This chapter covers the operation of the Greenbone Security Manager Appliance and looks at the most important aspects that could be encountered during operation.
This chapter highlights first steps of user management.
In addition, the upgrade of the appliance directly via the Internet as well as via Airgap mode are discussed.
Finally, the backup and restoring of data are topics of this chapter.
6.1. User management
The Greenbone Security Manager user management allows for the definition and management of different users with different roles and permissions.
When initializing the GSM appliance the first user (web/scan user respectively) is being set up via the GOS-Admin-Menu.
This user allows the login and management of additional users.
The GSM user management supports a role based permission concept when accessing the web interface.
Some roles are set up by default.
However, other roles can be created and used by an administrator.
The role defines which functions within the web interface a user is allowed to view and modify.
The roles are not put in effect in the web interface rather than in the underlying OMP protocol and as such have an impact on all OMP clients.
Read and modifying access can be assigned to roles separately.
Aside from roles the GSM user management supports groups as well.
Groups allow the aggregation of users.
This is mainly used for logical grouping.
Aside from the management of permissions through roles, groups can also be assigned specific permissions.
Additionally, through user management every user can be assigned a range of IP addresses of which scanning is allowed or prohibited.
The GSM appliance then denies a specific user the scanning of IP addresses other than the ones specified.
Access to specific adapters of the GSM appliance can be allowed or denied.
The Greenbone Security Manager offers its own user management for the management of the roles and specific permissions of the users.
In order not to have to manage multiple passwords and to allow for password synchronization the Greenbone Security Manager allows for integration with a central LDAP server.
It will only be used for the verification of the password of the user during log in.
All other settings are performed in the user management of the GSM appliance.
The following sections cover the creation of individual users.
The management of the permissions, groups and roles is covered in chapter User and Permission Management.
6.1.1. Creating and Managing Users
The dialog for creating and managing users can be accessed via the menu Administration.
This menu is only visible to administrators since only they are allowed to create and manage users initially.
Here the dialog for the creation of a new user can be started by clicking on the white star on blue background  or a user can be modified by clicking on the wrench icon.
or a user can be modified by clicking on the wrench icon.
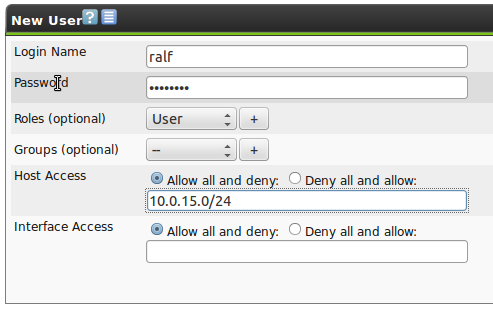
When creating a user the following settings are possible:
Login Name:
This is the name the user logs in with.
If an LDAP server is used for central password management, the user needs to be created with the identical name (rDN) as in the LDAP server.
The name can be a maximum of 80 characters and can contain letters and numbers.
Password:
This is the password for the user.
The password can be a maximum of 40 characters and can contain any type of character.
Please note when using special characters that they are available on all keyboards and operating systems in use.
Roles (optional):
Each user can have multiple roles.
The roles define the permissions of a user when using the OMP protocol.
Since the Greenbone Security Assistance utilized the OMP protocol the roles define directly the features in the web interface.
While it is possible to add and configure additional roles, at the beginning some default roles are available.
These roles are discussed in more detail in section User Roles.
Groups (optional):
Each user can be a member of multiple groups.
Permissions management can be performed via groups as well (see section Permissions).
Host Access:
Here it can be defined which systems a specific user can analyze in a scan and which systems should not be considered in a scan.
These restrictions can also be set up for administrators.
They can, however, remove these restrictions again themselves.
This is why this function is simply a self-protection for administrators.
Normal users (User) and roles without access to the user management respectively cannot circumvent this restriction.
Basically it can be chosen between a whitelist (deny all and allow) and a blacklist (allow all and deny).
In the first case the scanning of all systems is denied in general and only explicitly listed systems are allowed to be scanned.
In the latter case the scanning of all systems is allowed except the listed systems.
System names as well as IPv4 and IPv6 addresses can be entered.
Furthermore individual IP addresses as well as address ranges and network segments can be specified.
The following listing shows some examples:
- 192.168.15.5 (IPv4 address)
- 192.168.15.5-192.168.15.27 (IPv4 range long form)
- 192.168.15.5-27 (IPv4 range short form)
- 192.168.15.128/25 (CIDR notation)
- 2001:db8::1 (IPv6 address)
- 2001:db8::1-2001:db8::15 (IPv6 range long form)
- 2001:db8::1-15 (IPv6 range short form)
- 2001:db8::/120 (CIDR notation)
All options can be mixed and matched and entered as a comma separated list.
