This chapter covers recurring concepts when using the web user interface of the Greenbone Security Manager.
This includes standard icons, Powerfilters, tags and the graphics in the Secinfo dashboard.
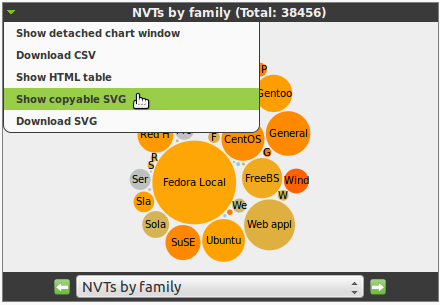
11.2. Charts
The charts in the SecInfo dashboard can be customized.
This allows to display and format the SecInfo data in different ways.
The created graphs can be downloaded and included into other documents.
There are four different chart types available:
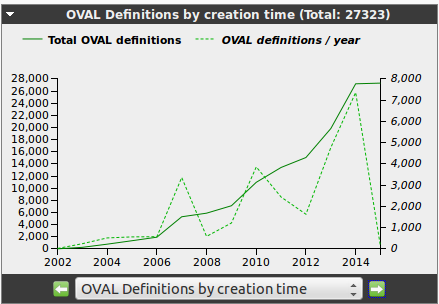
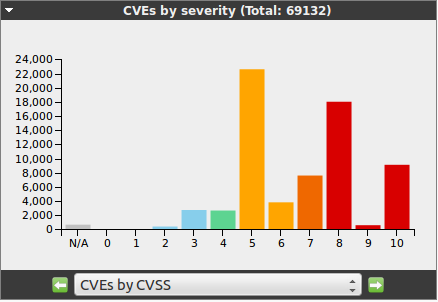
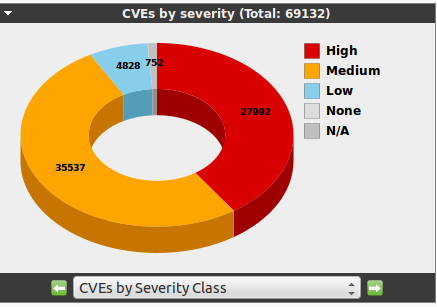
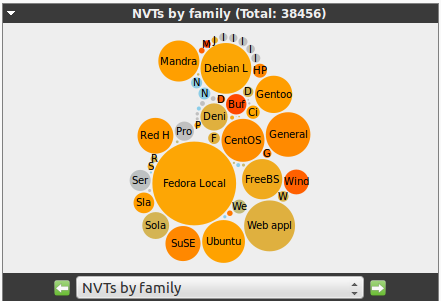
The contents of the charts can be selected via the drop down menu at the bottom of the chart.
This immediately also changes the chart type automatically.
Downloading the pictures or a copy can be selected through the context menu at the top left of the chart.
11.3. Powerfilter
Almost every screen in the web user interface offers the possibility to filter the information displayed.
The required entries can be performed in the filter bar at the top of the web user interface.
The filter bar can be expanded by  .
Then multiple context aware parameters are being displayed that are being combined to become the Powerfilter.
They can be edited in the filter bar directly.
.
Then multiple context aware parameters are being displayed that are being combined to become the Powerfilter.
They can be edited in the filter bar directly.
Thereby the Powerfilter is context aware again.
Should NVTs or targets being filtered more or less options are available respectively after expanding.
Note
The Powerfilter is not case sensitive.
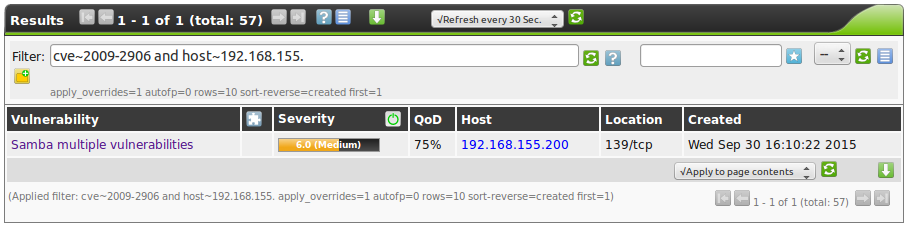
A typical Powerfilter search could search for
all CVE-2009-2906 vulnerabilities within the 192.168.155.0/24 network.
