Managing XDCR data encryption
The cross data center (XDCR) data security feature (Enterprise Edition only) provides secure cross data center replication using Secure Socket Layer (SSL) data encryption. The data replicated between clusters can be encrypted in both uni-directional and bi-directional replications.
XDCR data encryption prerequisites
- Couchbase servers on both source and destination clusters must have Couchbase 2.5 Enterprise Edition and above installed.
- The source cluster must use the destination cluster’s certificate. The certificate is a self-signed certificate used by SSL to initiate secure sessions.
- The reserved ports for XDCR data encryption must be available.
With XDCR data encryption, the following ports are reserved:
| Port | Description |
|---|---|
| 11214 | Incoming SSL Proxy |
| 11215 | Internal Outgoing SSL Proxy |
| 18091 | Internal REST HTTPS for SSL |
| 18092 | Internal CAPI HTTPS for SSL |
To enable XDCR data security
To enable XDCR data security using SSL and create replication:
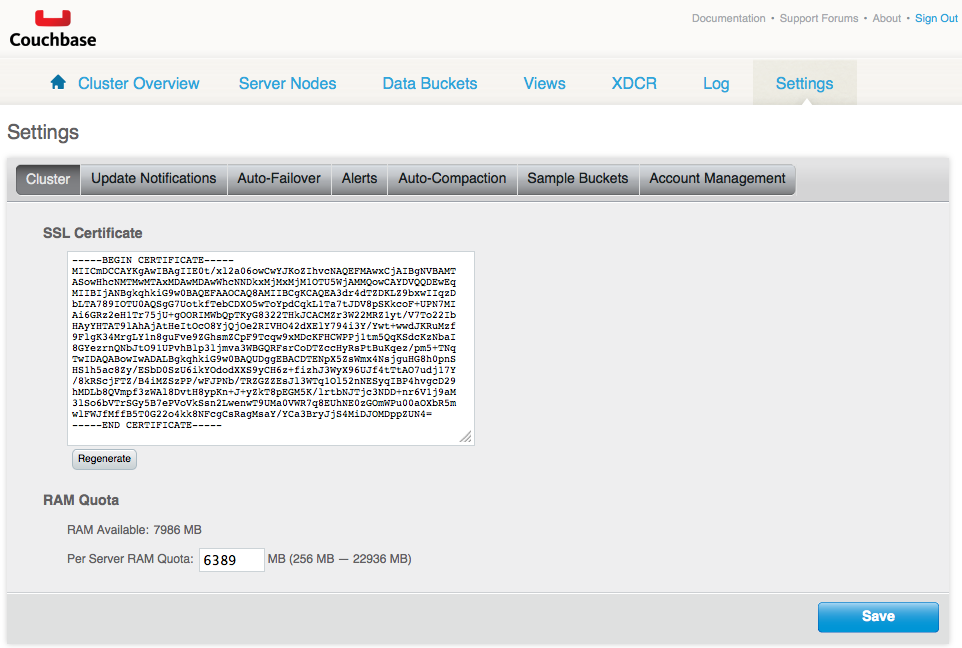
- On the destination cluster, navigate to Settings > Cluster and copy the
certificate.
- (Optional) To regenerate the existing destination certificate, click Regenerate before copying.
- On the source cluster, select the XDCR tab.
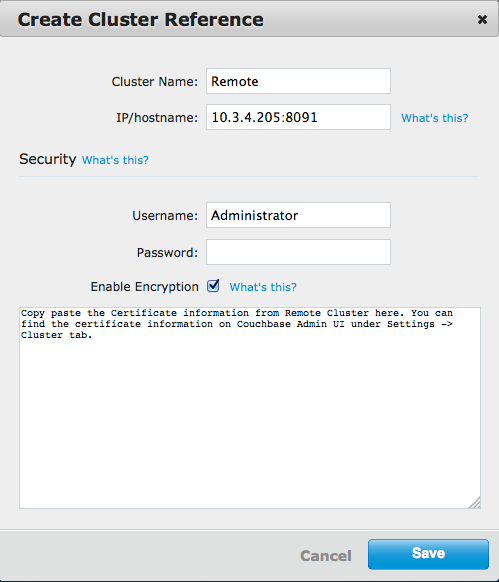
- On the Remote Clusters panel, click Create Cluster Reference to verify or create the cluster reference.
- Select the Enable Encryption box and paste the certificate in the provided area and click Save.
- On the Ongoing Replications panel, click Create Replication, provide the cluster and bucket information, and click Replicate.
To change XDCR data encryption
In some situations (such as updating SSL data security), the SSL certificate is regenerated and the XDCR data encryption is updated. To change XDCR data encryption:
- On the destination cluster, navigate to Settings > Cluster.
- Click Regenerate and copy the certificate.
- On the source cluster, select the XDCR tab.
- On the Remote Clusters panel, for the destination cluster, click Edit.
- Paste the regenerated certificate in the provided area and click Save.
Anytime a destination cluster’s certificate is regenerated, the corresponding source cluster(s) must be updated with the regenerated certificate.
For example, if source clusters A, B, and C use XDCR data encryption to replicate to destination cluster D, each of the source clusters must be updated whenever the certificate on the destination cluster D is regenerated (changed).
Important
If a destination cluster's certificate is regenerated and the source cluster(s) are not updated with the new certificate, replication stops.
SSL certificate
The following is an example of an SSL certificate and where the certificate is obtained on the cluster.
Create Cluster Reference
The following is an example of the Create Cluster Reference pop-up.
XDCR data security error messages
When creating the cluster reference, if the SSL certificates are not the same on the destination and source clusters, the following error message displays:
Attention - Got certificate mismatch while trying to send https request to HOST:18091
If the SSL certificates become mismatched (for example, if the certificate on the destination cluster is regenerated and the source cluster is not updated with the new certificate), vBucket replication stops and the following error message displays:
Error replicating vbucket <bucketNumber>. Please see logs for details.