The netmask in the CIDR notation is restricted however to a maximum of 20 for IPv4 and 116 for IPv6.
In both cases the result is a maximum of 4096 IP addresses
Interface Access:
Here it can be specified which network adapter a user can run a scan on.
A comma separated list of network adapters can be entered and similar to the Host Access it can be chosen between a whitelist and blacklist methodology.
Tip
In general the whitelist methodology should be used and scans of systems denied except for the chosen systems.
This is to ensure that users do not scan systems by accident or unknowingly that are outside of their responsibility, are located somewhere on the Internet or react critical to a scan.
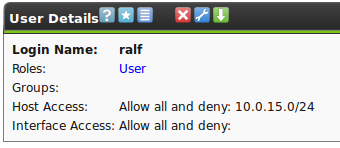
After creating the user the user’s properties are displayed.
The display should be verified to ensure that the user does not have too many permissions assigned to him.
6.2. Upgrade
As part of your subscription Greenbone provides upgrades for the GSM appliance.
The upgrades are provided regularly.
Users can decide if an upgrade should be applied.
The given numbers are based on the release data from the last 5 years as well as based on experience of the Support Team when helping customers to execute an upgrade.
There are three different kinds of updates:
- Patch-Level upgrade (i.e. from version 3.0.16 to 3.0.17)
- ca. 1 per month
- some recommended, some critical (security)
- 10 min per Master-GSM
- Release upgrade (i.e. from version 3.0.16 to 3.1.0)
- ca. 1-2 per year
- upon preference or due to End-of-Life
- 2-6 hours (depending on whether it is necessary to adjust configuration due to functionality changes and whether users need to be trained about the changes)
- LTS Release upgrade
- ca. 1 per 2 years
- required due to End-of-Life
- ca. 1-2 days (depending on whether it is necessary to adjust configuration due to functionality changes and whether users need to be trained about the changes)
- Generation Upgrade (i.e. from version 2.2.9 to 3.1.0)
- ca. 1 per 2 years
- upon preference or due to End-of-Life
- ca. 1-2 days (depending on whether it is necessary to adjust configuration due to functionality changes and whether users need to be trained about the changes)
These upgrades are not being performed automatically.
The user has to invoke the upgrades manually.
 The upgrade steps are also explained in a video at http://docs.greenbone.net/Videos/gos/en/GSM-Upgrade-en-20150703.mp4.
The upgrade steps are also explained in a video at http://docs.greenbone.net/Videos/gos/en/GSM-Upgrade-en-20150703.mp4.
If there are Master-GSMs as well as Slave-GSMs in the environment the following information is important:
- Sensors are being updated automatically by the master.
- Slaves must be updated manually.
The masters should be updated first and then the slaves.
It works this way under Airgap operation as well.
- Two GSMs with different patch levels can work together.
However, this is not supported.
- Different release versions on master and slave are not possible!
6.2.1. Checking the Current Version
To check the current version all that is required is to connect to the GSM appliance.
A log in is not even required.
The welcome message of the GSM lists the current version in its banner.
Alternatively executing the command softwareversion produces the same output.
Welcome to the Greenbone OS 3.1.6 running on a Greenbone Security Manager
Web Interface available at : https ://192.168.155.100
gsm login :
The log in screen of the web interface can also be checked.
The version is displayed at the bottom right as well.
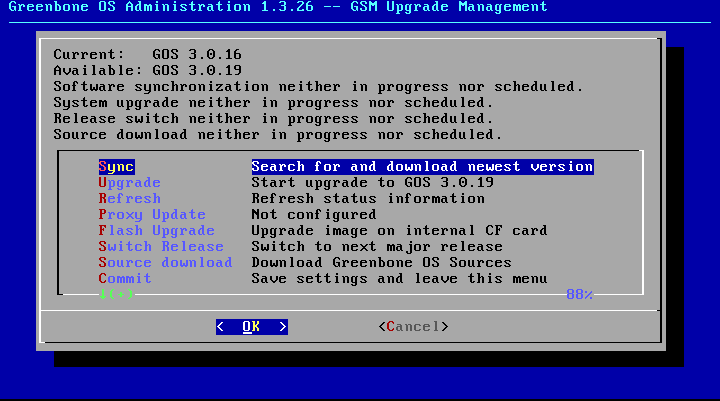
Alternatively after logging in using the command line via SSH for example, the version can be checked in the GOS-Admin-Menu.
