19. Asset Management
The GSM can store all results of all scans in the Asset-Management.
When defining a task it can be determined if the results of a scan should be recorded in the asset management (see section Creating a Task).
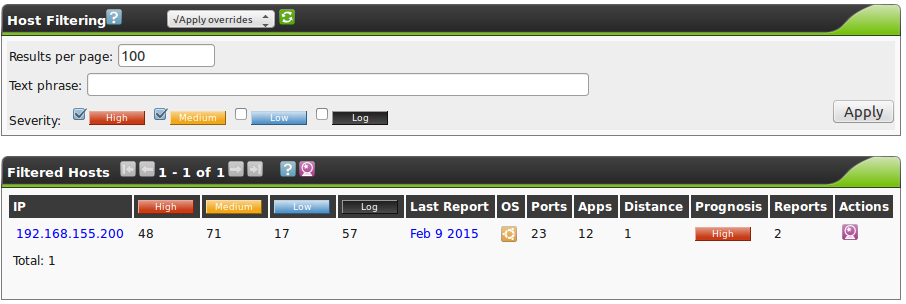
To begin with, in the overview all the systems stored in the asset management can be viewed.
Here you can see how many security holes were discovered on the systems.
In addition the overview displays the operating system with a logo (OS column) and the discovered ports and applications.
Also it is being displayed how a scan of the system would possible turn out in this moment (Prognosis column, see also section Prognosis).
Via the  a prognostic report can be created as well.
Through the asset management you can always access the last report of the host.
The date of the report is visible and can be accessed directly by clicking on the link.
If multiple reports exist older reports can be accessed in the host details.
By clicking on the host IP address the host details can be accessed.
Here the amount of discovered vulnerabilities, the identified operating system, the discovered ports and the amount of detected applications on the system can be viewed
a prognostic report can be created as well.
Through the asset management you can always access the last report of the host.
The date of the report is visible and can be accessed directly by clicking on the link.
If multiple reports exist older reports can be accessed in the host details.
By clicking on the host IP address the host details can be accessed.
Here the amount of discovered vulnerabilities, the identified operating system, the discovered ports and the amount of detected applications on the system can be viewed
The host details contain additional information of the system:
- Hardware:
- The GSM stores information about the hardware.
If known then the MAC address is listed here.
It can only be displayed though if the target system is on the same LAN as the GSM.
- Detected Applications:
- Especially of interest are the detected applications.
With this the Greenbone Security Manager can give a prognosis based on its SecInfo database without re-scanning if additional security risks would be found.
This is especially of interest for systems that currently do not have any vulnerability and new scans are not being performed regularly.
19.1. Prognosis
The prognosis allows to forecast possible security risks without a new scan based on current information about known security holes from the SecInfo Management (SCAP, Security Content Automation Protocol) (see chapter SecInfo Management).
This is especially interesting for environments where by the use of the GSM most vulnerabilities have been removed or remediated.
Of course new vulnerabilities are being discovered daily.
Not every vulnerability justifies a new scan of the network or of individual systems.
Due to the fact that the GSM has this information, based on the knowledge of the detected applications it can make a prognosis which security risks exist.
If security risks become known it justifies the actual running of a scan to verify the prognosis.
For this the asset database requires current data of course.
This is why a scan of the systems should occur regularly in weekly or monthly intervals.
A prognostic scan can be performed as well.
It will determine probable existing vulnerabilities