd_enable_homedirshttpd from accessing user home directories. Turn this Boolean on to allow httpd access to user home directories; for example, content in /home/*/.
httpd_execmemhttpd to execute programs that require memory addresses that are both executable and writeable. Enabling this Boolean is not recommended from a security standpoint as it reduces protection against buffer overflows, however certain modules and applications (such as Java and Mono applications) require this privilege.
httpd_ssi_exechttpd_tty_commhttpd is allowed access to the controlling terminal. Usually this access is not required, however in cases such as configuring an SSL certificate file, terminal access is required to display and process a password prompt.
httpd_unifiedhttpd_t complete access to all of the httpd types (i.e. to execute, read, or write sys_content_t). When disabled, there is separation in place between web content that is read-only, writeable or executable. Disabling this Boolean ensures an extra level of security but adds the administrative overhead of having to individually label scripts and other web content based on the file access that each should have.
httpd_use_cifshttpd access to files on CIFS file systems that are labeled with the cifs_t type, such as file systems mounted via Samba.
httpd_use_nfshttpd access to files on NFS file systems that are labeled with the nfs_t type, such as file systems mounted via NFS.
.html files for that website with the httpd_sys_content_t type. By default, the Apache HTTP Server can not write to files that are labeled with the httpd_sys_content_t type. The following example creates a new directory to store files for a read-only website:
mkdir /mywebsite as the root user to create a top-level directory.
/mywebsite/index.html file. Copy and paste the following content into /mywebsite/index.html:
<html> <h2>index.html from /mywebsite/</h2> </html>
/mywebsite/, as well as files and subdirectories under it, label /mywebsite/ with the httpd_sys_content_t type. Run the following command as the root user to add the label change to file-context configuration:
# semanage fcontext -a -t httpd_sys_content_t "/mywebsite(/.*)?"
restorecon -R -v /mywebsite as the root user to make the label changes:
# restorecon -R -v /mywebsite restorecon reset /mywebsite context unconfined_u:object_r:default_t:s0->system_u:object_r:httpd_sys_content_t:s0 restorecon reset /mywebsite/index.html context unconfined_u:object_r:default_t:s0->system_u:object_r:httpd_sys_content_t:s0
/etc/httpd/conf/httpd.conf as the root user. Comment out the existing DocumentRoot option. Add a DocumentRoot "/mywebsite" option. After editing, these options should look as follows:
#DocumentRoot "/var/www/html" DocumentRoot "/mywebsite"
service httpd status as the root user to see the status of the Apache HTTP Server. If the server is stopped, run service httpd start as the root user to start it. If the server is running, run service httpd restart as the root user to restart the service (this also applies any changes made to httpd.conf).
http://localhost/index.html. The following is displayed:
index.html from /mywebsite/
nfs_t type. Also, by default, Samba shares mounted on the client side are labeled with a default context defined by policy. In common policies, this default context uses the cifs_t type.
nfs_t or cifs_t types. This may prevent file systems labeled with these types from being mounted and then read or exported by other services. Booleans can be turned on or off to control which services are allowed to access the nfs_t and cifs_t types.
httpd_use_nfs Boolean on to allow httpd to access and share NFS file systems (labeled with the nfs_t type. Run the setsebool command as the root user to turn the Boolean on:
setsebool -P httpd_use_nfs on
httpd_use_cifs Boolean on to allow httpd to access and share CIFS file systems (labeled with the cifs_t type. Run the setsebool command as the root user to turn the Boolean on:
setsebool -P httpd_use_cifs on
-P option if you do not want setsebool changes to persist across reboots.
httpd_sys_content_t type, which are intended for use by the Apache HTTP Server. Files can be shared between the Apache HTTP Server, FTP, rsync, and Samba, if the desired files are labeled with the public_content_t or public_content_rw_t type.
mkdir /shares as the root user to create a new top-level directory to share files between multiple services.
default_t type. This type is inaccessible to confined services:
$ ls -dZ /shares drwxr-xr-x root root unconfined_u:object_r:default_t:s0 /shares
/shares/index.html file. Copy and paste the following content into /shares/index.html:
<html> <body> <p>Hello</p> </body> </html>
/shares/ with the public_content_t type allows read-only access by the Apache HTTP Server, FTP, rsync, and Samba. Run the following command as the root user to add the label change to file-context configuration:
semanage fcontext -a -t public_content_t "/shares(/.*)?"
restorecon -R -v /shares/ as the root user to apply the label changes:
# restorecon -R -v /shares/ restorecon reset /shares context unconfined_u:object_r:default_t:s0->system_u:object_r:public_content_t:s0 restorecon reset /shares/index.html context unconfined_u:object_r:default_t:s0->system_u:object_r:public_content_t:s0
/shares/ through Samba:
rpm -q samba samba-common samba-client to confirm the samba, samba-common, and samba-client packages are installed (version numbers may differ):
$ rpm -q samba samba-common samba-client samba-3.4.0-0.41.el6.3.i686 samba-common-3.4.0-0.41.el6.3.i686 samba-client-3.4.0-0.41.el6.3.i686
yum install package-name as the root user.
/etc/samba/smb.conf as the root user. Add the following entry to the bottom of this file to share the /shares/ directory through Samba:
[shares] comment = Documents for Apache HTTP Server, FTP, rsync, and Samba path = /shares public = yes writeable = no
smbpasswd -a username as the root user to create a Samba account, where username is an existing Linux user. For example, smbpasswd -a testuser creates a Samba account for the Linux testuser user:
# smbpasswd -a testuser New SMB password:Enter a passwordRetype new SMB password:Enter the same password againAdded user testuser.
smbpasswd -a username, where username is the username of a Linux account that does not exist on the system, causes a Cannot locate Unix account for 'username'! error.
service smb start as the root user to start the Samba service:
service smb start Starting SMB services: [ OK ]
smbclient -U username -L localhost to list the available shares, where username is the Samba account added in step 3. When prompted for a password, enter the password assigned to the Samba account in step 3 (version numbers may differ):
$ smbclient -Uusername-L localhost Enterusername's password: Domain=[HOSTNAME] OS=[Unix] Server=[Samba 3.4.0-0.41.el6] Sharename Type Comment --------- ---- ------- shares Disk Documents for Apache HTTP Server, FTP, rsync, and Samba IPC$ IPC IPC Service (Samba Server Version 3.4.0-0.41.el6)usernameDisk Home Directories Domain=[HOSTNAME] OS=[Unix] Server=[Samba 3.4.0-0.41.el6] Server Comment --------- ------- Workgroup Master --------- -------
mkdir /test/ as the root user to create a new directory. This directory will be used to mount the shares Samba share.
shares Samba share to /test/, replacing username with the username from step 3:
mount //localhost/shares /test/ -o user=usernameusername, which was configured in step 3.
cat /test/index.html to view the file, which is being shared through Samba:
$ cat /test/index.html <html> <body> <p>Hello</p> </body> </html>
/shares/ through the Apache HTTP Server:
rpm -q httpd to confirm the httpd package is installed (version number may differ):
$ rpm -q httpd httpd-2.2.11-6.i386
yum install httpd as the root user to install it.
