This section covers the CLI commands for the management of the appliance.
This includes reboot and shutdown, the setting up of the network configuration and the configuration of mail servers and logging servers.
5.5.1. Reboot and shutdown of the appliance
To shut down the appliance enter the shutdown command in the CLI.
Depending on the model in use it can happen that the appliance does not shut itself off automatically.
However, as soon as the shutdown is performed the appliance can be powered off.
gsm: shutdown
Are you sure you want to shutdown the system?
y/n?
y
Possible running scan processes can be restarted after reboot.
To reboot the appliance enter the reboot command in the CLI.
gsm: reboot
Are you sure you want to reboot the system?
y/n? y
A reboot or shutdown will be declined if essential administrative changes are running on the appliance such as an upgrade.
5.5.2. Network configuration
The network configuration in the CLI is preformed via the setting of variables.
A commit is always required after.
The following parameters can be set.
5.5.2.1. hostname
The name of the appliance appears in the scan reports and in the Syslog messages on a central logging server.
It makes sense to choose a descriptive name.
The following characters can be used:
- lower case and upper case letters a-z A-Z
- numbers 0-9
- dash -
gsm: get hostname
s hostname gsm
gsm: set hostname gsm-frankfurt
gsm *: commit
gsm: get hostname
s hostname gsm -frankfurt
5.5.2.2. domainname
The domain name like the hostname appears in the scan reports and the Syslog messages on a central logging server.
Furthermore the configured domain will be used automatically with emails as the sending domain.
Additionally the domain name is appended to not fully qualified hostname as such suffix.
The domain name can use the same characters as the hostname.
gsm: get domainname
s domainname greenbone.net
gsm: set domainname musterfirma.de
gsm *: commit
gsm: get domainname
s domainname musterfirma.de
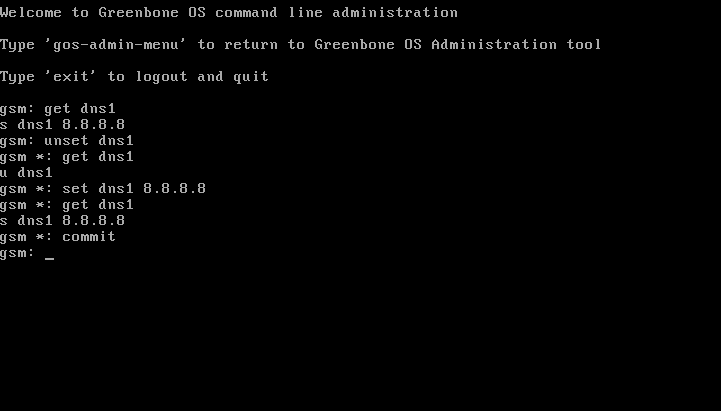
5.5.2.3. DNS server
The GSM appliance supports up to three DNS servers.
At least one DNS server is required.
Additional servers will only be used at an outage of the first server.
Three variables are available:
To delete a DNS server use the unset command.
gsm: get dns2
s dns2 8.8.4.4
gsm: unset dns2
gsm *: commit
gsm: get dns2
u dns2
5.5.2.4. IP Addresses
The GSM appliances come with up to 24 network adapters.
Each of these adapters can be configured with an IPv4 and an IPv6 address.
When using IPv4 addresses the keyword dhcp can be entered.
An IP address will be assigned via DHCP.
The variables are.
address_ethX_ipv4address_ethX_ipv6
For X any number between 0 and 23 can be entered.
This depends on the hardware in use.
gsm: get address_eth0_ipv4
s address_eth0_ipv4 dhcp
gsm: set address_eth0_ipv4 192.168.155.108/24
gsm *: commit
gsm: get address_eth0_ipv6
u address_eth0_ipv6
gsm: set address_eth0_ipv6 2001:db8:0:1::1/64
gsm *: commit
gsm:
After configuring the IP addresses a reboot is required so that the addresses are in actual use.
To delete an IP address use the command unset.
