--enableshadow, --useshadow
|
Enable shadow passwords
|
--disableshadow
|
Disable shadow passwords
|
--passalgo=<descrypt|bigcrypt|md5|sha256|sha512>
|
Hash/crypt algorithm to be used
|
--enablenis
|
Enable NIS for user account configuration
|
--disablenis
|
Disable NIS for user account configuration
|
--nisdomain=<domain>
|
Specify an NIS domain
|
--nisserver=<server>
|
Specify an NIS server
|
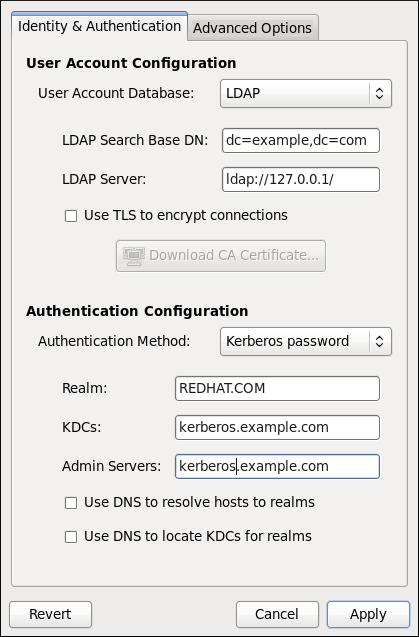
--enableldap
|
Enable LDAP for user account configuration
|
--disableldap
|
Disable LDAP for user account configuration
|
--enableldaptls
|
Enable use of TLS with LDAP
|
--disableldaptls
|
Disable use of TLS with LDAP
|
--enablerfc2307bis
|
Enable use of RFC-2307bis schema for LDAP user information lookups
|
--disablerfc2307bis
|
Disable use of RFC-2307bis schema for LDAP user information lookups
|
--enableldapauth
|
Enable LDAP for authentication
|
--disableldapauth
|
Disable LDAP for authentication
|
--ldapserver=<server>
|
Specify an LDAP server
|
--ldapbasedn=<dn>
|
Specify an LDAP base DN (Distinguished Name)
|
--ldaploadcacert=<URL>
|
Load a CA certificate from the specified URL
|
--enablekrb5
|
Enable Kerberos for authentication
|
--disablekrb5
|
Disable Kerberos for authentication
|
--krb5kdc=<server>
|
Specify Kerberos KDC server
|
--krb5adminserver=<server>
|
Specify Kerberos administration server
|
--krb5realm=<realm>
|
Specify Kerberos realm
|
--enablekrb5kdcdns
|
Enable use of DNS to find Kerberos KDCs
|
--disablekrb5kdcdns
|
Disable use of DNS to find Kerberos KDCs
|
--enablekrb5realmdns
|
Enable use of DNS to find Kerberos realms
|
--disablekrb5realmdns
|
Disable use of DNS to find Kerberos realms
|
--enablewinbind
|
Enable winbind for user account configuration
|
--disablewinbind
|
Disable winbind for user account configuration
|
--enablewinbindauth
|
Enable winbindauth for authentication
|
--disablewinbindauth
|
Disable winbindauth for authentication
|
--winbindseparator=<\>
|
Character used to separate the domain and user part of winbind usernames if winbindusedefaultdomain is not enabled
|
--winbindtemplatehomedir=</home/%D/%U>
|
Directory that winbind users have as their home
|
--winbindtemplateprimarygroup=<nobody>
|
Group that winbind users have as their primary group
|
--winbindtemplateshell=</bin/false>
|
Shell that winbind users have as their default login shell
|
--enablewinbindusedefaultdomain
|
Configures winbind to assume that users with no domain in their usernames are domain users
|
--disablewinbindusedefaultdomain
|
Configures winbind to assume that users with no domain in their usernames are not domain users
|
--winbindjoin=<Administrator>
|
Joins the winbind domain or ADS realm as the specified administrator
|
--enablewinbindoffline
|
Configures winbind to allow offline login
|
--disablewinbindoffline
|
Configures winbind to prevent offline login
|
--smbsecurity=<user|server|domain|ads>
|
Security mode to use for the Samba and Winbind services
|
--smbrealm=<realm>
|
Default realm for Samba and Winbind services when security is set to
|
--enablewins
|
Enable Wins for hostname resolution
|
--disablewins
|
Disable Wins for hostname resolution
|
--enablesssd
|
Enable SSSD for user information
|
--disablesssd
|
Disable SSSD for user information
|
--enablecache
|
Enable nscd
|
--disablecache
|
Disable nscd
|
--enablelocauthorize
|
Local authorization is sufficient for local users
|
--disablelocauthorize
|
Local users are also authorized through a remote service
|
--enablesysnetauth
|
Authenticate system accounts with network services
|
--disablesysnetauth
|
Authenticate system accounts with local files only
|
--enablepamaccess
|
Check /etc/security/access.conf during account authorization
|
--disablepamaccess
|
Do not check /etc/security/access.conf during account authorization
|
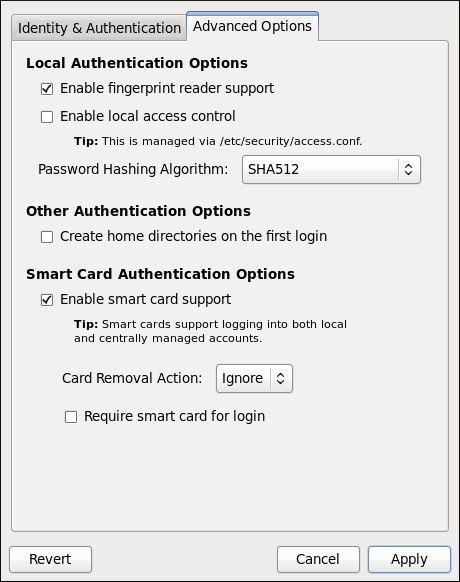
--enablemkhomedir
|
Create a home directory for a user on the first login
|
--disablemkhomedir
|
Do not create a home directory for a user on the first login
|
--enablesmartcard
|
Enable authentication with a smart card
|
--disablesmartcard
|
Disable authentication with a smart card
|
--enablerequiresmartcard
|
Require smart card for authentication
|
--disablerequiresmartcard
|
Do not require smart card for authentication
|
--smartcardmodule=<module>
|
Default smart card module to use
|
--smartcardaction=<0=Lock|1=Ignore>
|
Action to be taken when smart card removal is detected
|
--enablefingerprint
|
Enable fingerprint authentication
|
--disablefingerprint
|
Disnable fingerprint authentication
|
--nostart
|
Do not start or stop the portmap, ypbind, or nscd services even if they are configured
|
--test
|
Do not update the configuration files, only print the new settings
|
--update, --kickstart
|
Opposite of --test, update configuration files with changed settings
|
--updateall
|
Update all configuration files
|
--probe
|
Probe and display network defaults
|
--savebackup=<name>
|
Save a backup of all configuration files
|
--restorebackup=<name>
|
Restore a backup of all configuration files
|
--restorelastbackup
|
Restore the backup of configuration files saved before the previous configuration change
|