/var/www/html/ directory. Run the following command as the root user to create a link (named shares) to the /shares/ directory:
ln -s /shares/ shares
service httpd start as the root user to start the Apache HTTP Server:
service httpd start Starting httpd: [ OK ]
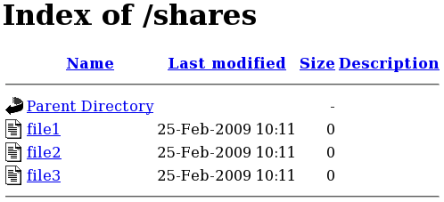
http://localhost/shares. The /shares/index.html file is displayed.
index.html file if it exists. If /shares/ did not have index.html, and instead had file1, file2, and file3, a directory listing would occur when accessing http://localhost/shares:
rm -i /shares/index.html as the root user to remove the index.html file.
touch /shares/file{1,2,3} as the root user to create three files in /shares/:
# touch /shares/file{1,2,3}
# ls -Z /shares/
-rw-r--r-- root root system_u:object_r:public_content_t:s0 file1
-rw-r--r-- root root unconfined_u:object_r:public_content_t:s0 file2
-rw-r--r-- root root unconfined_u:object_r:public_content_t:s0 file3
service httpd status as the root user to see the status of the Apache HTTP Server. If the server is stopped, run service httpd start as the root user to start it.
http://localhost/shares. A directory listing is displayed:
semanage port -l | grep -w "http_port_t" as the root user to list the ports SELinux allows httpd to listen on:
# semanage port -l | grep -w http_port_t http_port_t tcp 80, 443, 488, 8008, 8009, 8443
http to listen on TCP ports 80, 443, 488, 8008, 8009, or 8443. If /etc/httpd/conf/httpd.conf is configured so that httpd listens on any port not listed for http_port_t, httpd fails to start.
httpd to run on a port other than TCP ports 80, 443, 488, 8008, 8009, or 8443:
/etc/httpd/conf/httpd.conf as the root user so the Listen option lists a port that is not configured in SELinux policy for httpd. The following example configures httpd to listen on the 10.0.0.1 IP address, and on TCP port 12345:
# Change this to Listen on specific IP addresses as shown below to # prevent Apache from glomming onto all bound IP addresses (0.0.0.0) # #Listen 12.34.56.78:80 Listen 10.0.0.1:12345
semanage port -a -t http_port_t -p tcp 12345 as the root user to add the port to SELinux policy configuration.
semanage port -l | grep -w http_port_t as the root user to confirm the port is added:
# semanage port -l | grep -w http_port_t http_port_t tcp 12345, 80, 443, 488, 8008, 8009, 8443
httpd on port 12345, run semanage port -d -t http_port_t -p tcp 12345 as the root user to remove the port from policy configuration.
[5] From the "The Number One HTTP Server On The Internet" section of the Apache HTTP Server Project page: http://httpd.apache.org/. Copyright © 2009 The Apache Software Foundation. Accessed 7 July 2010.
rpm -q samba to see if the samba package is installed. If it is not installed and you want to use Samba, run the following command as the root user to install it:
yum install samba
smbd) runs confined by default. Confined services run in their own domains, and are separated from other confined services. The following example demonstrates the smbd process running in its own domain. This example assumes the samba package is installed:
getenforce to confirm SELinux is running in enforcing mode:
$ getenforce Enforcing
getenforce command returns Enforcing when SELinux is running in enforcing mode.
service smbd start as the root user to start smbd:
service smb start Starting SMB services: [ OK ]
ps -eZ | grep smb to view the smbd processes:
$ ps -eZ | grep smb unconfined_u:system_r:smbd_t:s016420? 00:00:00 smbd unconfined_u:system_r:smbd_t:s016422? 00:00:00 smbd
smbd processes is unconfined_u:system_r:smbd_t:s0. The second last part of the context, smbd_t, is the type. A type defines a domain for processes and a type for files. In this case, the smbd processes are running in the smbd_t domain.
smbd to access and share them. For example, smbd can read and write to files labeled with the samba_share_t type, but by default, can not access files labeled with the httpd_sys_content_t type, which is intended for use by the Apache HTTP Server. Booleans must be turned on to allow certain behavior, such as allowing home directories and NFS file systems to be exported through Samba, as well as to allow Samba to act as a domain controller.
samba_share_t type to allow Samba to share them. Only label files you have created, and do not relabel system files with the samba_share_t type: Booleans can be turned on to share such files and directories. SELinux allows Samba to write to files labeled with the samba_share_t type, as long as /etc/samba/smb.conf and Linux permissions are set accordingly.
samba_etc_t type is used on certain files in /etc/samba/, such as smb.conf. Do not manually label files with the samba_etc_t type. If files in /etc/samba/ are not labeled correctly, run restorecon -R -v /etc/samba as the root user to restore such files to their default contexts. If /etc/samba/smb.conf is not labeled with the samba_etc_t type, the service smb start command may fail and an SELinux denial may be logged. The following is an example denial when /etc/samba/smb.conf was labeled with the httpd_sys_content_t type:
setroubleshoot: SELinux is preventing smbd (smbd_t) "read" to ./smb.conf (httpd_sys_content_t). For complete SELinux messages. run sealert -l deb33473-1069-482b-bb50-e4cd05ab18af
allow_smbd_anon_writesmbd to write to a public directory, such as an area reserved for common files that otherwise has no special access restrictions.
samba_create_home_dirssamba_domain_controlleruseradd, groupadd and passwd.
samba_enable_home_dirssamba_export_all_rosamba_share_t type to be shared through Samba. When the samba_export_all_ro Boolean is on, but the samba_export_all_rw Boolean is off, write access to Samba shares is denied, even if write access is configured in /etc/samba/smb.conf, as well as Linux permissions allowing write access.
samba_export_all_rwsamba_share_t type to be exported through Samba. Permissions in /etc/samba/smb.conf and Linux permissions must be configured to allow write access.
samba_run_unconfinedsamba_share_fusefssamba_share_nfssmbd from having full access to NFS shares via Samba. Enabling this Boolean will allow Samba to share NFS file systems.
use_samba_home_dirsvirt_use_sambarpm -q samba samba-common samba-client to confirm the samba, samba-common, and samba-client packages are installed. If any of these packages are not installed, install them by running yum install package-name as the root user.
mkdir /myshare as the root user to create a new top-level directory to share files through Samba.
touch /myshare/file1 as the root user to create an empty file. This file is used later to verify the Samba share mounted correctly.
samba_share_t type, as long as /etc/samba/smb.conf and Linux permissions are set accordingly. Run the following command as the root user to add the label change to file-context configuration:
semanage fcontext -a -t samba_share_t "/myshare(/.*)?"
restorecon -R -v /myshare as the root user to apply the label changes:
# restorecon -R -v /myshare restorecon reset /myshare context unconfined_u:object_r:default_t:s0->system_u:object_r:samba_share_t:s0 restorecon reset /myshare/file1 context unconfined_u:object_r:default_t:s0->system_u:object_r:samba_share_t:s0
/etc/samba/smb.conf as the root user. Add the following to the bottom of this file to share the /myshare/ directory through Samba:
[myshare] comment = My share path = /myshare public = yes writeable = no
smbpasswd -a username as the root user to create a Samba account, where username is an existing Linux user. For example, smbpasswd -a testuser creates a Samba account for the Linux testuser user:
# smbpasswd -a testuser New SMB password:Enter a passwordRetype new SMB password:Enter the same password againAdded user testuser.
smbpasswd -a username, where username is the username of a Linux account that does not exist on the system, causes a Cannot locate Unix account for 'username'! error.
service smb start as the root user to start the Samba service:
service smb start Starting SMB services: [ OK ]
smbclient -U username -L localhost to list the available shares, where username is the Samba account added in step 7. When prompted for a password, enter the password assigned to the Samba account in step 7 (version numbers may differ):
$ smbclient -Uusername-L localhost Enterusername's password: Domain=[HOSTNAME] OS=[Unix] Server=[Samba 3.4.0-0.41.el6] Sharename Type Comment --------- ---- ------- myshare Disk My share IPC$ IPC IPC Service (Samba Server Version 3.4.0-0.41.el6)usernameDisk Home Directories Domain=[HOSTNAME] OS=[Unix] Server=[Samba 3.4.0-0.41.el6] Server Comment --------- ------- Workgroup Master --------- -------
mkdir /test/ as the root user to create a new directory. This directory will be used to mount the myshare Samba share.
myshare Samba share to /test/, replacing username with the username from step 7:
mount //localhost/myshare /test/ -o user=usernameusername, which was configured in step 7.
ls /test/ to view the file1 file created in step 3:
$ ls /test/ file1
samba_share_t type, for example, when wanting to share a website in /var/www/html/. For these cases, use the samba_export_all_ro Boolean to share any file or directory (regardless of the current label), allowing read only permissions, or the samba_export_all_rw Boolean to share any file or directory (regardless of the current label), allowing read and write permissions.
