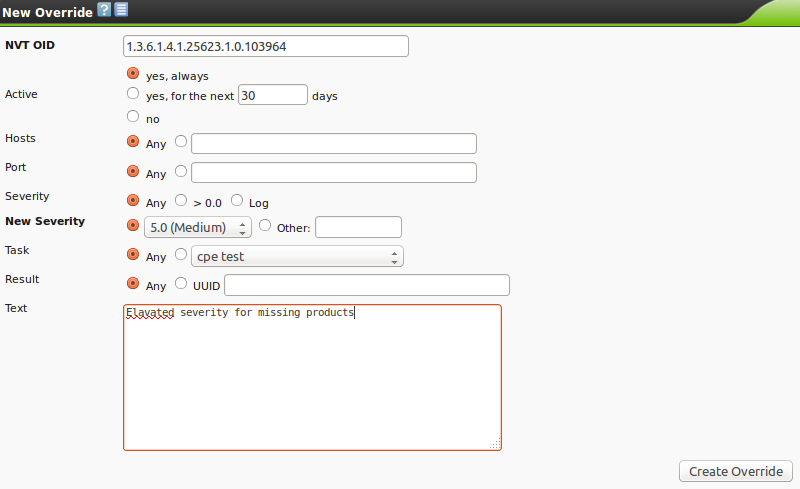
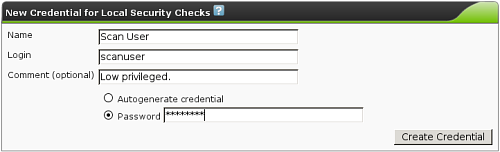
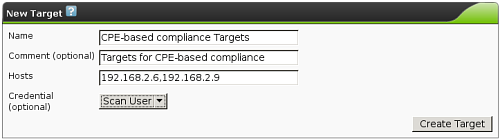
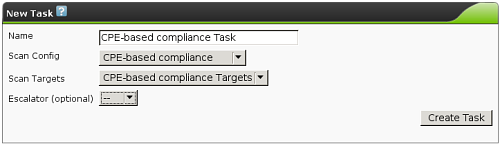
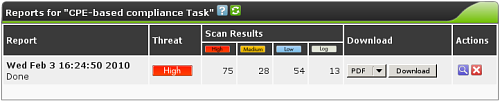
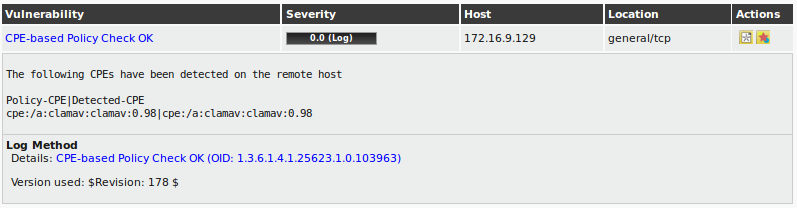
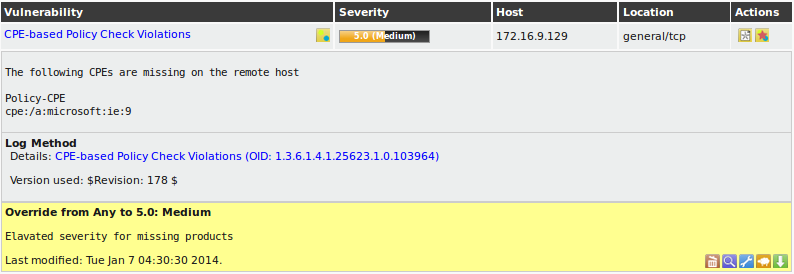
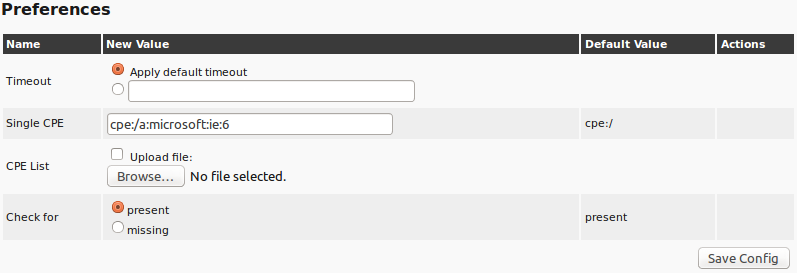