When deleting and IPv4 address it only deactivates this address.
The IPv6 address is still reachable.
Tip
Basically the IPv6-link-local-address is always active on every network adapter as well.
If IPv6 should be disabled the ipv6support variable is used.
It deactivates IPv6 support for the entire appliance.
The link-local-addresses will disabled as well.
5.5.2.5. Default Gateway
To configure the default gateway use the variable default_route_ipv4.
When using DHCP to assign IP addresses the default route will also be set via DHCP unless with the variable default_route_ipv4 a router is set explicitly.
gsm: get default_route_ipv4
u default_route_ipv4
gsm: set default_route_ipv4 192.168.155.1
gsm *: commit
gsm:
Only the IPv4 default gateway can be configured via the CLI.
Complex routing settings must be done via the expert network configuration
(see section Expert Network Configuration).
5.5.2.6. Network Time Protocol
To synchronize the appliance with central time servers the GSM appliance supports the NTP-Protocol.
Two NTP servers the appliance will use for time synchronization can be configured.
The appliance will chose the most suitable server.
During an outage of a server the other server will be used automatically.
The variables ntp_server1 and ntp_server2 are available.
Both variables require an IP address as an entry.
The entry of a DNS name is not allowed.
gsm: set ntp_server1 192.53.103.104
gsm *: commit
To test the use and functionality of the protocol use the ntpq command.
gsm: ntpq
remote refid st t when poll reach delay offset jitter
==============================================================================
*ptbtime1.ptb.de .PTB. 1 u 245 1024 377 14.131 -0.432 0.495
+ptbtime2.ptb.de .PTB. 1 u 1012 1024 377 13.544 0.015 0.354
LOCAL (0) .LOCL. 10 l 53h 64 0 0.000 0.000 0.000
You can determine the configured NTP server, polling, reachability, time delay, offset and jitter.
The asterisk (*) in the first column indicates which server the appliance currently synchronizes with.
5.5.2.7. Mail Server
If you want to send reports after completion of a scan automatically via email the appliance needs to be configured with a mail server.
The appliance itself does not come with a mail server.
Confirm that the mail server that the mail server accepts emails sent form the appliance.
The appliance does not store emails in case of delivery failure.
A second delivery attempt at a later time will not be attempted.
On the mail server possible spam protection such as grey listing must be deactivated for the appliance.
Authentication using a username and password is also not supported by the appliance.
The authentication must be done IP based!
To configure the mail server use the mailhub variable.
gsm: get mailhub
s mailhub mail.greenbone.net
gsm: set mailhub mx.musterfirma.de
gsm *: commit
5.5.2.8. Central Logging Server
The GSM appliance allows for the configuration of a central logging server for the collection of the logs.
The GSM appliance uses the Syslog protocol.
Central collection of the logs allows for central analysis, management and monitoring of logs.
Additionally the logs are also stored locally.
Two logging servers can be configured.
Both will be used.
As transport layer both UDP (default) and TCP can be used.
TCP ensures delivery of the logs even when packet loss occurs.
If packet loss occurs during a transmission vie UDP the log messages will be lost.
Two variables can be configured:
syslog_server1syslog_server2
The format is as follows:
Example:
gsm: set syslog_server1 tcp://192.168.0.5:2000
gsm *: commit
If no port is specified the default port 514 will be used.
If the protocol is not specified UDP will be used.
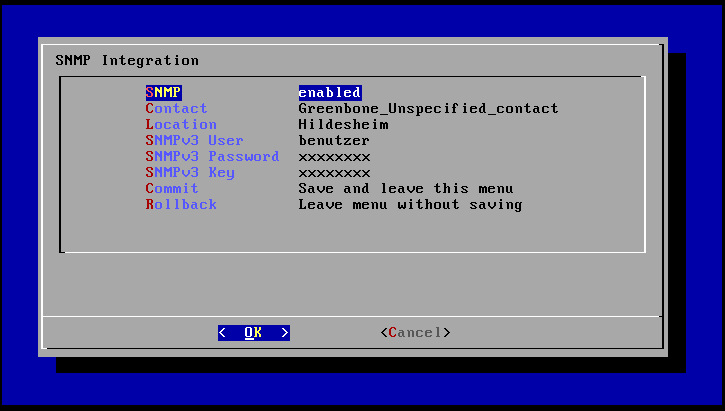
5.5.2.9. SNMP
The GSM appliance supports SNMP.