11.3.1. Components
The possible components of the Powerfilter depend on its context.
In general the specification of the following parameters is always possible:
- rows:
- Enter the amount of the results to be displayed.
Mostly the value is rows=10.
Entering a value of
-1 will display all results.
Entering a value of -2 will use the value that was pre-set in My Settings under Rows Per Page.
- first:
- Sets from which position the results should be displayed.
If a search returns 50 results but only 10 should be displayed at the same time, rows=10 first=11 displays the second 10 results.
- sort:
Defines the column that should be used for sorting the results (sort=name).
The results are being sorted ascending.
The name of the column can mostly be deducted from the name of the column.
By clicking the column the name of the column can be verified.
Typical column names are:
- name
- severity
- host
- location
The column names will be changed to small caps and spaces to underscores.
Additionally a couple of other fields are available.
- uuid: The uuid of a result
- comment: A possible comment
- modified: Date and time of the last modification
- created: Data and time of the creation
- sort-reverse:
- Defines the column that should be used for sorting the results (sort-reverse=name).
The results will be sorted descending.
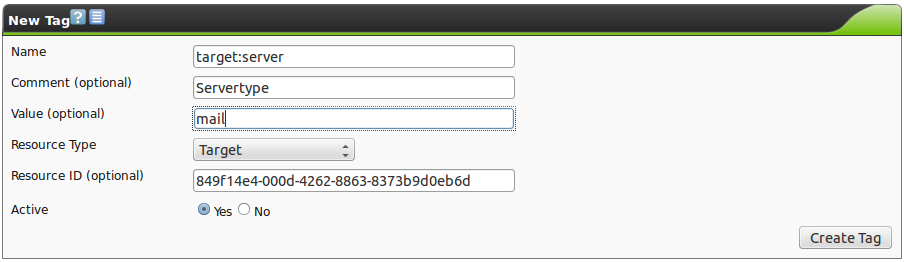
- tag:
- Selects only the results with a specific Tag (see also Tags).
It can be filtered by a specific tag value (tag=”server:mail”) or search only for the tag (tag=”server”).
Regular expressions are also allowed.
Note
By filtering using tags custom categories can be created and used in the filters.
This allows for versatile and granular filter functionality!
When specifying these components many operators can be used:
- = equals i.e. rows=10
- ~ contains i.e. name~admin
- < less than i.e. created<-1 w older than a week
- > greater than i.e. created>-1 w younger than a week
- :RegEx i.e. name:admin$
There are a couple of special features.
If the value is omitted after the equal sign all results will be displayed where this value is not set:
shows all results without a comment.
If the column that should be searched is omitted all columns will be searched:
This searches if at least one column contains the search string.
The data is usually or combined.
This can be specifically specified with the key word or.
To achieve an and-combination the keyword and needs to be specified.
Using not will negate the filter.
11.3.1.1. Date specifications
Date specifications in the Powerfilter can be absolute or relative.
An absolute data specification has the following format:
The time can be omitted:
The time of 12:00am will be assumed automatically.
The date specification can be used in the search filter i.e. created>2014-05-26.
Relative time specifications are always calculated in relation to the current time.
Positive time specification are interpreted as being in the future.
Time specification in the past are defined with a prepended minus (-).
For time periods the following letters can be used:
- s second
- m minute
- h hour
- d day
- w week
- m month (30 days)
- y year (365 days)
To view the results of the past 5 days enter -5d.
A combination 5d1h is not permitted.
This is to be replaced with 121h respectively.
To limit the time period , i.e. month, for which information should be displayed the following expression can be used:
modified>2014-06-01 and modified<2014-07-01
11.3.1.2. Text phrases
In general, additionally text phrases that are being searched for can be specified.