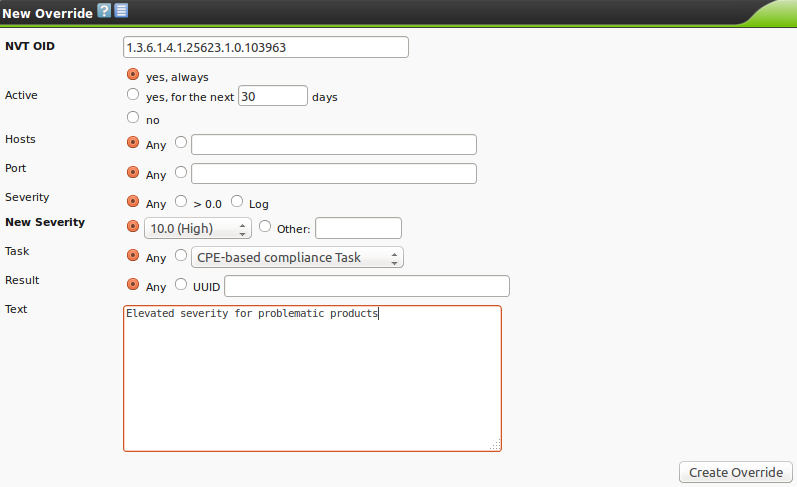
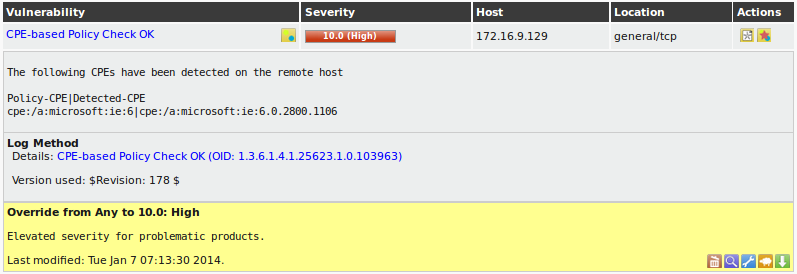
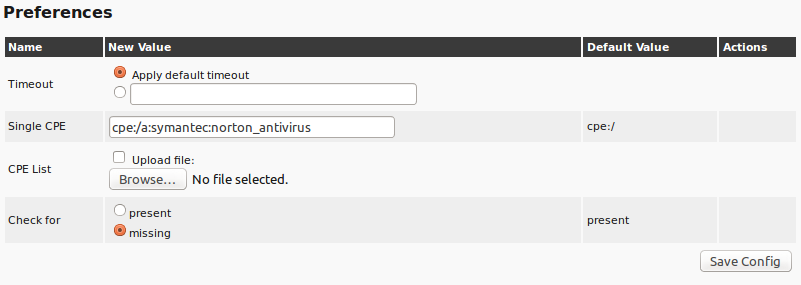
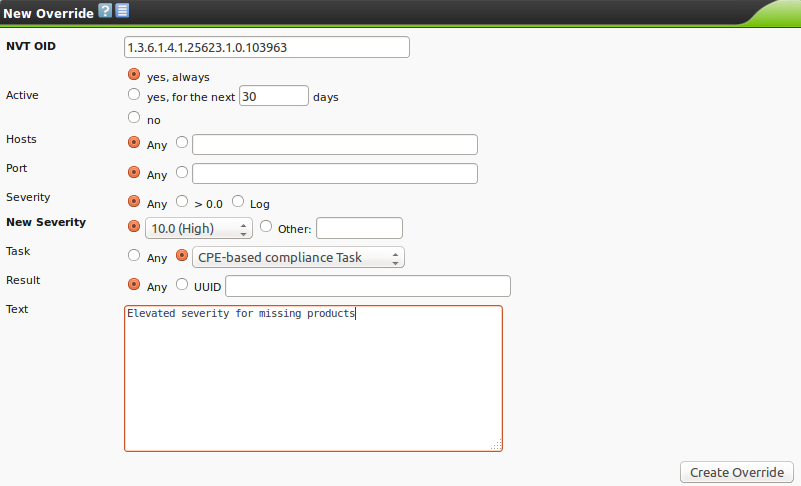
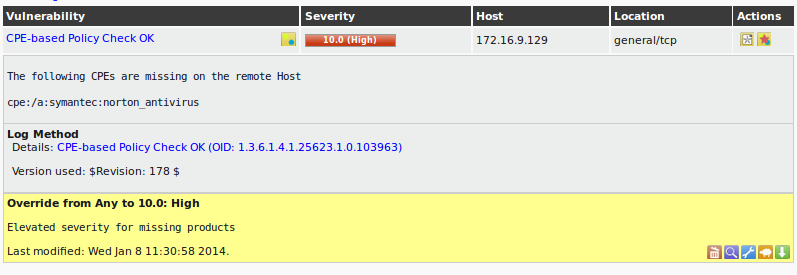
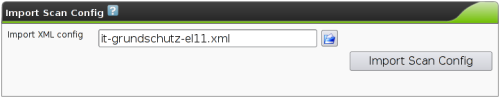
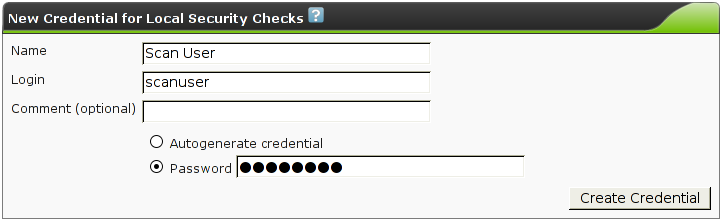
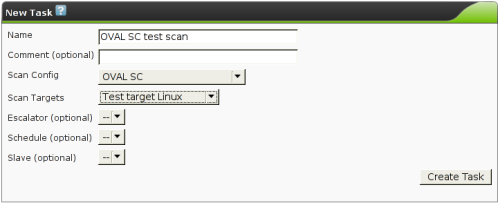
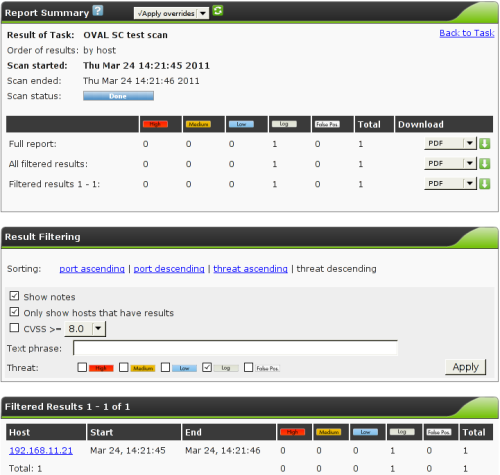