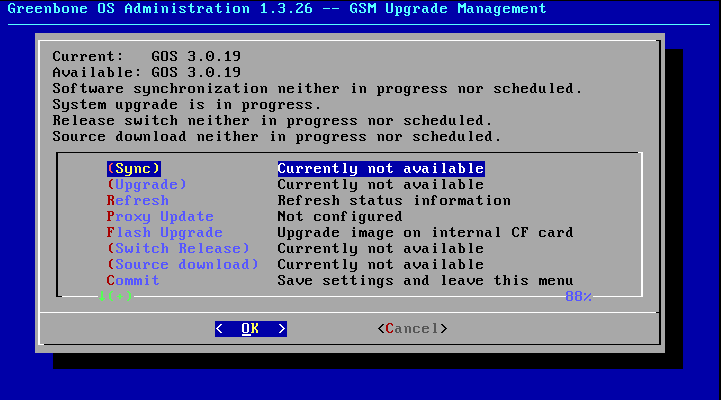
Under Upgrade it can be checked directly if an newer version is available.
The current installed version can be displayed with Current.
Available displays the latest version downloaded from the Greenbone feed server during last feed synchronisation.
Under menu option Sync available versions on the Greenbone servers can be checked and a possible installation can be downloaded.
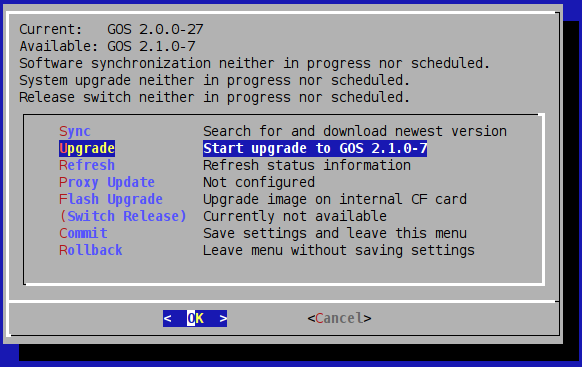
6.2.3. Release Upgrade
A release change is not being indicated in the GOS-Admin-Menu.
A release change is announced by Greenbone via Newsletter and on the web site.
Select the menu option Switch Release in the GOS-Admin-Menu.
After a warning message the available release is displayed and is being downloaded from the Greenbone Feed servers.
This process can take up to an hour depending on the Internet connection.
Afterwards a new version for upgrade is being offered in the GOS-Admin-Menu and the release change is preformed along the same lines as a Patch-Level upgrade.
To complete a reboot is required.
The upgrade can also take a couple of hours.
While upgrading no scans should be running or being started.
6.2.4. Use of Proxies
In case the GSM appliance cannot access the Internet directly and requires the use of a proxy, it must be stored on the GSM appliance.
Start the GOS-Admin-Menu and select the Feed option.
Then select the option Proxy Feed.
Here the proxy can be entered.
Make sure that a valid HTTP-URL is used.
Names as well as IP address can be used.
http://proxy.mycompany.com:3128
http://192.168.15.5:3128
To enter proxy credentials select Credentials in the same menu.
This proxy configuration will be used for the feed updates as well as for the software updates.
6.3. Backup and Restore
Regularly backing up the GSM appliance and the created data ensures fast restoration of operation of a new appliance, should the appliance have to be replaced by Greenbone after a failure of the appliance.
Moreover, to be safe a backup of the system should be done prior to every update.
Three different ways of backup are available:
- Backup of the entire system (SystemBackup)
- Snapshot of the entire system (SystemSnapshot)
- Backup of the created and changed data (user data).
This includes all created scan configurations, users, overrides and so on.
A backup of the entire system prior to every update of the GSM appliance is recommended.
This ensures the GSM appliance can be returned to its original state should the update fail.
A backup of the user data should be performed regularly.
With this backup it is possible to restore your configurations after an exchange by Greenbone should the appliance have failed.
Additionally this backup is recommended prior to every update.
The following sections cover the individual steps.
6.3.1. Backup of the entire system
The way the backup of the entire system is performed depends on the appliance in use.
The GSM ONE and GSM 25V are virtual appliances.
It is very simple to utilize the backup functionalities of the hypervisor.
The hypervisor, for example, supports the snapshot functionality that allows to backup and if needed the restoring, of the current state of the running system.
The GSM 25 and GSM 100 do not support the backup of the entire system.
All other appliances (GSM 500 and up) come with a backup partition.
The backup partition can store exactly one complete backup of the appliance.
