

/usr/lib/libcoolkeypk11.so.
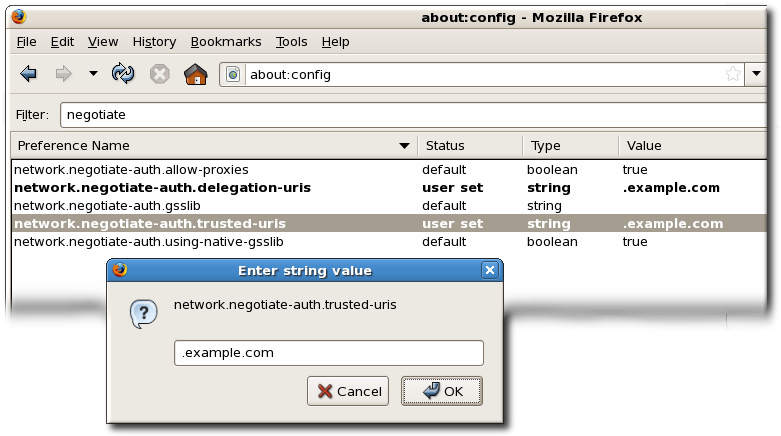
about:config to display the list of current configuration options.
negotiate to restrict the list of options.
kinit command and supply the user password for the user on the KDC.
[jsmith@host ~] $ kinit Password for [email protected]:
NSPR_LOG_* variables:
export NSPR_LOG_MODULES=negotiateauth:5 export NSPR_LOG_FILE=/tmp/moz.log
/tmp/moz.log file for error messages with nsNegotiateAuth in the message.
-1208550944[90039d0]: entering nsNegotiateAuth::GetNextToken() -1208550944[90039d0]: gss_init_sec_context() failed: Miscellaneous failure No credentials cache found
kinit to generate the Kerberos ticket and then open the website again.
-1208994096[8d683d8]: entering nsAuthGSSAPI::GetNextToken() -1208994096[8d683d8]: gss_init_sec_context() failed: Miscellaneous failure Server not found in Kerberos database
[domain_realm] section of the /etc/krb5.conf file to identify the domain. For example:
.example.com = EXAMPLE.COM example.com = EXAMPLE.COM