Routing¶
Introduction to network routing¶
Zentyal uses the Linux kernel subsystem for the routing, configured using the tool iproute2 [1].
| [1] | http://www.policyrouting.org/iproute2.doc.html |
Configuring routing with Zentyal¶
Gateway¶
The gateway is the default router for the connections associated with a destination that is not in the local network. This means, if the system does not have static routes defined or if none of these matches with the desired transmission, we will use the gateway.
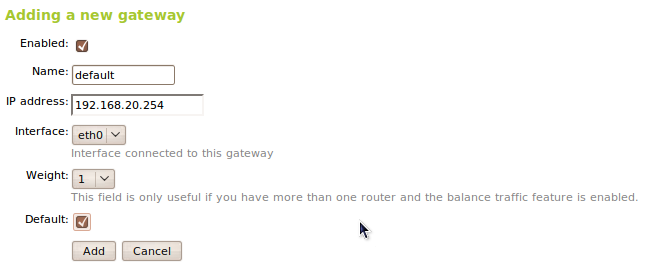
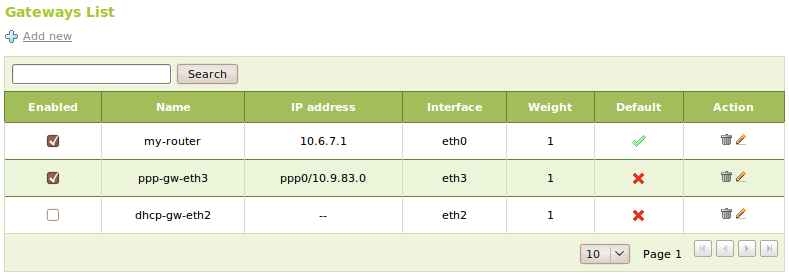
To configure a gateway in Zentyal we use Network ‣ Gateway, which has the following parameters.
- Enabled:
- Indicates whether this gateway is effectively working or if it is disabled.
- Name:
- Name we will use to identify the Gateway.
- IP Address:
- IP Address of the gateway. This address has to be directly accessible from the host that contains Zentyal, this means, without other routings in the middle.
- Interface:
- Network interface connected to the gateway. The packages sent to this gateway will be sent using this interface.
- Weight
- The higher the weight, more packages will be sent using this gateway if we have balance traffic enabled.
- Default
- If this option is enabled, this will be the default gateway.
If you have configured interfaces as DHCP or PPPoE [2] you can’t add a gateway explicitly for them, because they are automatically managed. Nevertheless, you can still enable or disable them editing the Weight or choose whether is it the Default, but it’s not possible to edit any other of the attributes.
Additionally Zentyal may need a proxy in order to access the Internet, for example for software and antivirus updates, or for the redirection of the proxy HTTP itself.
In order to configure this external proxy, we have to go to Network ‣ Gateways. Here we can specify the address for the Proxy server and also the Proxy port. We can specify a User and Password if the proxy requires it.
| [2] | http://en.wikipedia.org/wiki/PPPoE |
Static route table¶
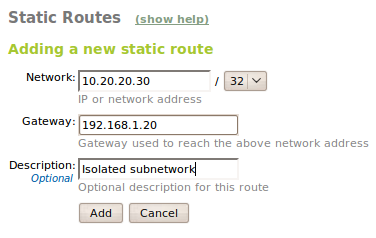
If we want all the traffic directed to a network to go through a specific gateway, we have to add a static gateway. This can be used, for example, to interconnect two local networks through their default gateways.
For making a manual configuration of a static route, we have to use Network ‣ Static Routes.
These routes can be overwritten if we use the DHCP protocol.
Configuring of the balancing with Zentyal¶
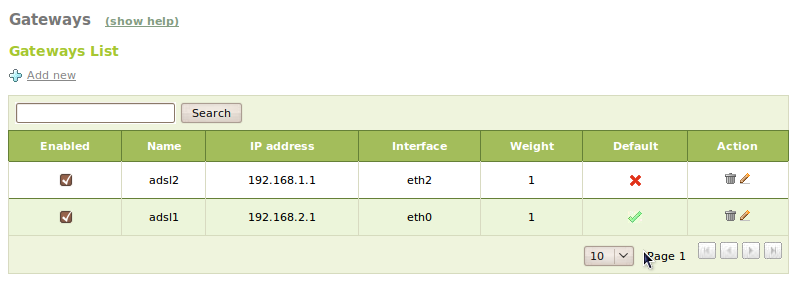
As we have mentioned previously, a single host can have more than one configured gateways, which leads to a situation where we have to take into account new parameters during the configuration of the Zentyal server.
The routing rules for more than one gateway, also known as multigateway rules allow the network to use multiple connections to Internet in a transparent way. This can be very useful for organization that require more bandwidth than what can be offered by a single ADSL line or that can not allow interruptions on their access to Internet, which is very common nowadays.