An incremental backup or the provisioning of other types is not supported.
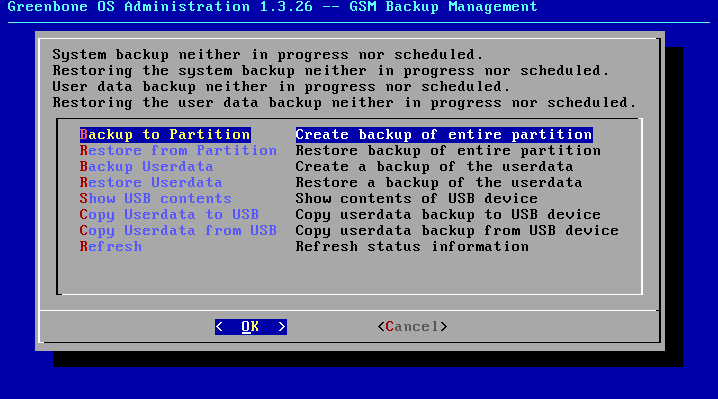
To perform a complete backup start the GOS-Admin-Menu from the console.
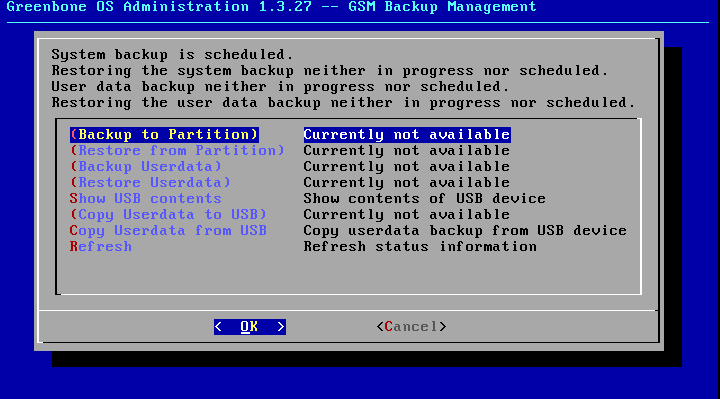
Select the menu option Backup.
The menu being displayed has the options Create System Backup and Restore System Backup.
Create System Backup start the backup process.
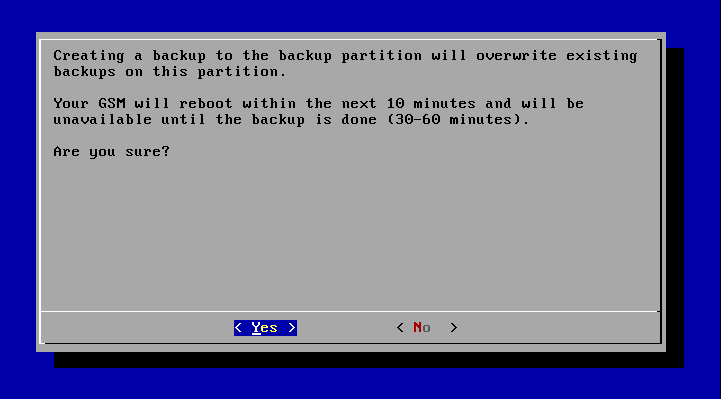
Afterwards the GSM appliance will reboot within the next 10 minutes (often immediately) and the system is backed up to the backup partition.
This process can take about 30-60 minutes.
A respective maintenance window is required and before starting the backup the process has to be confirmed.
While the appliance waits to reboot other menu options in the backup menu are no longer available.
Restoring the GSM appliance from a complete backup is also performed with the assistance of the GOS-Admin-Menu.
Select the menu option Restore from Partition.
A maintenance window of 30-60 minutes is also required and the appliance performs a reboot.
The process needs to be confirmed as it could cause data loss.
Note
If, since the last backup, there have been changes to user data, new scan configurations, tasks or overrides, they will be overridden.
If in doubt user data should be backed up before restoring!
6.3.2. Snapshot of the System
The snapshot backup is another alternative to backing up the entire system.
The system snapshot is only available with certain appliances (i.e. 5xx but not 6xx).
Both the system backup as well as the system snapshot creates a complete backup of the partition.
However both of the backups don’t override each other.
This means that practically two (backup) states can be stored (with one GSM 5xx).
A GSM 600 only the system backup is possible for example.
To start the creation of a snapshot change to the command line and enter the command systemsnapshot.
Afterwards the GSM appliance will boot and create the snapshot.
With the GSM 5xx a snapshot backup as well as a system backup can be created.