/var/www/html/, and then shares that file through Samba, allowing read and write permissions. This example assumes the httpd, samba, samba-common, samba-client, and wget packages are installed:
/var/www/html/file1.html file. Copy and paste the following content into /var/www/html/file1.html:
<html> <h2>File being shared through the Apache HTTP Server and Samba.</h2> </html>
ls -Z /var/www/html/file1.html to view the SELinux context of file1.html:
$ ls -Z /var/www/html/file1.html -rw-r--r--. root root unconfined_u:object_r:httpd_sys_content_t:s0 /var/www/html/file1.html
file1.index.html is labeled with the httpd_sys_content_t. By default, the Apache HTTP Server can access this type, but Samba can not.
service httpd start as the root user to start the Apache HTTP Server:
service httpd start Starting httpd: [ OK ]
wget http://localhost/file1.html command. Unless there are changes to the default configuration, this command succeeds:
$ wget http://localhost/file1.html Resolving localhost... 127.0.0.1 Connecting to localhost|127.0.0.1|:80... connected. HTTP request sent, awaiting response... 200 OK Length: 84 [text/html] Saving to: `file1.html.1' 100%[=======================>] 84 --.-K/s in 0s `file1.html.1' saved [84/84]
/etc/samba/smb.conf as the root user. Add the following to the bottom of this file to share the /var/www/html/ directory through Samba:
[website] comment = Sharing a website path = /var/www/html/ public = no writeable = no
/var/www/html/ directory is labeled with the httpd_sys_content_t type. By default, Samba can not access files and directories labeled with the httpd_sys_content_t type, even if Linux permissions allow it. To allow Samba access, run the following command as the root user to turn the samba_export_all_ro Boolean on:
setsebool -P samba_export_all_ro on
-P option if you do not want the change to persist across reboots. Note: turning the samba_export_all_ro Boolean on allows Samba to access any type.
service smb start as the root user to start smbd:
service smb start Starting SMB services: [ OK ]
vsftpd) is designed from the ground up to be fast, stable, and, most importantly, secure. Its ability to handle large numbers of connections efficiently and securely is why vsftpd is the only stand-alone FTP distributed with Red Hat Enterprise Linux.
rpm -q vsftpd to see if vsftpd is installed:
$ rpm -q vsftpd
yum install vsftpd
vsftpd FTP daemon runs confined by default. SELinux policy defines how vsftpd interacts with files, processes, and with the system in general. For example, when an authenticated user logs in via FTP, they can not read from or write to files in their home directories: SELinux prevents vsftpd from accessing user home directories by default. Also, by default, vsftpd does not have access to NFS or CIFS file systems, and anonymous users do not have write access, even if such write access is configured in /etc/vsftpd/vsftpd.conf. Booleans can be turned on to allow the previously mentioned access.
rpm -q ftp to see if the ftp package is installed. If it is not, run yum install ftp as the root user to install it.
rpm -q vsftpd to see if the vsftpd package is installed. If it is not, run yum install vsftpd as the root user to install it.
vsftpd only allows anonymous users to log in by default. To allow authenticated users to log in, edit /etc/vsftpd/vsftpd.conf as the root user. Make sure the local_enable=YES option is uncommented:
# Uncomment this to allow local users to log in. local_enable=YES
service vsftpd start as the root user to start vsftpd. If the service was running before editing vsftpd.conf, run service vsftpd restart as the root user to apply the configuration changes:
service vsftpd start Starting vsftpd for vsftpd: [ OK ]
ftp localhost as the user you are currently logged in with. When prompted for your name, make sure your username is displayed. If the correct username is displayed, press Enter, otherwise, enter the correct username:
$ ftp localhost Connected to localhost (127.0.0.1). 220 (vsFTPd 2.1.0) Name (localhost:username): 331 Please specify the password. Password:Enter your password500 OOPS: cannot change directory:/home/usernameLogin failed. ftp>
setroubleshoot: SELinux is preventing the ftp daemon from reading users home directories (username). For complete SELinux messages. run sealert -l c366e889-2553-4c16-b73f-92f36a1730ce
ftp_home_dir Boolean. Enable this ftp_home_dir Boolean by running the following command as the root user:
# setsebool -P ftp_home_dir=1
ftp_home_dir Boolean, logging in will succeed.
/var/ftp/ when they log in via FTP. This directory is labeled with the public_content_t type, allowing only read access, even if write access is configured in /etc/vsftpd/vsftpd.conf. The public_content_t type is accessible to other services, such as Apache HTTP Server, Samba, and NFS.
public_content_tpublic_content_t type to share them read-only through vsftpd. Other services, such as Apache HTTP Server, Samba, and NFS, also have access to files labeled with this type. Files labeled with the public_content_t type can not be written to, even if Linux permissions allow write access. If you require write access, use the public_content_rw_t type.
public_content_rw_tpublic_content_rw_t type to share them with read and write permissions through vsftpd. Other services, such as Apache HTTP Server, Samba, and NFS, also have access to files labeled with this type. Remember that Booleans for each service must be turned on before they can write to files labeled with this type.
vsftpd:
allow_ftpd_anon_writevsftpd from writing to files and directories labeled with the public_content_rw_t type. Turn this Boolean on to allow users to upload files via FTP. The directory where files are uploaded to must be labeled with the public_content_rw_t type and Linux permissions set accordingly.
allow_ftpd_full_accesspublic_content_t or public_content_rw_t types.
allow_ftpd_use_cifsvsftpd to access files and directories labeled with the cifs_t type; therefore, having this Boolean enabled allows you to share file systems mounted via Samba through vsftpd.
allow_ftpd_use_nfsvsftpd to access files and directories labeled with the nfs_t type; therefore, having this Boolean enabled allows you to share file systems mounted via NFS through vsftpd.
ftp_home_dir550 Failed to open file. An SELinux denial is logged.
ftpd_connect_dbhttpd_enable_ftp_serverhttpd to listen on the FTP port and act as a FTP server.
tftp_anon_writesetsebool ftp_home_dir=1 as the root user to enable access to FTP home directories.
mkdir -p /myftp/pub as the root user to create a new top-level directory.