Then only results are being displayed in which the text phrases where found.
If the text phrases or not limited to a column (name=text) all columns will be searched.
This means that also columns that are hidden from the current view will be searched as well.
The following examples can be useful:
overflow- Finds all results that contain the word
overflow.
This applies to both Overflow as well as Bufferoverflow.
Also 192.168.0.1 will find 192.168.0.1 as well as 192.168.0.100.
remote exploit- Will find all results containing
remote or exploit.
Of course results that contain both words will be displayed as well.
remote and exploit- Both words must be found in a result in any column.
The results do not have to be found in the same column.
"remote exploit"- The exact string is being searched for and not the individual words.
regexp 192\.168\.[0-9]+.1- The regex is being searched for.
11.3.2. Saving and Management
Interesting and often used filters can be saved as well.
This simplifies their re-use.
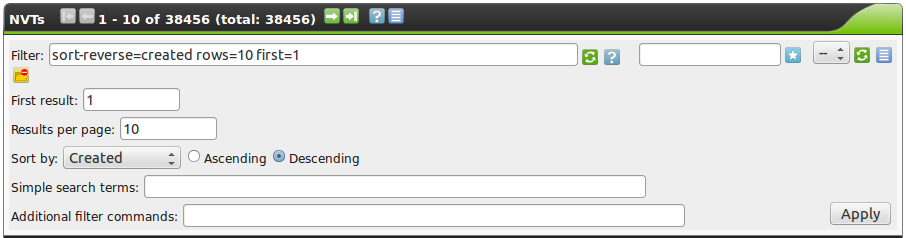
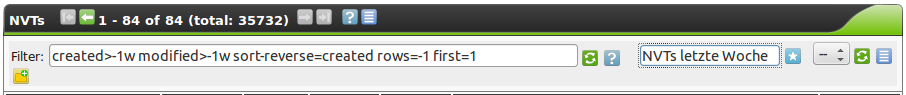
For example, to display the NVTs that were modified or added to the feed last week, in the GUI select SecInfo Management followed by NVTs.
Then edit the Powerfilter so that it has the following content (see figure Often used Powerfilters can be saved and retrieved again.):
Created>-1w or modified>-1w sort-reverse=created rows=1 first=1
This displays all the NVTs that were created or modified last week.
This filter can now be given a name.
Use the field to the right of the Powerfilter.
Enter the name and confirm with  .
The filter is now being saved and can be selected via the drop down box next to it.
.
The filter is now being saved and can be selected via the drop down box next to it.
To use a previously saved filter use the drop down box and confirm afterwards by clicking Switch Filter  (see figure The filters can be selected via the drop down box.).
If Java script is activated the filter is executed immediately after selection from the drop down box.
(see figure The filters can be selected via the drop down box.).
If Java script is activated the filter is executed immediately after selection from the drop down box.
If a specific filter should always be activated in a specific view it can be done in the user settings (see also chapter My Settings).
In this example (see figure Often used filters can be set up as default filter in the user settings.) it is the NVT Filter.
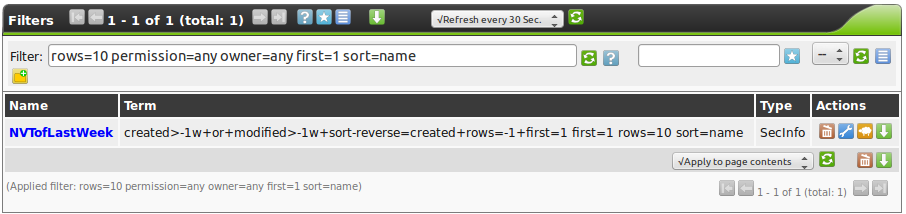
All saved filters can be managed in Configuration/Filters.
Here, filters can be deleted, edited, cloned and exported as GSM object for import into other appliances.
These filters can then be used to filter results of events for the alerts as well.
Filters can be shared.