Restoring of a system snapshot backup is done via the Grub boot menu.
Connect to the system vie serial port or a VGA monitor.
Perform a reboot.
In the grub menu (before the GOS boot) a menu option Snapshot Backup should be displayed.
Select this option.
The system now boots into the snapshot.
6.3.3. Backup of User Data via USB-Stick
Backing up of user data is performed on all GSM appliances in the same way.
The GSM appliance supports first of all the backup of the user data to the GSM appliance itself.
The file created can be copied to a USB key or a separate SSH server afterwards.
This way the data will still be available when the appliance fails.
To save the data to an external USB key two steps are always required:
- Backup of the user data
- Copying of the backup to the USB key
The same process is performed backwards when restoring the user data.
First the user data is copied from the USB key or the SSH server to the appliance.
Then the data can be restored.
The following covers the individual steps.
 These backup steps are also explained within the following video covering upgrades: http://docs.greenbone.net/Videos/gos/en/GSM-Upgrade-en-20150703.mp4.
These backup steps are also explained within the following video covering upgrades: http://docs.greenbone.net/Videos/gos/en/GSM-Upgrade-en-20150703.mp4.
First, log into the appliance, for example, via SSH.
The start the GOS-Admin-Menu and select the menu option Backup.
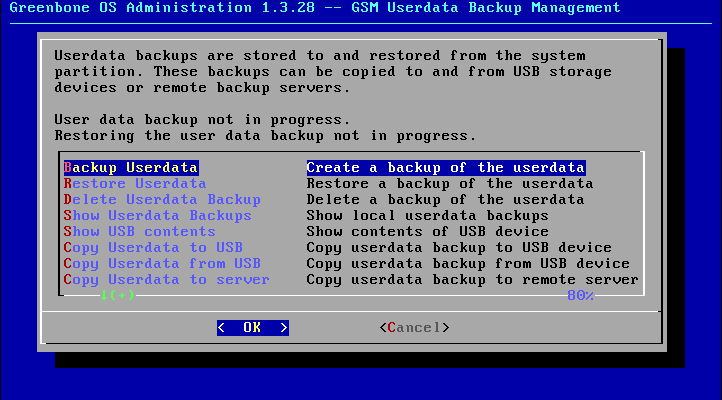
After selecting the option Userdata Backup the menu options concerning the Userdata Backup are available. While the actual Userdata backup is in progress the other options will be blocked until the backup is complete.
Otherwise the system can be used as usual.
A maintenance window is not required.
A reboot is not performed either.
Opposite to the complete backup multiple versions of user data backups can be stored on the appliance.
They are being saved by name with the following pattern:
<gsf-number>-<date><time>.gsmb
201309161-201406180807.gsmb
On the appliance the backups are stored in the folder /var/gsm/backups/userdata/.
The stored user data can now be copied to a USB key or a SSH server.
The USB key has to be partitioned and contain exactly one primary partition formatted in VFAT file system.
This is the factory default with most USB keys.
After inserting the USB key wait for a couple of seconds until the GSM appliance recognized the USB key.
Then you can display the contents of the USB key with the menu option Show USB contents.
The execution of the command can take a couple of seconds.
Now the user data can be copied to the USB key.
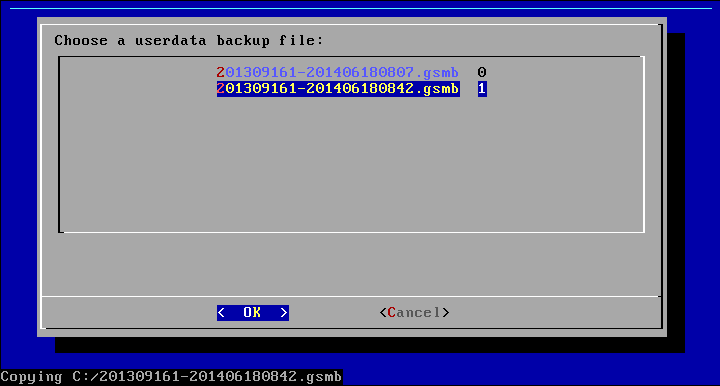
Select the menu option Copy Userdata to USB.
Afterwards you can select the backup to be copied.
Should the file already exist in the USB key, you will be asked if the file should be renamed, overridden or skipped:
Long file name "201309161 -201406180807. gsmb " already exists .
a) utorenmae A) utorename - all r) rename R) ename - all o) verwrite O) verwrite - all
s) kip S) kip q) uit ( aArRoOsSq ):
After the files are copied to the USB key the contents can be displayed again (see After the copy process the data was transferred.).