/myftp/pub/ directory to allow a Linux user write access. This example changes the owner and group from root to owner user1 and group root. Replace user1 with the user you want to give write access to:
# chown user1:root /myftp/pub # chmod 775 /myftp/pub
chown command changes the owner and group permissions. The chmod command changes the mode, allowing the user1 user read, write, and execute permissions, and members of the root group read, write, and execute permissions. Everyone else has read and execute permissions: this is required to allow the Apache HTTP Server to read files from this directory.
public_content_t type allow them to be read by FTP, Apache HTTP Server, Samba, and rsync. Files labeled with the public_content_rw_t type can be written to by FTP. Other services, such as Samba, require Booleans to be set before they can write to files labeled with the public_content_rw_t type. Label the top-level directory (/myftp/) with the public_content_t type, to prevent copied or newly-created files under /myftp/ from being written to or modified by services. Run the following command as the root user to add the label change to file-context configuration:
semanage fcontext -a -t public_content_t /myftp
restorecon -R -v /myftp/ to apply the label change:
# restorecon -R -v /myftp/ restorecon reset /myftp context unconfined_u:object_r:default_t:s0->system_u:object_r:public_content_t:s0
/myftp is labeled with the public_content_t type, and /myftp/pub/ is labeled with the default_t type:
$ ls -dZ /myftp/ drwxr-xr-x. root root system_u:object_r:public_content_t:s0 /myftp/ $ ls -dZ /myftp/pub/ drwxrwxr-x. user1 root unconfined_u:object_r:default_t:s0 /myftp/pub/
public_content_rw_t type. This example uses /myftp/pub/ as the directory FTP can write to. Run the following command as the root user to add the label change to file-context configuration:
semanage fcontext -a -t public_content_rw_t "/myftp/pub(/.*)?"
restorecon -R -v /myftp/pub as the root user to apply the label change:
# restorecon -R -v /myftp/pub restorecon reset /myftp/pub context system_u:object_r:default_t:s0->system_u:object_r:public_content_rw_t:s0
allow_ftpd_anon_write Boolean must be on to allow vsftpd to write to files that are labeled with the public_content_rw_t type. Run the following command as the root user to turn this Boolean on:
setsebool -P allow_ftpd_anon_write on
-P option if you do not want changes to persist across reboots.
/myftp/pub/ directory:
cd ~/ to change into your home directory. Then, run mkdir myftp to create a directory to store files to upload via FTP.
cd ~/myftp to change into the ~/myftp/ directory. In this directory, create an ftpupload file. Copy the following contents into this file:
File upload via FTP from a home directory.
getsebool allow_ftpd_anon_write to confirm the allow_ftpd_anon_write Boolean is on:
$ getsebool allow_ftpd_anon_write allow_ftpd_anon_write --> on
setsebool -P allow_ftpd_anon_write on as the root user to turn it on. Do not use the -P option if you do not want the change to persist across reboots.
service vsftpd start as the root user to start vsftpd:
# service vsftpd start Starting vsftpd for vsftpd: [ OK ]
ftp localhost. When prompted for a username, enter the the username of the user who has write access, then, enter the correct password for that user:
$ ftp localhost Connected to localhost (127.0.0.1). 220 (vsFTPd 2.1.0) Name (localhost:username): 331 Please specify the password. Password:Enter the correct password230 Login successful. Remote system type is UNIX. Using binary mode to transfer files. ftp> cd myftp 250 Directory successfully changed. ftp> put ftpupload local: ftpupload remote: ftpupload 227 Entering Passive Mode (127,0,0,1,241,41). 150 Ok to send data. 226 File receive OK. ftp> 221 Goodbye.
allow_ftpd_anon_write Boolean is enabled.
rpm -q nfs-utils to see if the nfs-utils is installed. If it is not installed and you want to use NFS, run the following command as the root user to install it:
yum install nfs-utils
NFS daemons are confined by default. SELinux policy does not allow NFS to share files by default. If you want to share NFS partitions, this can be configured via the nfs_export_all_ro and nfs_export_all_rw Booleans, as described in this section. These Booleans are however not required when files to be shared are labeled with the public_content_t or public_content_rw_t types. NFS can share files labeled with these types even if the nfs_export_all_ro and nfs_export_all_rw Booleans are off.
nfs_t type.The following types are used with NFS. Different types allow you to configure flexible access:
var_lib_nfs_t/var/lib/nfs directory. This type should not need to be changed in normal operation. To restore changes to the default settings, run the restorecon -R -v /var/lib/nfs command as the root user.
nfsd_exec_t/usr/sbin/rpc.nfsd file is labeled with the nfsd_exec_t, as are other system executables and libraries related to NFS. Users should not label any files with this type. nfsd_exec_t will transition to nfs_t.
allow_ftpd_use_nfsftpd access to NFS mounts.
allow_nfsd_anon_writenfsd to write to a public directory anonymously; such as to an area reserved for common files that otherwise has no special access restrictions.
httpd_use_nfshttpd to access files stored on a NFS filesystem.
nfs_export_all_ronfs_export_all_rwqemu_use_nfssamba_share_nfssmbd from having full access to NFS shares via Samba. Enabling this Boolean will allow Samba to share NFS file systems.
use_nfs_home_dirsvirt_use_nfsxen_use_nfsnfs-srv with an IP address of 192.168.1.1, and a client with a hostname of nfs-client and an IP address of 192.168.1.100. Both hosts are on the same subnet (192.168.1.0/24). This is an example only and assumes that the nfs-utils package is installed, that the SELinux targeted policy is used, and that SELinux is running in enforced mode.
nfs-srv.
setsebool command to disable read/write mounting of NFS file systems:
setsebool -P nfs_export_all_rw off
-P option if you do not want setsebool changes to persist across reboots.
rpm -q nfs-utils to confirm the nfs-utils package is installed. The nfs-utils package provides support programs for using NFS and should be installed on a NFS server and on any clients in use. If this package is not installed, install it by running yum install nfs-utils as the root user.
mkdir /myshare as the root user to create a new top-level directory to share using NFS.
touch /myshare/file1 as the root user to create a new empty file in the shared area. This file will be accessed later by the client.
/myshare directory full Linux access rights for all users:
# chmod -R 777 /myshare
/etc/exports file and add the following line to the top of the file:
/myshare 192.168.1.100(rw)
/myshare, the host or network range that nfs-srv will share to (in this case the IP address of a single host, nfs-client at 192.168.1.100), and finally the share permissions. Read and write permissions are given here, as indicated by (rw).
MOUNTD_PORT,STATD_PORT,LOCKD_TCPPORT and LOCKD_UDPPORT variables. Changing the port numbers in this file is not required for this example.
MOUNTD_PORT="port" option.
STATD_PORT="port" option.
LOCKD_TCPPORT="port" option.
LOCKD_UDPPORT="port" option.
service nfs start as the root user to start NFS and its related services:
# service nfs start Starting NFS services: [ OK ] Starting NFS quotas: [ OK ] Starting NFS daemon: [ OK ] Starting NFS mountd: [ OK ]
exportfs -rv as the root user:
# exportfs -rv exporting 192.168.1.100:/myshare
showmount -e as the root user to show all exported file systems:
# showmount -e Export list for nfs-srv: /myshare 192.168.1.100
nfs-srv has been configured to allow NFS communications to nfs-client at 192.168.1.100, and full Linux file systems permissions are active. If SELinux were disabled, the client would be able to mount this share and have full access over it. However, as the nfs_export_all_rw Boolean is disabled, the client is currently not able to mount this file system, as shown in the following output. This step should be performed on the client, nfs-client:
[nfs-client]# mkdir /myshare [nfs-client]# mount.nfs 192.168.1.1:/myshare /myshare mount.nfs: access denied by server while mounting 192.168.1.1:/myshare/
nfs-srv:
[nfs-srv]# setsebool -P nfs_export_all_rw on
[nfs-srv]# service nfs restart
nfs-client:
[nfs-client]# mount.nfs 192.168.1.1:/myshare /myshare [nfs-client]# [nfs-client]# ls /myshare total 0 -rwxrwxrwx. 1 root root 0 2009-04-16 12:07 file1 [nfs-client]#
named daemon. BIND lets users locate computer resources and services by name instead of numerical addresses.
rpm -q bind to see if the bind package is installed. If it is not installed, run the following command as the root user to install it:
yum install bind
/var/named/slaves,/var/named/dynamic and /var/named/data directories allow zone files to be updated via zone transfers and dynamic DNS updates. Files in /var/named are labeled with the named_zone_t type, which is used for master zone files.