The SNMP support can both be used for sending of traps through alerts (see section Alerts) as well as the monitoring of vital parameters of the appliance.
The supported parameters are specified in a Management Information Base (MIB) file.
The current MIB is available from the Greenbone tech [doc] portal.
The GSM appliance supports SNMP version 3 for read access and SNMPv1 for traps.
The simplest way to configure the SNMPv3 is via the GOS-Admin-Menu under section Remote and SNMP Configuration.
There is it also explained that the GSM will transfer the SNMPv3 user password with SHA-1 and use AES as encryption.
Sending traps is configured in the GOS-Admin-Menu under Network and SNMP.
Alternatively the following variables allow for the configuration of the SNMP access:
snmpsnmp_keysnmp_passwordsnmp_usersnmp_locationsnmp_contactsnmp_trapsnmp_trapcommunitysnmp_trapreceiver
For sending alerts as SNMP traps use the following parameters.
gsm: set snmp_trap enabled
gsm *: set snmp_trapcommunity public
gsm *: commit
gsm: get snmp_trapreceiver
s snmp_trapreceiver 192.168.0.1
To configure read access for SNMP via CLI, use the respective variables snmp_key, snmp_password, and snmp_user.
Afterwards test read access of the SNMP service under Linux/Unix with snmpwalk:
$ snmpwalk -v 3 -l authPriv -u user -a sha -A password -x aes -X key 192.168.155.180
iso .3.6.1.2.1.1.1.0 = STRING: "Greenbone Security Manager"
iso .3.6.1.2.1.1.5.0 = STRING: "gsm"
...
The following information may be gathered:
- Uptime
- Network interfaces
- Memory
- Harddisk
- Load
- CPU
5.5.3. Expert Network Configuration
The GOS-Admin-Menu and the variables currently only allow for simple network configuration.
The configuration of VLANs or multiple static routes is not possible.
To make respective changes in the configuration an expert mode exists.
It requires the input of all settings via script.
The creation, editing and activation of this script is covered in this section.
Once the expert mode is used IP addresses can no longer be changed via the GOS-Admin-Menu or variables!
To use the expert mode it must be activated first.
Execute the following command in the CLI (see section Command line).
Afterwards an reboot is required.
gsm: set netmode expert
gsm *: commit
gsm: reboot
Are you sure you want to reboot the system?
y/n? y
To revert back to normal mode at the later date use the command set netmode default.
Note that you need to execute commit to enable the set netmod command.
After editing the file expertnet.sh a reboot is required to commit the settings.
Currently the command set netmode expert puts the appliance in a state whereby the user has to enter the entire configuration manually.
To save them permanently the commands must be entered in within the expertnet.sh file and made executable (see below).
To edit the file change into shell mode.
Enter the command shell:
gsm: shell
ATTENTION:
The shell command should only be used by expert users.
To leave the expert mode , type ’exit ’.
admin@gsm :~$ ls -l expertnet.sh
-rwxr --r-- 1 admin admin 131 May 4 2012 expertnet.sh
admin@gsm :~$ _
Since you are in the Greenbone shell the files in the home directory can be displayed with the command ls.
The file expertnet.sh is located here.
The file can be customized with an editor.
vi, vim or nano can be used for editing.
If you are not familiar with the editor vi or vim please use nano as the editor.
It displays help at the bottom of the window.
The keyboard combinations listed all are executed with the Control key: Ctrl-O saves the file.
If the file has not been edited its content looks as follows:
# This script can be used to set custom network parameters like
# VLANS , source based routing and firewall restrictions on the GSM
Editing on a different system and copying the file afterwards with secure copy is not possible.