Afterwards the USB key can be unplugged.
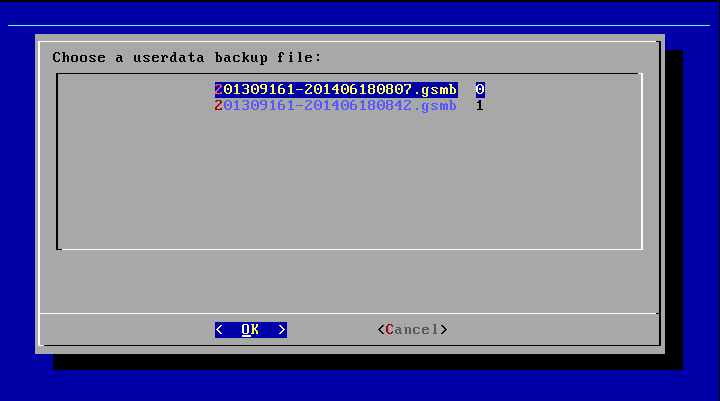
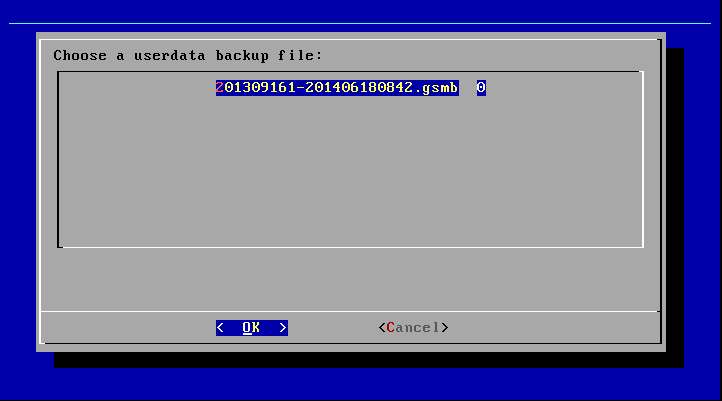
To restore the data from the USB key, in the GOS-Admin-Menu select the menu option Backup followed by the option Copy Userdata from USB.
After a couple of seconds the selection of available backups on the USB key is displayed.
After confirming a version with OK, it will be copied to the GSM appliance.
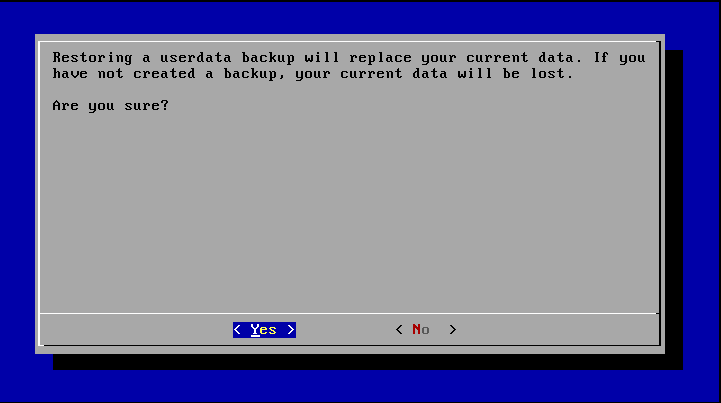
Afterwards the user data can be restored with Restore Userdata.
There will be a warning message that when restoring the old data the current data will be erased.
This is possible if you want to backup it up.
However, merging of user data backups is not possible.
Tip
If you want to backup only individual information such as a scan configuration you can export it via the web interface and import it onto another appliance as well!
6.3.4. Backup of User Data via SSH
Backing up of user data can also be performed via SSH.
This requires a SSH access on a remote system.
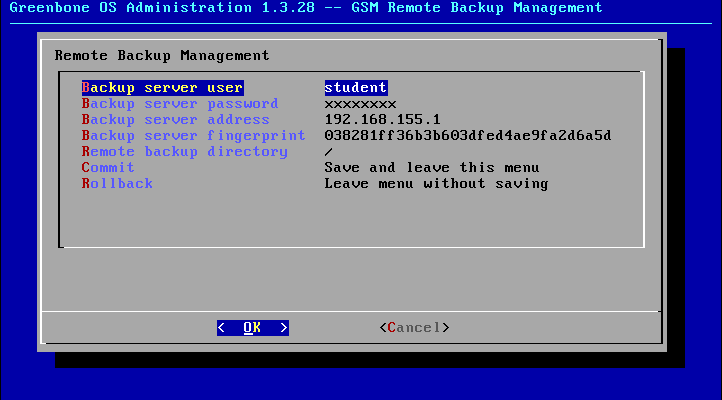
To configure the remote backup via SSH you need to use gos-admin-menu and access menu Backup and there Configure Server.