/etc/named.conf to place slave zones in /var/named/slaves. The following is an example of a domain entry in /etc/named.conf for a slave DNS server that stores the zone file for testdomain.com in /var/named/slaves:
zone "testdomain.com" {
type slave;
masters { IP-address; };
file "/var/named/slaves/db.testdomain.com";
};
named_zone_t, the named_write_master_zones Boolean must be enabled to allow zone transfers and dynamic DNS to update the zone file. Also, the mode of the parent directory has to be changed to allow the named user or group read, write and execue access.
/var/named/ are labeled with named_cache_t type, a file system relabel or running restorecon -R /var/ will change their type to named_zone_t.
named_zone_tnamed can only modify files of this type if the named_write_master_zones Boolean is turned on.
named_cache_tnamed can write to files labeled with this type, without additional Booleans being set. Files copied or created in the /var/named/slaves,/var/named/dynamic and /var/named/data directories are automatically labeled with the named_cache_t type.
named_write_master_zonesnamed from writing to zone files or directories labeled with the named_zone_t type. named does not usually need to write to zone files; but in the case that it needs to, or if a secondary server needs to write to zone files, enable this Boolean to allow this action.
/var/named/dynamic directory for zone files you want updated via dynamic DNS. Files created in or copied into /var/named/dynamic inherit Linux permissions that allow named to write to them. As such files are labeled with the named_cache_t type, SELinux allows named to write to them.
/var/named/dynamic is labeled with the named_zone_t type, dynamic DNS updates may not be successful for a certain period of time as the update needs to be written to a journal first before being merged. If the zone file is labeled with the named_zone_t type when the journal attempts to be merged, an error such as the following is logged:
named[PID]: dumping master file: rename: /var/named/dynamic/zone-name: permission denied
setroubleshoot: SELinux is preventing named (named_t) "unlink" to zone-name (named_zone_t)
restorecon -R -v /var/named/dynamic command as the Linux root user.
rpm -q cvs to see if the cvs package is installed. If it is not installed and you want to use CVS, run the following command as the root user to install it:
yum install cvs
cvs daemon runs as cvs_t. By default in Red Hat Enterprise Linux, CVS is only allowed to read and write certain directories. The label cvs_data_t defines which areas the cvs daemon has read and write access to. When using CVS with SELinux, assigning the correct label is essential for clients to have full access to the area reserved for CVS data.
cvs_data_tcvs_exec_t/usr/bin/cvs binary.
allow_cvs_read_shadowcvs daemon to access the /etc/shadow file for user authentication.
cvs-srv with an IP address of 192.168.1.1 and a client with a hostname of cvs-client and an IP address of 192.168.1.100. Both hosts are on the same subnet (192.168.1.0/24). This is an example only and assumes that the cvs and xinetd packages are installed, that the SELinux targeted policy is used, and that SELinux is running in enforced mode.
cvs-srv.
rpm -q cvs to see if the cvs package is installed. If it is not installed, run the following command as the root user to install cvs:
# yum install cvs
rpm -q xinetd to see if the xinetd package is installed. If it is not installed, run the following command as the root user to install xinetd:
# yum install xinetd
CVS. This can be done via the groupadd CVS command as the root user, or by using the system-config-users tool.
cvsuser and make this user a member of the CVS group. This can be done using the system-config-users tool.
/etc/services file and make sure that the CVS server has uncommented entries looking similar to the following:
cvspserver 2401/tcp # CVS client/server operations cvspserver 2401/udp # CVS client/server operations
/cvs directory to house the repository:
[root@cvs-srv]# mkdir /cvs
/cvs directory to all users:
[root@cvs-srv]# chmod -R 777 /cvs
/etc/xinetd.d/cvs file and make sure that the CVS section is uncommented and configured to use the /cvs directory. The file should look similar to:
service cvspserver
{
disable = no
port = 2401
socket_type = stream
protocol = tcp
wait = no
user = root
passenv = PATH
server = /usr/bin/cvs
env = HOME=/cvs
server_args = -f --allow-root=/cvs pserver
# bind = 127.0.0.1
xinetd daemon by running service xinetd start as the root user.
cvsuser user, run the following command:
[cvsuser@cvs-client]$ cvs -d /cvs init
cvs-client and try to log in remotely. The following step should be performed on cvs-client:
[cvsuser@cvs-client]$ export CVSROOT=:pserver:[email protected]:/cvs [cvsuser@cvs-client]$ [cvsuser@cvs-client]$ cvs login Logging in to :pserver:[email protected]:2401/cvs CVS password: ******** cvs [login aborted]: unrecognized auth response from 192.168.100.1: cvs pserver: cannot open /cvs/CVSROOT/config: Permission denied
cvs-srv:
/cvs directory as the root user in order to recursively label any existing and new data in the /cvs directory, giving it the cvs_data_t type:
[root@cvs-srv]# semanage fcontext -a -t cvs_data_t '/cvs(/.*)?' [root@cvs-srv]# restorecon -R -v /cvs
cvs-client should now be able to log in and access all CVS resources in this repository:
[cvsuser@cvs-client]$ export CVSROOT=:pserver:[email protected]:/cvs [cvsuser@cvs-client]$ [cvsuser@cvs-client]$ cvs login Logging in to :pserver:[email protected]:2401/cvs CVS password: ******** [cvsuser@cvs-client]$
rpm -q squid to see if the squid package is installed. If it is not installed and you want to use squid, run the following command as the root user to install it:
# yum install squid
getenforce to confirm SELinux is running in enforcing mode:
$ getenforce Enforcing
getenforce command returns Enforcing when SELinux is running in enforcing mode.
service squid start as the root user to start squid:
# service squid start Starting squid: [ OK ]
ps -eZ | grep squid to view the squid processes:
$ ps -eZ | grep squid unconfined_u:system_r:squid_t:s0 2522 ? 00:00:00 squid unconfined_u:system_r:squid_t:s0 2524 ? 00:00:00 squid unconfined_u:system_r:squid_t:s0 2526 ? 00:00:00 ncsa_auth unconfined_u:system_r:squid_t:s0 2527 ? 00:00:00 ncsa_auth unconfined_u:system_r:squid_t:s0 2528 ? 00:00:00 ncsa_auth unconfined_u:system_r:squid_t:s0 2529 ? 00:00:00 ncsa_auth unconfined_u:system_r:squid_t:s0 2530 ? 00:00:00 ncsa_auth unconfined_u:system_r:squid_t:s0 2531 ? 00:00:00 unlinkd
squid processes is unconfined_u:system_r:squid_t:s0. The second last part of the context, squid_t, is the type. A type defines a domain for processes and a type for files. In this case, the squid processes are running in the squid_t domain.
squid_t, interact with files, other processes, and the system in general. Files must be labeled correctly to allow squid access to them.
