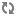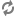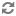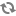Besides installing the corosync package, you will also have to
create a configuration file, stored in
/etc/corosync/corosync.conf. Most distributions ship an example
configuration file (corosync.conf.example) as part of the
documentation bundled with the corosync package. An example Corosync
configuration file is shown below:
Corosync configuration file (corosync.conf).
totem {
version: 2
# Time (in ms) to wait for a token  token: 10000
# How many token retransmits before forming a new
# configuration
token_retransmits_before_loss_const: 10
# Turn off the virtual synchrony filter
vsftype: none
# Enable encryption
token: 10000
# How many token retransmits before forming a new
# configuration
token_retransmits_before_loss_const: 10
# Turn off the virtual synchrony filter
vsftype: none
# Enable encryption  secauth: on
# How many threads to use for encryption/decryption
threads: 0
# This specifies the redundant ring protocol, which may be
# none, active, or passive.
secauth: on
# How many threads to use for encryption/decryption
threads: 0
# This specifies the redundant ring protocol, which may be
# none, active, or passive.  rrp_mode: active
# The following is a two-ring multicast configuration.
rrp_mode: active
# The following is a two-ring multicast configuration.  interface {
ringnumber: 0
bindnetaddr: 192.168.42.0
mcastaddr: 239.255.42.1
mcastport: 5405
}
interface {
ringnumber: 1
bindnetaddr: 10.0.42.0
mcastaddr: 239.255.42.2
mcastport: 5405
}
}
amf {
mode: disabled
}
service {
# Load the Pacemaker Cluster Resource Manager
interface {
ringnumber: 0
bindnetaddr: 192.168.42.0
mcastaddr: 239.255.42.1
mcastport: 5405
}
interface {
ringnumber: 1
bindnetaddr: 10.0.42.0
mcastaddr: 239.255.42.2
mcastport: 5405
}
}
amf {
mode: disabled
}
service {
# Load the Pacemaker Cluster Resource Manager  ver: 1
name: pacemaker
}
aisexec {
user: root
group: root
}
logging {
fileline: off
to_stderr: yes
to_logfile: no
to_syslog: yes
syslog_facility: daemon
debug: off
timestamp: on
logger_subsys {
subsys: AMF
debug: off
tags: enter|leave|trace1|trace2|trace3|trace4|trace6
}
}
ver: 1
name: pacemaker
}
aisexec {
user: root
group: root
}
logging {
fileline: off
to_stderr: yes
to_logfile: no
to_syslog: yes
syslog_facility: daemon
debug: off
timestamp: on
logger_subsys {
subsys: AMF
debug: off
tags: enter|leave|trace1|trace2|trace3|trace4|trace6
}
}
The | |
With | |
In Corosync configurations using redundant networking (with more
than one | |
There are several things to note about the recommended interface configuration:
| |
The |
Once created, the corosync.conf file (and the authkey file if the
secauth option is enabled) must be synchronized across all cluster
nodes.