Securing data communication
To ensure security for the replicated information, configure a suitable VPN gateway between the two datacenters that encrypts the data between each route between datacenters.
When configuring XDCR across multiple clusters over public networks, the data is sent unencrypted across the public interface channel.
Within dedicated datacenters being used for Couchbase Server deployments, you can configure a point to point VPN connection using a static route between the two clusters:
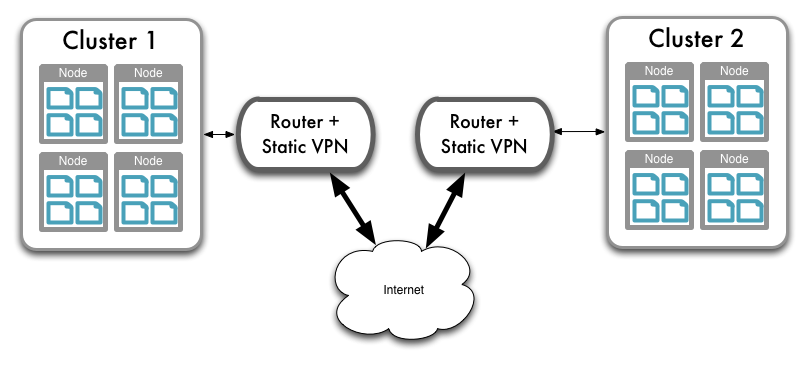
When using Amazon EC2 or other cloud deployment solutions, particularly when using different EC2 zones, there is no built-in VPN support between the different EC2 regional zones. However, there is VPN client support for your cluster within EC2 and Amazon VPC to allow communication to a dedicated VPN solution.
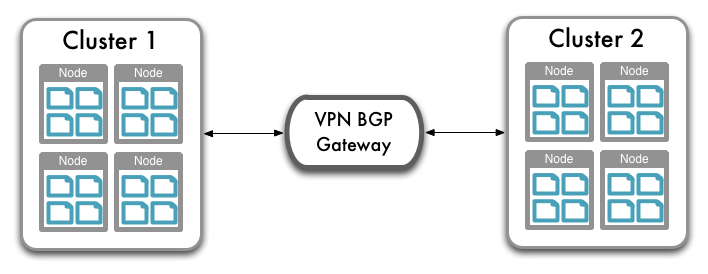
To support cluster to cluster VPN connectivity within EC2:
- Configure a multi-point BGP VPN solution that can route multiple VPN connections.
- Route the VPN connection from one EC2 cluster and region to the third-party BGP VPN router.
- Route the VPN connection from the other region, using the BGP gateway to route between the two VPN connections.
For additional security, configure your security groups to allow traffic only on the required ports between the IP addresses for each cluster. To configure security groups, specify the inbound port and IP address range. You will also need to ensure that the security also includes the right port and IP addresses for the remainder of your cluster to allow communication between the nodes within the cluster.