/etc/squid/squid.conf is configured so squid listens on a port other than the default TCP ports 3128, 3401 or 4827, the semanage port command must be used to add the required port number to the SELinux policy configuration. The following example demonstrates configuring squid to listen on a port that is not initially defined in SELinux policy configuration for squid, and, as a consequence, squid failing to start. This example also demonstrates how to then configure the SELinux system to allow squid to successfully listen on a non-standard port that is not already defined in the policy. This example assumes the squid package is installed. Run each command in the example as the root user:
service squid status to confirm squid is not running:
# service squid status squid is stopped
service squid stop to stop the process:
# service squid stop Stopping squid: [ OK ]
semanage port -l | grep -w squid_port_t to view the ports SELinux allows squid to listen on:
semanage port -l | grep -w -i squid_port_t squid_port_t tcp 3128, 3401, 4827 squid_port_t udp 3401, 4827
/etc/squid/squid.conf as the root user. Configure the http_port option so it lists a port that is not configured in SELinux policy configuration for squid. In this example, squid is configured to listen on port 10000:
# Squid normally listens to port 3128 http_port 10000
setsebool command to make sure the squid_connect_any Boolean is set to off. This ensures squid is only permitted to operate on specific ports:
setsebool -P squid_connect_any 0
service squid start to start squid:
# service squid start Starting squid: .................... [FAILED]
localhost setroubleshoot: SELinux is preventing the squid (squid_t) from binding to port 10000. For complete SELinux messages. run sealert -l 97136444-4497-4fff-a7a7-c4d8442db982
squid to listen on port 10000, as used in this example, the following command is required:
# semanage port -a -t squid_port_t -p tcp 10000
service squid start again to start squid and have it listen on the new port:
# service squid start Starting squid: [ OK ]
squid to listen on a non-standard port (TCP 10000 in this example), squid starts successfully on this port.
squid. Different types allow you to configure flexible access:
httpd_squid_script_exec_tcachemgr.cgi, which provides a variety of statistics about squid and its configuration.
squid_cache_tcache_dir directive in /etc/squid/squid.conf. By default, files created in or copied into /var/cache/squid and /var/spool/squid are labeled with the squid_cache_t type. Files for the squidGuard URL redirector plugin for squid created in or copied to /var/squidGuard are also labeled with the squid_cache_t type. Squid is only able to use files and directories that are labeled with this type for its cached data.
squid_conf_tsquid uses for its configuration. Existing files, or those created in or copied to /etc/squid and /usr/share/squid are labeled with this type, including error messages and icons.
squid_exec_t/usr/sbin/squid.
squid_log_t/var/log/squid or /var/log/squidGuard must be labeled with this type.
squid_initrc_exec_tsquid which is located at /etc/rc.d/init.d/squid.
squid_var_run_t/var/run, especially the process id (PID) named /var/run/squid.pid which is created by squid when it runs.
squid_connect_anyrpm -q squid to see if the squid package is installed. If it is not installed, run yum install squid as the root user to install it.
/etc/squid/squid.conf and confirm that the cache_dir directive is uncommented and looks similar to the following:
cache_dir ufs /var/spool/squid 100 16 256
cache_dir directive to be used in this example; it consists of the Squid storage format (ufs), the directory on the system where the cache resides (/var/spool/squid), the amount of disk space in megabytes to be used for the cache (100), and finally the number of first-level and second-level cache directories to be created (16 and 256 respectively).
http_access allow localnet directive is uncommented. This allows traffic from the localnet ACL which is automatically configured in a default installation of Squid on Red Hat Enterprise Linux. It will allow client machines on any existing RFC1918 network to have access through the proxy, which is sufficient for this simple example.
visible_hostname directive is uncommented and is configured to the hostname of the machine. The value should be the fully qualified domain name (FQDN) of the host:
visible_hostname squid.example.com
service squid start to start squid. As this is the first time squid has started, this command will initialise the cache directories as specified above in the cache_dir directive and will then start the squid daemon. The output is as follows if squid starts successfully:
# /sbin/service squid start init_cache_dir /var/spool/squid... Starting squid: . [ OK ]
squid process ID (PID) has started as a confined service, as seen here by the squid_var_run_t value:
# ls -lZ /var/run/squid.pid
-rw-r--r--. root squid unconfined_u:object_r:squid_var_run_t:s0 /var/run/squid.pid
localnet ACL configured earlier is successfully able to use the internal interface of this host as its proxy. This can be configured in the settings for all common web browsers, or system-wide. Squid is now listening on the default port of the target machine (TCP 3128), but the target machine will only allow outgoing connections to other services on the Internet via common ports. This is a policy defined by SELinux itself. SELinux will deny access to non-standard ports, as shown in the next step:
SELinux is preventing the squid daemon from connecting to network port 10000
squid_connect_any Boolean must be modified, as it is disabled by default. To turn the squid_connect_any Boolean on, run the following command as the root user:
# setsebool -P squid_connect_any on
-P option if you do not want setsebool changes to persist across reboots.
rpm -q mysql-server to see if the mysql-server package is installed. If it is not installed, run the following command as the root user to install it:
yum install mysql-server
getenforce to confirm SELinux is running in enforcing mode:
$ getenforce Enforcing
getenforce command returns Enforcing when SELinux is running in enforcing mode.
service mysqld start as the root user to start mysqld:
# service mysqld start Initializing MySQL database: Installing MySQL system tables... [ OK ] Starting MySQL: [ OK ]
ps -eZ | grep mysqld to view the mysqld processes:
$ ps -eZ | grep mysqld unconfined_u:system_r:mysqld_safe_t:s0 6035 pts/1 00:00:00 mysqld_safe unconfined_u:system_r:mysqld_t:s0 6123 pts/1 00:00:00 mysqld
mysqld processes is unconfined_u:system_r:mysqld_t:s0. The second last part of the context, mysqld_t, is the type. A type defines a domain for processes and a type for files. In this case, the mysqld processes are running in the mysqld_t domain.
mysql. Different types allow you to configure flexible access:
mysqld_db_t/var/lib/mysql, however this can be changed. If the location for the MySQL database is changed, the new location must be labeled with this type. Refer to the following example for instructions on how to change the default database location and how to label the new section appropriately.
mysqld_etc_t/etc/my.cnf and any other configuration files in the /etc/mysql directory.
mysqld_exec_tmysqld binary located at /usr/libexec/mysqld, which is the default location for the MySQL binary on Red Hat Enterprise Linux. Other systems may locate this binary at /usr/sbin/mysqld which should also be labeled with this type.
mysqld_initrc_exec_t/etc/rc.d/init.d/mysqld by default in Red Hat Enterprise Linux.
mysqld_log_t/var/log/ matching the mysql.* wildcard must be labeled with this type.
mysqld_var_run_t/var/run/mysqld, specifically the process id (PID) named /var/run/mysqld/mysqld.pid which is created by the mysqld daemon when it runs. This type is also used for related socket files such as /var/lib/mysql/mysql.sock. Files such as these must be labeled correctly for proper operation as a confined service.
allow_user_mysql_connectexim_can_connect_dbexim mailer to initiate connections to a database server.
ftpd_connect_dbftp daemons to initiate connections to a database server.
httpd_can_network_connect_db/var/lib/mysql. This is where SELinux expects it to be by default, and hence this area is already labeled appropriately for you, using the mysqld_db_t type.
auditd service is running, and that there is a valid database in the default location of /var/lib/mysql.
ls -lZ /var/lib/mysql to view the SELinux context of the default database location for mysql:
# ls -lZ /var/lib/mysql
drwx------. mysql mysql unconfined_u:object_r:mysqld_db_t:s0 mysql
mysqld_db_t which is the default context element for the location of database files. This context will have to be manually applied to the new database location that will be used in this example in order for it to function properly.
mysqlshow -u root -p and enter the mysqld root password to show the available databases:
# mysqlshow -u root -p Enter password: ******* +--------------------+ | Databases | +--------------------+ | information_schema | | mysql | | test | | wikidb | +--------------------+
mysqld daemon with service mysqld stop as the root user:
# service mysqld stop Stopping MySQL: [ OK ]
/opt/mysql is used:
# mkdir -p /opt/mysql
# cp -R /var/lib/mysql/* /opt/mysql/
# chown -R mysql:mysql /opt/mysql
ls -lZ /opt to see the initial context of the new directory:
# ls -lZ /opt
drwxr-xr-x. mysql mysql unconfined_u:object_r:usr_t:s0 mysql
usr_t of this newly created directory is not currently suitable to SELinux as a location for MySQL database files. Once the context has been changed, MySQL will be able to function properly in this area.