There you need configure the following items:
- Backup server user
- This is the username to be used to log into the remote system and transfer the backup.
- Backup server password
- This is the password for the specified user.
- Backup server address
- This is the IP address of the backup server.
- Backup server fingerprint
- Here you have to enter the MD5 checksum of the hostkey of the backup server.
You can find out about the MD5 checksum by executing the following command on the backup server.
This fingerprint must be entered without colons (see figure The identify of the backup server is checked via the fingerprint of the hostkey.).
ssh-keygen -l -f /etc/ssh/ssh_host_rsa_key.pub
2048 03:82:81:ff:36:b3:b6:03:df:ed:4a:e9:fa:2d:6a:5d root@station100 (RSA)
- Remote backup directory
- Here you can change the directory where the backup will be stored on the remote system.
Now you have to create and copy a user data backup with Userdata Backup.
An automatic execution of the remote backup is not yet possible.
6.4. Airgap Update
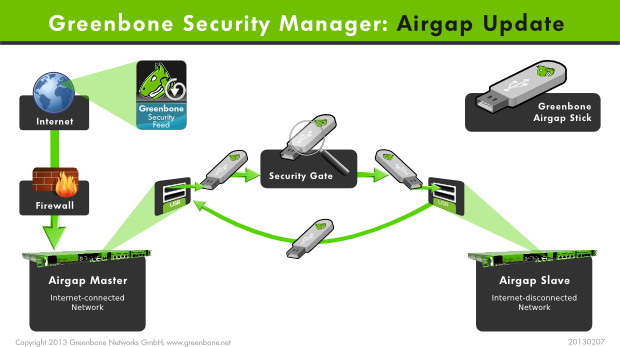
The Airgap function allows a GSM appliance that is not directly connected to the Internet with updates of feeds and updates nonetheless.
Two GSM appliances are required.
One of these appliances is situated in a secured area and does not have any connectivity to the Internet.
The second appliance has to be connected to the Internet.
For the Airgap function two options are available:
- Greenbone Airgap USB key
- Airgap FTP Server
Both options are covered in the following sections.
Note
Please refer to the GSM model overview (GSM Overview), section GSM Networks to check which models support the Airgap feature.
6.4.1. Airgap via USB key
The feeds and updates are loaded from an appliance that is connected to the Internet and copied to a USB key.
It then can be used to update the second appliance.
The USB key can be checked for malware by a security gateway beforehand.
After setting up the of the Airgap functionality no log in onto the appliances is required.
The communication happens entirely through the LCD display and can be performed by any personnel.
Once a day they only have to remove the USB key from the Airgap master and insert it into the airgap slave.
After a few minutes they will be asked on the display to remove the USB key from the Airgap slave again and insert it into the Airgap master.
The Airgap function can only be used with special USB keys provided by Greenbone.
Contact Greenbone providing your customer number to request a respective USB key.
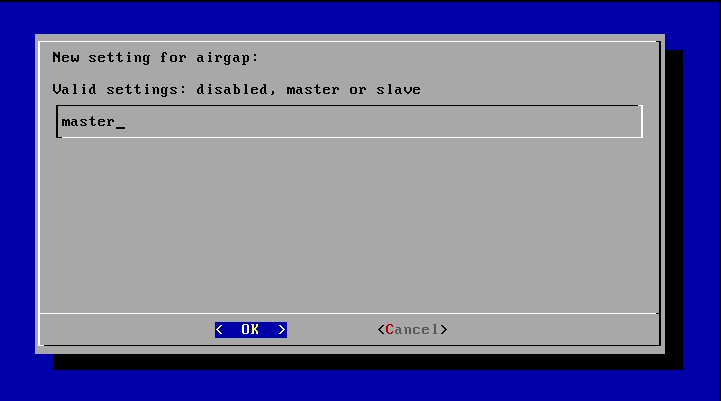
To use the Airgap function with the respective key, the GSM appliance needs to be configured respectively and the roles of Airgap master and Airgap slave need to be assigned.