The GSM does not support secure copying via SSH.
The first change in the file is to insert a first line so that the file looks as follows:
#!/bin/sh
# This script can be used to set custom network parameters like
# VLANS , source based routing and firewall restrictions on the GSM
The first line directs the Greenbone OS to interpret the file using the /bin/sh shell.
Without this line the file will not be executed later.
In order for the file to be able to be executed the file rights need to be configured directly.
Enter the following command in the command line:
admin@gsm :~$ chmod 755 expertnet.sh
All network configurations require the command ip.
The alternate commands ifconfig, route and vconfig should not be used.
Their support can be limited in the future.
To avoid problems with the paths on the appliance the command ip should always be executed with the entire path: /bin/ip
5.5.3.1. Configuration of IP addresses
Configuration of IP addresses can easily be achieved with the ip command.
The configuration is done in three steps:
- Activation of the network adapter
- Configuration of the first IP address
- Configuration of optional additional IP addresses on the same network adapter
After activating the network adapter a delay of 10 second should be included to allow enough time for the network adapter to auto-negotiate.
For consistency in the example this is also done for the loopback adapter.
/bin/ip link set lo up
sleep 10s
/bin/ip addr add 127.0.0.1/8 dev lo
/bin/ip link set eth0 up
sleep 10s
/bin/ip addr add 192.168.81.10/24 dev eth0
/bin/ip -f inet6 addr add 2607: f0d0 :2001::10/114 dev eth0
The first three lines activate and configure the loopback interface.
This network adapter should not be forgotten in the script.
Without the loopback interface the GSM will not work.
The command ip can activate multiple IP addresses on the same network adapter.
ip addr add allows to add additional IP addresses.
The do not replace the existing IP address.
To delete an IP address ip addr del is required explicitly.
5.5.3.2. VLAN support
If switches are configured so that multiple VLANs with Tags (VLAN IDs combined with an IEEE 802.1q - trunk ) are transferred to the GSM they have to be disassembled on the GSM respectively.
Sub-interfaces need to be configured on the physical network adapter.
These sub-interfaces are also created with the ip command.
/bin/ip link set eth1 up
sleep 10
/bin/ip link add link eth1 name eth1 .91 type vlan id 91
/bin/ip link set eth1 .91 up
/bin/ip addr add 192.168.81.26/24 dev eth1 .91
The third command creates a sub-interface called eth1.91 on network adapter eth1.
The name can be freely chosen.
For example, names like ServerNet or MailDMZ can be used.
The flag type vlan instructs the command so that a tagged VLAN is disassembled respectively.
id 91 selects the actual VLAN ID.
The additional lines activate the sub-interface and configure the IP address.
Multiple IPv4 and IPv6 addresses can be configured as well.
In case a VLAN trunk is a native VLAN the physical network adapter can be configured with an IP address.
If no native VLAN was configured an IP address for the physical network adapter is not required.
However, remember to activate the physical network adapter if this is the case!
5.5.3.3. Static Routing
Most networks only have one gateway.
This gateway often is referred to as default gateway.
Sometimes historically grown networks use different routers for different destinations.
If these routers do not communicate data through dynamic routing protocols client systems often require static routes for those destinations.
The expert configuration allows for configuration of unlimited static routes.
When using expert configuration the default gateway also needs to be configured in the expertnet.sh file.
If IPv4 and IPv6 is used for each protocol a separate default gateway needs to be configured.
If auto-configuration is used with IPv6 the default gateway can be omitted.
To set a route also use the ip command with the route argument:
/bin/ip route add default via 192.168.81.1
/bin/ip -f inet6 route add default via 2607: f0d0 :2001::1
The keyword default is dissolved into 0.0.0.0/0 or ::/0 respectively.
To add additional routes the following syntax can be used:
/bin/ip route add 192.168.0.0/24 via 192.168.81.5
A route for network 192.168.0.0/24 is set using the router 192.168.81.5.