/etc/my.cnf with a text editor and modify the datadir option so that it refers to the new location. In this example the value that should be entered is /opt/mysql.
[mysqld] datadir=/opt/mysql
service mysqld start as the root user to start mysqld. The service should fail to start, and a denial will be logged to /var/log/messages:
SELinux is preventing /usr/libexec/mysqld "write" access on /opt/mysql. For complete SELinux messages. run sealert -l b3f01aff-7fa6-4ebe-ad46-abaef6f8ad71
/opt/mysql is not labeled correctly for MySQL data files. SELinux is stopping MySQL from having access to the content labeled as usr_t. Perform the following steps to resolve this problem:
semanage command to add a context mapping for /opt/mysql:
semanage fcontext -a -t mysqld_db_t "/opt/mysql(/.*)?"
/etc/selinux/targeted/contexts/files/file_contexts.local file:
# grep -i mysql /etc/selinux/targeted/contexts/files/file_contexts.local /opt/mysql(/.*)? system_u:object_r:mysqld_db_t:s0
restorecon command to apply this context mapping to the running system:
restorecon -R -v /opt/mysql
/opt/mysql location has been labeled with the correct context for MySQL, the mysqld daemon starts:
# service mysqld start Starting MySQL: [ OK ]
/opt/mysql:
ls -lZ /opt
drwxr-xr-x. mysql mysql system_u:object_r:mysqld_db_t:s0 mysql
mysqld daemon has started successfully. At this point all running services should be tested to confirm normal operation.
rpm -q postgresql-server to see if the postgresql-server package is installed. If it is not installed, run the following command as the root user to install it:
yum install postgresql-server
getenforce to confirm SELinux is running in enforcing mode:
$ getenforce Enforcing
getenforce command returns Enforcing when SELinux is running in enforcing mode.
service postgresql start as the root user to start postgresql:
service postgresql start Starting postgresql service: [ OK ]
ps -eZ | grep postgres to view the postgresql processes:
ps -eZ | grep postgres unconfined_u:system_r:postgresql_t:s0 395 ? 00:00:00 postmaster unconfined_u:system_r:postgresql_t:s0 397 ? 00:00:00 postmaster unconfined_u:system_r:postgresql_t:s0 399 ? 00:00:00 postmaster unconfined_u:system_r:postgresql_t:s0 400 ? 00:00:00 postmaster unconfined_u:system_r:postgresql_t:s0 401 ? 00:00:00 postmaster unconfined_u:system_r:postgresql_t:s0 402 ? 00:00:00 postmaster
postgresql processes is unconfined_u:system_r:postgresql_t:s0. The second last part of the context, postgresql_t, is the type. A type defines a domain for processes and a type for files. In this case, the postgresql processes are running in the postgresql_t domain.
postgresql. Different types allow you to configure flexible access:
postgresql_db_t/usr/lib/pgsql/test/regres
/usr/share/jonas/pgsql
/var/lib/pgsql/data
/var/lib/postgres(ql)?
postgresql_etc_t/etc/postgresql.
postgresql_exec_t/usr/bin/initdb(.sepgsql)?
/usr/bin/(se)?postgres
/usr/lib(64)?/postgresql/bin/.*
/usr/lib/phsql/test/regress/pg_regress
postgresql_initrc_exec_t/etc/rc.d/init.d/postgresql.
postgresql_log_t/var/lib/pgsql/logfile
/var/lib/pgsql/pgstartup.log
/var/lib/sepgsql/pgstartup.log
/var/log/postgresql
/var/log/postgres.log.*
/var/log/rhdb/rhdb
/var/log/sepostgresql.log.*
postgresql_var_run_t/var/run/postgresql.
allow_user_postgresql_connect/var/lib/pgsql/data. This is where SELinux expects it to be by default, and hence this area is already labeled appropriately for you, using the postgresql_db_t type.
ls -lZ /var/lib/pgsql to view the SELinux context of the default database location for postgresql:
# ls -lZ /var/lib/pgsql
drwx------. postgres postgres system_u:object_r:postgresql_db_t:s0 data
postgresql_db_t which is the default context element for the location of database files. This context will have to be manually applied to the new database location that will be used in this example in order for it to function properly.
/opt/postgresql/data is used. If you use a different location, replace the text in the following steps with your location:
# mkdir -p /opt/postgresql/data
# ls -lZ /opt/postgresql/
drwxr-xr-x. root root unconfined_u:object_r:usr_t:s0 data
# chown -R postgres:postgres /opt/postgresql
/etc/rc.d/init.d/postgresql with a text editor and modify the PGDATA and PGLOG variables to point to the new location:
# vi /etc/rc.d/init.d/postgresql PGDATA=/opt/postgresql/data PGLOG=/opt/postgresql/data/pgstartup.log
su - postgres -c "initdb -D /opt/postgresql/data"
# service postgresql start Starting postgresql service: [FAILED]
/opt/postgresql) and start the postgresql service properly:
semanage command to add a context mapping for /opt/postgresql and any other directories/files within it:
semanage fcontext -a -t postgresql_db_t "/opt/postgresql(/.*)?"
/etc/selinux/targeted/contexts/files/file_contexts.local file:
# grep -i postgresql /etc/selinux/targeted/contexts/files/file_contexts.local /opt/postgresql(/.*)? system_u:object_r:postgresql_db_t:s0
restorecon command to apply this context mapping to the running system:
restorecon -R -v /opt/postgresql
/opt/postgresql location has been labeled with the correct context for PostgreSQL, the postgresql service will start successfully:
# service postgresql start Starting postgreSQL service: [ OK ]
/opt/postgresql:
ls -lZ /opt
drwxr-xr-x. root root system_u:object_r:postgresql_db_t:s0 postgresql
ps command that the postgresql process displays the new location:
# ps aux | grep -i postmaster
postgres 21564 0.3 0.3 42308 4032 ? S 10:13 0:00 /usr/bin/postmaster -p 5432 -D /opt/postgresql/datapostgresql daemon has started successfully. At this point all running services should be tested to confirm normal operation.
rpm -q rsync to see if the rsync package is installed. If it is not installed, run the following command as the root user to install it:
yum install rsync
rsync.
rsync. Different types all you to configure flexible access:
public_content_trsync. If a special directory is created to house files to be shared with rsync, the directory and its contents need to have this label applied to them.
rsync_exec_t/usr/bin/rsync system binary.
rsync_log_trsync log file, located at /var/log/rsync.log by default. To change the location of the file rsync logs to, use the --log-file=FILE option to the rsync command at run-time.
rsync_var_run_trsyncd lock file, located at /var/run/rsyncd.lock. This lock file is used by the rsync server to manage connection limits.
allow_rsync_anon_writersync in the rsync_t domain to manage files, links and directories that have a type of public_content_rw_t. Often these are public files used for public file transfer services. Files and directories must be labeled public_content_rw_t.
rsync_clientrsync to initiate connections to ports defined as rsync_port_t, as well as allowing rsync to manage files, links and directories that have a type of rsync_data_t. Note that the rsync daemon must be in the rsync_t domain in order for SELinux to enact its control over rsync. The configuration example in this chapter demonstrates rsync running in the rsync_t domain.
rsync_export_all_rorsync in the rsync_t domain to export NFS and CIFS file systems with read-only access to clients.
rsync daemon to run normally on a non-standard port.
getenforce to confirm SELinux is running in enforcing mode:
$ getenforce Enforcing
getenforce command returns Enforcing when SELinux is running in enforcing mode.