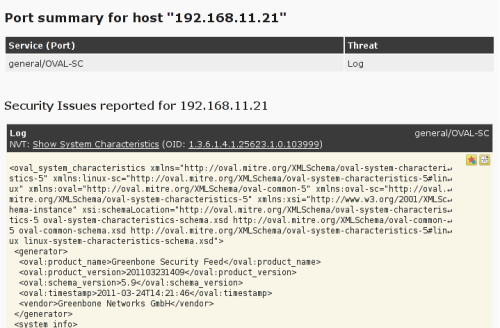
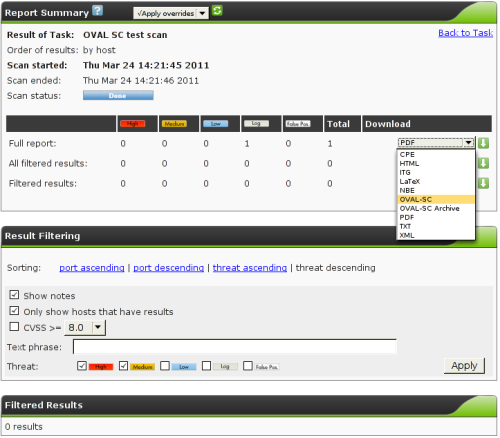
| M4.2 |
Screen lock |
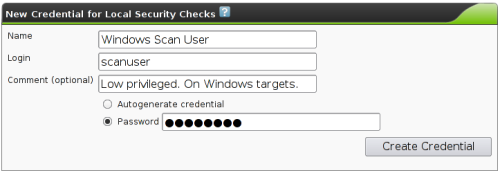
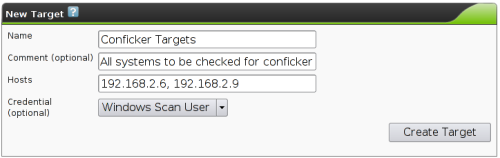
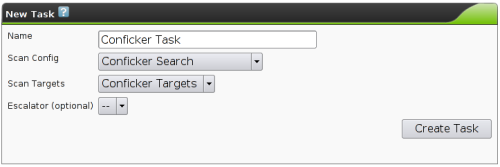
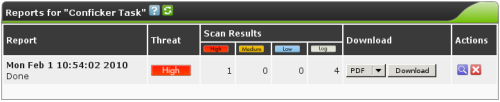
Credentials |
Windows: Can only test for local accounts.