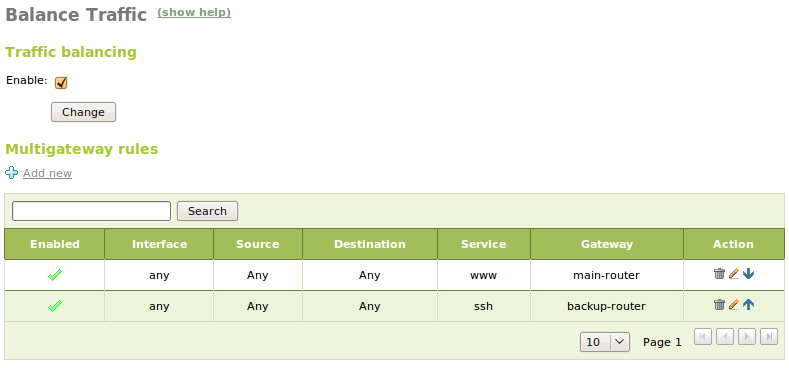
Traffic balancing shares the outgoing connections to the Internet in a equitable way, allowing to use completely the available bandwidth. The simplest configuration is to stablish the different weights for each gateway, so if the connections we have count with different capacities, we can do an optimal use.
Additionally, we can configure Zentyal to always send given types of traffic through a specific router if needed. A common example will be to send always the e-mail traffic or all the traffic of a determined subnet through a specific router
Multigateway rules and balancing can be stablish in the section Network ‣ Traffic balancing. In this section we can add rules to send certain connections to a specific gateway depending on the Interface, the source (It can be a IP address, one Object, the Zentyal server itself or Any), the destination (A IP adress or a Object), the Service to which we want to associate this rule and the Gateway where we want to route the specified traffic.
Configuring fault-tolerance in Zentyal¶
If we are performing traffic balancing between two or more gateways, it’s recommended to enable the fault-tolerance feature. In case we are balancing traffic between two routers and one of them suffers a failure, if we don’t have this feature enabled, part of the traffic will still try to use the non-functioning router, causing connectivity problems for the network users.
In the failover configuration it’s possible to define sets of test for each gateway to check whether it’s operative or if it’s having some problems and should no longer be used as an outgoing route to Internet. These tests can be a ping to the gateway, to an external host, DNS resolution or an HTTP request. You can also define how many tests are going to be executed and the percentage of acceptance required. If any test fail, not reaching acceptance rate, the associated gateway will be disabled. These tests will continue running, so when the acceptance rates are satisfied again, the gateway will be activated again.
Disabling a gateway makes that all the traffic will use the other gateways that are still enable, it will deactivate all the multigateway rules associated to this gateway and also consolidate the quality of service rules. This way, the network users should not suffer any problems with their Internet connection. Once Zentyal detects that the disabled gateway is operative again, it will restore the normal behaviour of the traffic balancing, multigateway rules and quality of service.
Failover is implemented as a Zentyal event. In order to use it, you first need to have the module Events enabled, and after this enable the event WAN Failover.
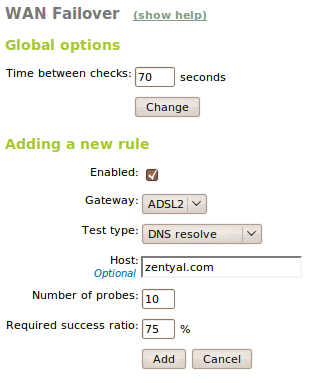
To configure the options and test for the failover you need to go to the menu Network ‣ WAN Failover. It is possible to specify the periodicity of the event modifying the value of the option Time between tests. For adding a rule we just have to click on the option Add new and we will see a form with the following fields:
- Enables:
- Indicates if the rule is going to be applied during the connectivity checks of the routers. It is possible to add different rules and enable or disable them depending of our need, without having to delete and add them.
- Gateway:
- We will select the gateway out of the lists of previously configured gateways.
- Type of test:
It can have one of the following values:
- Ping to gateway:
- It sends a control packet from the Zentyal server to the gateway and waits for a response, this way, it checks that there is connectivity between both hosts and that the gateway is active. It doesn’t check whether the gateway has Internet connection.
- Ping to host:
- Like the last type, this test send a control packet and waits for a response, but this time is to a external host, so we are not only testing the connection with the gateway, but also the Internet connection.
- DNS Resolution:
- We try to obtain the IP address for the specified host name, which requires not only connectivity between the server and the gateway and from this to the Internet but also, that the DNS servers are still accessible.
- HTTP Request:
- This could be the most complete test, considering that it tries to download the content of an specific web site, which requires all the former tests to be satisfactory.
- Host:
- The server that is going to be used as destination in the tests. Not applicable to Ping to gateway.
- Number of tests:
- Number of times we are going to repeat the test.
- Required success rate:
- Indicates which rate of successfully attempts we need to consider the test as ‘passed’.
With the default configuration, if any of this rules is activated, disabling a gateway, the event is only registered in the log file /var/log/ebox/ebox.log, if we want to receive notifications using other methods, we can configure an event emitter for this case, as we can learn in the chapter Events and alerts or also acquire a Zentyal Professional Subscription [3] which includes the automatic event sending.
| [3] | http://store.zentyal.com/serversubscriptions/subscription-professional.html |