which command to confirm that the rsync binary is in the system path:
$ which rsync /usr/bin/rsync
rsync as a daemon, a configuration file should be used and saved as /etc/rsyncd.conf. Note that the following configuration file used in this example is very simple and is not indicative of all the possible options that are available, rather it is just enough to demonstrate the rsync daemon:
log file = /var/log/rsyncd.log
pid file = /var/run/rsyncd.pid
lock file = /var/run/rsync.lock
[files]
path = /srv/files
comment = file area
read only = false
timeout = 300
rsync --daemon is not sufficient for SELinux to offer its protection over rsync. Refer to the following output:
# rsync --daemon
# ps x | grep rsync
8231 ? Ss 0:00 rsync --daemon
8233 pts/3 S+ 0:00 grep rsync
# ps -eZ | grep rsync
unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 8231 ? 00:00:00 rsync
ps command, the context shows the rsync daemon running in the unconfined_t domain. This indicates that rsync has not transitioned to the rsync_t domain as it was launched by the rsync --daemon command. At this point SELinux can not enforce its rules and policy over this daemon. Refer to the following steps to see how to fix this problem. In the following steps, rsync will transition to the rsync_t domain by launching it from a properly-labeled init script. Only then can SELinux and its protection mechanisms have an effect over rsync. This rsync process should be killed before proceeding to the next step.
/etc/rc.d/init.d/rsyncd.
#!/bin/bash
# Source function library.
. /etc/rc.d/init.d/functions
[ -f /usr/bin/rsync ] || exit 0
case "$1" in
start)
action "Starting rsyncd: " /usr/bin/rsync --daemon
;;
stop)
action "Stopping rsyncd: " killall rsync
;;
*)
echo "Usage: rsyncd {start|stop}"
exit 1
esac
exit 0
initrc_exec_t:
semanage command to add a context mapping for /etc/rc.d/init.d/rsyncd:
semanage fcontext -a -t initrc_exec_t "/etc/rc.d/init.d/rsyncd"
/etc/selinux/targeted/contexts/files/file_contexts.local file:
# grep rsync /etc/selinux/targeted/contexts/files/file_contexts.local /etc/rc.d/init.d/rsyncd system_u:object_r:initrc_exec_t:s0
restorecon command to apply this context mapping to the running system:
restorecon -R -v /etc/rc.d/init.d/rsyncd
ls -lZ command to confirm the script has been labeled appropriately. Note that in the following output the script has been labeled as initrc_exec_t:
ls -lZ /etc/rc.d/init.d/rsyncd
-rwxr-xr-x. root root system_u:object_r:initrc_exec_t:s0 /etc/rc.d/init.d/rsyncd
rsyncd via the new script. Now that rsync has started from an init script that has been appropriately labeled, the process will start as rsync_t:
# service rsyncd start
Starting rsyncd: [ OK ]
ps -eZ | grep rsync
unconfined_u:system_r:rsync_t:s0 9794 ? 00:00:00 rsync
rsync daemon as it is now runing in the rsync_t domain.
rsyncd running in the rsync_t domain. The next example shows how to get this daemon successfully running on a non-default port. TCP port 10000 is used in the next example.
/etc/rsyncd.conf file and add the port = 10000 line at the top of the file in the global configuration area (ie., before any file areas are defined). The new configuration file will look like:
log file = /var/log/rsyncd.log
pid file = /var/run/rsyncd.pid
lock file = /var/run/rsync.lock
port = 10000
[files]
path = /srv/files
comment = file area
read only = false
timeout = 300
Jul 22 10:46:59 localhost setroubleshoot: SELinux is preventing the rsync (rsync_t) from binding to port 10000. For complete SELinux messages. run sealert -l c371ab34-639e-45ae-9e42-18855b5c2de8
semanage command to add TCP port 10000 to SELinux policy in rsync_port_t:
# semanage port -a -t rsync_port_t -p tcp 10000
rsync_port_t, rsyncd will start and operate normally on this port:
# service rsyncd start Starting rsyncd: [ OK ]
# netstat -lnp | grep 10000
tcp 0 0 0.0.0.0:10000 0.0.0.0:* LISTEN 9910/rsync
rsyncd to operate on TCP port 10000.
rpm -q postfix to see if the postfix package is installed. If it is not installed, run the following command as the root user to install it:
yum install postfix
getenforce to confirm SELinux is running in enforcing mode:
$ getenforce Enforcing
getenforce command returns Enforcing when SELinux is running in enforcing mode.
service postfix start as the root user to start postfix:
service postfix start Starting postfix: [ OK ]
ps -eZ | grep postfix to view the postfix processes:
ps -eZ | grep postfix system_u:system_r:postfix_master_t:s0 1651 ? 00:00:00 master system_u:system_r:postfix_pickup_t:s0 1662 ? 00:00:00 pickup system_u:system_r:postfix_qmgr_t:s0 1663 ? 00:00:00 qmgr
master process is unconfined_u:system_r:postfix_master_t:s0. The second last part of the context, postfix_master_t, is the type for this process. A type defines a domain for processes and a type for files. In this case, the master process is running in the postfix_master_t domain.
Postfix. Different types all you to configure flexible access:
postfix_etc_t/etc/postfix.
postfix_data_t/var/lib/postfix.
$ grep postfix /etc/selinux/targeted/contexts/files/file_contexts
allow_postfix_local_write_mail_spoolrpm -q spamassassin to see if the spamassassin package is installed. If it is not installed, run the following command as the root user to install it:
yum install spamassassin
semanage command to show the port that SELinux allows spamd to listen on by default:
# semanage port -l | grep spamd spamd_port_t tcp 783
spamd_port_t as the port for SpamAssassin to operate on.
/etc/sysconfig/spamassassin configuration file and modify it so that it will start SpamAssassin on the example port TCP/10000:
# Options to spamd SPAMDOPTIONS="-d -p 10000 -c m5 -H"
# service spamassassin start
Starting spamd: [2203] warn: server socket setup failed, retry 1: spamd: could not create INET socket on 127.0.0.1:10000: Permission denied
[2203] warn: server socket setup failed, retry 2: spamd: could not create INET socket on 127.0.0.1:10000: Permission denied
[2203] error: spamd: could not create INET socket on 127.0.0.1:10000: Permission denied
spamd: could not create INET socket on 127.0.0.1:10000: Permission denied
[FAILED]
SELinux is preventing the spamd (spamd_t) from binding to port 10000.
semanage command to modify SELinux policy in order to allow SpamAssassin to operate on the example port (TCP/10000):
semanage port -a -t spamd_port_t -p tcp 10000
# service spamassassin start Starting spamd: [ OK ] # netstat -lnp | grep 10000 tcp 0 0 127.0.0.1:10000 0.0.0.0:* LISTEN 2224/spamd.pid
spamd is properly operating on TCP port 10000 as it has been allowed access to that port by SELinux policy.
dhcpd. Run rpm -q dhcp to see if the dhcp package is installed. If it is not installed, run the following command as the root user to install it:
yum install dhcp
getenforce to confirm SELinux is running in enforcing mode:
$ getenforce Enforcing
getenforce command returns Enforcing when SELinux is running in enforcing mode.
service dhcpd start as the root user to start DHCPD:
service dhcpd start Starting dhcpd: [ OK ]
ps -eZ | grep dhcpd to view the dhcpd processes:
ps -eZ | grep dhcpd unconfined_u:system_r:dhcpd_t:s0 5483 ? 00:00:00 dhcpd
unconfined_u:system_r:dhcpd_t:s0.
dhcpd:
dhcp_etc_t/etc, including configuration files.
dhcp_var_run_t/var/run.
$ grep dhcp /etc/selinux/targeted/contexts/files/file_contexts