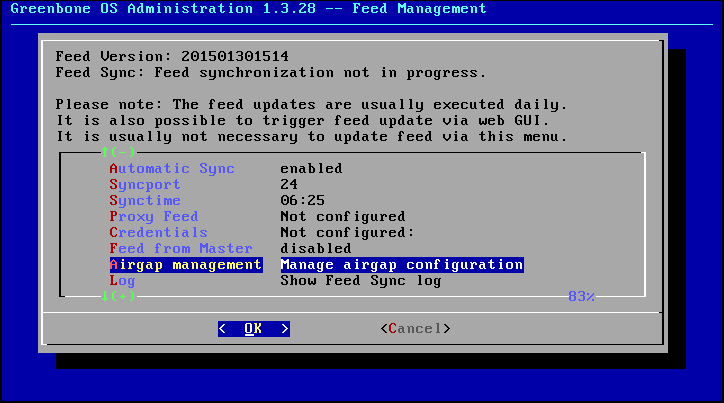
Start the GOS-Admin-Menu and change into the menu Feed.
Scroll to the menu option Airgap management and select it.
Enter in the role the respective role in the process either master or slave.
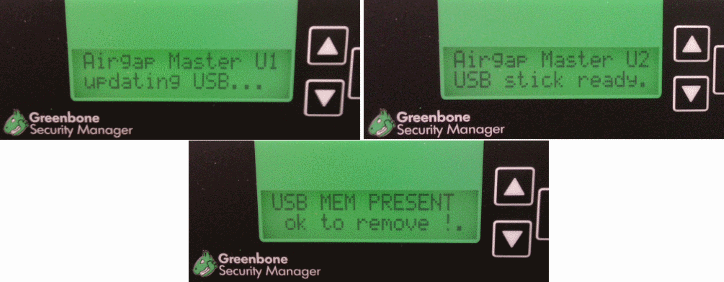
The master is now building a special update package during every daily update and will save it to the USB key.
The process can be followed on the display.
When the master is updating, it will display the messages Airgap Master U1 updating USB... and Airgap Master U2 USB stick ready. one after the other.
A soon as the master displays USB MEM PRESENT ok to remove!. the USB key can be removed and transferred to the slave.
The slave recognizes the USB key automatically and loads the update from the USB key.
The display displays the message Airgap Slave DL1 updating from USB. and Airgap Slave S0 ........
As soon as the message USB MEM PRESENT ok to remove!. is being displayed also, the USB key can be removed and inserted back into the master.
6.4.2. Airgap via FTP
Alternatively the feed updates can be provided via their own FTP server.
The FTP server takes on the function of the USB key.
Two GSMs are required as well:
- The master picks up the feed from the Internet and writes it to the FTP server.
- The slave downloads the feed from the FTP server.
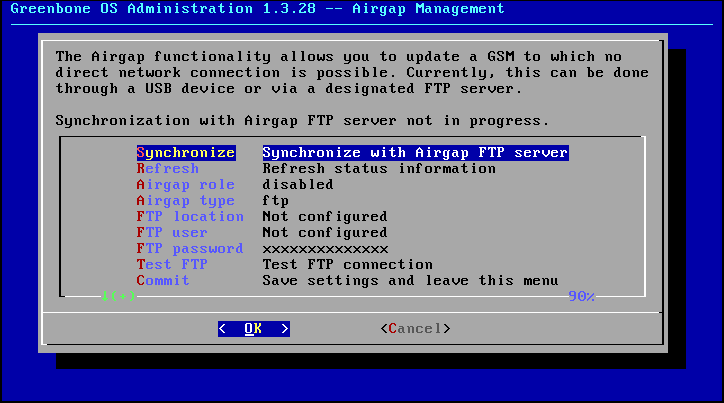
On the master change into the menu Airgap management (see figure The Airgap management can be found in its own submenu.).
Afterwards change the Airgap type to the value ftp and the Airgap role to master.
Afterwards you will get a new parameter in the menu.
Enter the respective values:
- FTP location:
This is the FTP server with folder as complete path.
- FTP user:
This is the FTP user with which to log in.
- FTP password:
This is the password for the log in.
- Test FTP:
You can verify the data entered.
The test verifies if a log in works with the data supplied.
On the slave perform the same set up.
Here only select the to slave.
In order for the synchronization to work flawlessly the synchronization times of the master and slave must be synchronized.
Ensure that the master is allowed enough time for the upload of the feeds so that the slave does not load the feed before the master completed the upload.
The Synctime can be adjusted respectively.
So that the FTP server really displays the function of a diode it should be ensured that the uploaded files are verified after upload.
This can be achieved with the pure-ftpd for example.
This FTP server allows the possibility to run a script after the upload of a file.
It first executes a virus scanner.
After the successful verification the script moves the feed files to anther folder to which the slave has access and downloads the feed from.