Copyright © 2006, 2007 Thomas M. Eastep
Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version published by the Free Software Foundation; with no Invariant Sections, with no Front-Cover, and with no Back-Cover Texts. A copy of the license is included in the section entitled “GNU Free Documentation License”.
2007/07/19
Table of Contents
Caution
This article applies to Shorewall 3.0.6 and later. If you are running a version of Shorewall earlier than Shorewall 3.0.6, you will need to upgrade to that version.
Caution
The technique described in this article will not work if you are running kernel 2.6.20 or later.
Xen is a paravirtualization tool that allows you to run multiple virtual machines on one physical machine. It is available on a wide number of platforms and is included in recent SUSE™ distributions.
Xen refers to the virtual machines as Domains. Domains are numbered with the first domain being domain 0, the second domain 1, and so on. Domain 0 (Dom0) is special because that is the domain created when to machine is booted. Additional domains (called DomU's) are created using the xm create command from within Domain 0. Additional domains can also be created automatically at boot time by using the xendomains service.
Xen virtualizes a network interface named eth0[1]in each domain. In Dom0, Xen also creates a bridge (xenbr0) and a number of virtual interfaces
as shown in the following diagram.
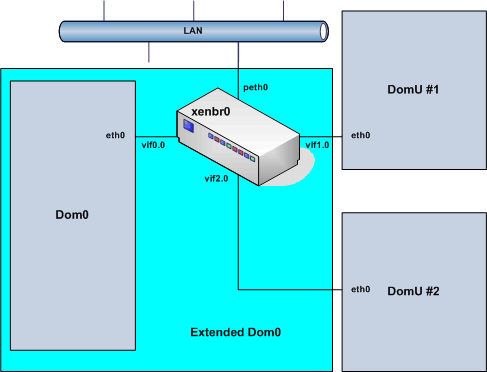
I use the term Extended Dom0 to distinguish the bridge and virtual interfaces from Dom0 itself. That distinction is important when we try to apply Shorewall in this environment.
The bridge has a number of ports:
peth0 — This is the port that connects to the physical network interface in your system.
vif0.0 — This is the bridge port that is used by traffic to/from Domain 0.
vifX.0 — This is the bridge port that is used by traffic to/from Domain X.
As I state in the answer to Shorewall FAQ 2, I object to running servers in a local zone because if the server becomes compromised then there is no protection between that compromised server and the other local systems. Xen allows you to safely run Internet-accessible servers in your local zone by creating a firewall in (the Extended) Dom0 to isolate the server(s) from the other local systems (including Dom0).
Caution
The Shorewall configuration shown in this article does not work with kernel 2.6.20 and later. For new Xen installations, I strongly recommend against a bridged Xen Domain 0 unless you run Shorewall in a DomU.
Caution
I find a bridged Xen Domain 0 to be an arcane environment in which to try to use Netfilter (and hence Shorewall). As the number of interfaces and bridges increase, complexity increases geometrically. I recommend following this guide only if you really need to place a public server in your local network. Otherwise, running Shorewall in a DomU is much more straight-forward as is running Shorewall in a routed Dom0.
Warning
I know of no case where a user has successfully used NAT (including Masquerade) in a bridged Xen Dom0. So if you want to create a masquerading firewall/gateway using Xen, you need to do so in a DomU (see how I did it) or you must configure Xen to use routing or NAT rather than the default bridging.
Here is an example. In this example, we will assume that the system is behind a second firewall that restricts incoming traffic so that we only have to worry about protecting the local LAN from the systems running in the DomU's.
Because Xen uses normal Linux bridging, you must enable bridge support in shorewall.conf
BRIDGING=Yes
One thing strange about configuring Shorewall in this environment
is that Dom0 is defined as two different zones. It is defined as the
firewall zone and it is also defined as "all systems connected to
xenbr0:vif0.0. In this case, I
call this second zone ursa (which was
the name given to the virtual system running in Dom0 when I ran this
configuration); that zone corresponds to Dom0 as seen from the outside
in the diagram above (see more below).
# OPTIONS OPTIONS fw firewall #Domain 0 ursa ipv4 #Domain 0 on the bridge dmz ipv4 #Server(s) running in Domains other than 0 net ipv4 #The local LAN and beyond #LAST LINE - ADD YOUR ENTRIES ABOVE THIS ONE - DO NOT REMOVE
We must deal with two network interfaces. We must deal with the (virtualized) eth0 and we must also deal with the bridge (xenbr0) created by Xen.
#ZONE INTERFACE BROADCAST OPTIONS - xenbr0 - dhcp net eth0 detect dhcp #LAST LINE -- ADD YOUR ENTRIES BEFORE THIS ONE -- DO NOT REMOVE
Here we define the zones ursa and dmz and we extend the definition of the zone net.
#ZONE HOST(S) OPTIONS ursa xenbr0:vif0.0 dmz xenbr0:vif+ routeback net xenbr0:peth0 #LAST LINE -- ADD YOUR ENTRIES BEFORE THIS LINE -- DO NOT REMOVE
Note that the net zone has two
different interfaces. From the point of view of Dom0 (which is where
Shorewall runs), the net zone comprises
everything except Dom0. From the point of view of the Extended Domain 0,
the net zone is everything connected
(directly or indirectly) to the peth0 port on the bridge.
The policies shown here effectively isolate Domains 1...N.
#SOURCE DEST POLICY LOG LIMIT:BURST # LEVEL all fw ACCEPT fw all ACCEPT ursa all ACCEPT net ursa ACCEPT net net NONE all all REJECT info #LAST LINE -- DO NOT REMOVE
These rules determine the traffic allowed into and out of the dmz zone.
# # "Net' to DMZ # ACCEPT net dmz udp domain ACCEPT net dmz tcp www,smtp,smtps,domain,ssh,imap,rsync,https,imaps,ftp,10023,pop3,3128 Trcrt/ACCEPT net dmz # # DMZ to 'Net' # ACCEPT dmz net:!192.168.0.0/22 udp domain,ntp ACCEPT dmz net:!192.168.0.0/22 tcp echo,ftp,ssh,smtp,whois,domain,www,81,https,rsync,cvspserver,2702,2703,8080 ACCEPT dmz net:$POPSERVERS tcp pop3 Ping/ACCEPT dmz net Ping/ACCEPT dmz ursa
Here, 192.168.0.0/22 comprises the local network.
From the point of view of Shorewall, the zone diagram is as shown in the following diagram.
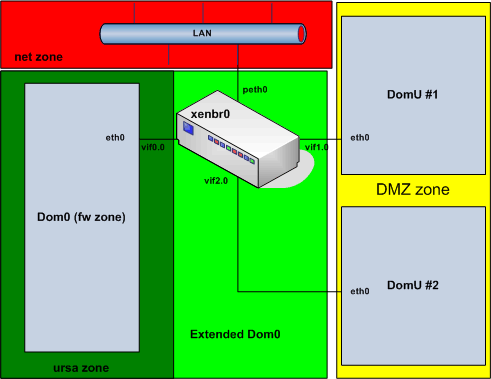
Note that the ursa zone subsumes the fw zone because the ursa zone is defined to be all systems that interface to xenbr0's vif0.0 port — it is the rules governing traffic to/from the ursa zone that protect the firewall in this configuration.
More elaborate configurations are possible as described in my Xen and the Art of Consolidation article.
[1] This assumes the default Xen configuration created by
xend and assumes that the host system has a single
ethernet interface named eth0.