Linux: Only default screen savers in Gnome and KDE. |
| M4.3 |
Use of anti virus protection software |
Credentials |
|
| M4.4 |
Compliant handling of drives for removable media and external data storage devices |
Credentials |
|
| M4.5 |
Logging of telecommunication equipment |
Credentials |
|
| M4.7 |
Changing of default passwords |
Remote |
Test only via SSH and Telnet. |
| M4.9 |
Use of the seccurity mechanisms of XWindows |
Credentials |
|
| M4.14 |
Mandatory password protection in Unix |
Credentials |
|
| M4.15 |
Secure login |
Credentials |
|
| M4.16 |
Access restrictions of user IDs and / or terminals |
Credentials |
|
| M4.17 |
Locking and deleting unneeded accounts and terminals |
Credentials |
|
| M4.18 |
Administrative and technical securing of access to monitoring and single-user mode |
Credentials |
|
| M4.19 |
Restrictive allocation of attributes for UNIX system files and directories |
Credentials |
|
| M4.20 |
Restrictive allocation of attributes for UNIX user files and directories |
Credentials |
|
| M4.21 |
Preventing of unauthorized escalation of administrator rights |
Credentials |
|
| M4.22 |
Preventing of loss of confidentiality of sensitive data in the UNIX system |
Credentials |
|
| M4.23 |
Safe access of executable files |
Credentials |
|
| M4.33 |
Use of a virus scanning program for storage media exchange and data transfer |
Credentials |
|
| M4.36 |
Disabling of certain fax receiving phone numbers |
Credentials |
Cisco devices can only be tested via telnet because they do not support blowfish-cbc encryption. |
| M4.37 |
Disabling of cetrain fax sending phone numbers |
Credentials |
Cisco devices can only be tested via telnet because they do not support blowfish-cbc encryption. |
| M4.40 |
Preventing the unauthorized use of the computer microphone |
Credentials |
Only implemented for Linux. Under Windows it is not possible to determine the status of the microphone via registry/WMI. |
| M4.48 |
Password protection if Windows systems |
Credentials |
|
| M4.49 |
Securing of the the boot process of Windows systems |
Credentials |
|
| M4.52 |
Equipment protection under Windows NT-based systems |
Credentials |
|
| M4.57 |
Deactivation of automatic CD-ROM recognition |
Credentials |
|
| M4.80 |
Sichere Zugriffsmechanismen bei Fernadministration |
Remote |
|
| M4.94 |
Protection of web server files |
Remote |
|
| M4.96 |
Disabling of DNS |
Credentials |
|
| M4.97 |
One service per server |
Remote |
|
| M4.98 |
Limit communication though a packet filter to a minimum |
Credentials |
Microsoft Windows Firewall is being tested. For Vista and newer any firewall that is installed comforming to the system. |
| M4.106 |
Activation of system wide logging |
Credentials |
|
| M4.135 |
Restrictive assigning of access rights to system files |
Credentials |
|
| M4.147 |
Secure use of EFS under Windows |
Credentials |
|
| M4.200 |
Use of USB storage media |
Credentials |
|
| M4.227 |
Use of a local NTP server for time synchronization |
Credentials |
|
| M4.238 |
Use of a local packet filter |
Credentials |
Microsoft Windows Firewall is being tested. For Vista and newer any firewall that is installed comforming to the system. |
| M4.244 |
Secure system configuration of Windows client operating systems |
Credentials |
|
| M4.277 |
Securing of the SMB, LDAP and RCP communication of Windows servers |
Credentials |
|
| M4.284 |
Handling of services of Windows Server 2003 |
Credentials |
|
| M4.285 |
Uninstallation of unneeded client services of Windows Server 2003 |
Credentials |
|
| M4.287 |
Secure administration of VoIP middleware |
Remote |
|
| M4.300 |
Information protection of printers, copies and multi-function equipment |
Remote |
|
| M4.305 |
Use of storage quotas |
Credentials |
|
| M4.310 |
Implementaion of LDAP access to file services |
Remote |
|
| M4.313 |
Providing of secure domain controllers |
Credentials |
|
| M4.325 |
Deletion of swap files |
Credentials |
|
| M4.326 |
Providing the NTFS properties on a Samba file server |
Credentials |
|
| M4.328 |
Secure base configuration of a Samba server |
Credentials |
|
| M4.331 |
Secure configuration of the operating system for a samba server |
Credentials |
|
| M4.332 |
Secure configuration of access controls of a samber server |
Credentials |
|
| M4.333 |
Secure configuration of Winbind under Samba |
Credentials |
|
| M4.334 |
SMB message signing and Samba |
Credentials |
|
| M4.338 |
Use of Windows Vista and new file and registry virtulization |
Credentials |
Only a general test if file and registry virtulization is enabled. |
| M4.339 |
Avoidance of unauthorized use of portable media under Windows Vista and later |
Credentials |
|
| M4.340 |
Use of the Windows user account control UAC starting with Windows Vista |
Credentials |
|
| M4.341 |
Integrity protection starting with Windows Vista |
Credentials |
Where possible technically implemented (active UAC and protected mode in different zones). |
| M4.342 |
Activation of last access certificate stamp starting with Windows Vista |
Credentials |
|
| M4.344 |
Monitoring of Windows Vista-, Windows 7 und Windows Server 2008-Systemen |
Credentials |
|
| M4.368 |
Regular audits of the terminal server environemnt |
Credentials |
|
| M5.8 |
Regular security check of the network |
Remote |
Only a message is being displayed that tests should be performed with up-to date plugins. |
| M5.17 |
Use of the security mechanisms of NFS |
Credentials |
|
| M5.18 |
Use of the security mechanisms of NIS |
Credentials |
|
| M5.19 |
Use of the security mechanisms of sendmail |
Remote |
|
| M5.19 |
Use of the security mechanisms of sendmail |
Credentials |
|
| M5.20 |
Use of the security mechanisms of rlogin, rsh and rcp |
Credentials |
|
| M5.21 |
Secure use of telnet, ftp, tftp and rexec |
Credentials |
|
| M5.34 |
Use of one time passwords |
Credentials |
|
| M5.59 |
Protection from DNS-spoofing with authentication mechanisms |
Credentials |
|
| M5.63 |
Use of GnuPG or PGP |
Credentials |
|
| M5.64 |
Secure shell |
Remote |
|
| M5.66 |
Use of TLS/SSL |
Remote |
|
| M5.72 |
Deactivation of not required net services |
Credentials |
Only displays the services in question. |
| M5.90 |
Use of IPSec under Windows |
Credentials |
|
| M5.91 |
Use of fersonal firewalls for clients |
Credentials |
Microsoft Windows Firewall is being tested. For Vista and newer any firewall that is installed comforming to the system. On Linux systems, displaying if the the iptables rules, if possible. |
| M5.109 |
Use of a e-mail scanners on the mailserver |
Remote |
|
| M5.123 |
Securing of the network commuication under Windows |
Credentials |
|
| M5.131 |
Securing of the IP protocols under Windows Server 2003 |
Credentials |
|
| M5.145 |
Secure use of CUPS |
Credentials |
|
| M5.147 |
Securing of the communication with directory services |
Remote |
|