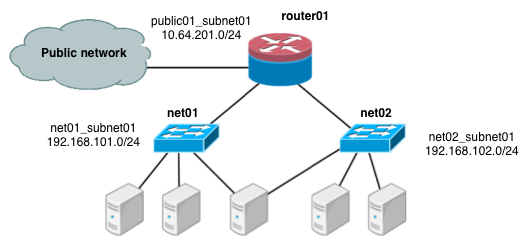
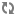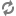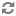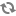The first scenario has two private networks (net01, and
net02), each with one subnet
(net01_subnet01: 192.168.101.0/24,
net02_subnet01, 192.168.102.0/24).
Both private networks are attached to a router that
contains them to the public network (10.64.201.0/24).
Under the service tenant, create the shared router, define the
public network, and set it as the default gateway of the
router
$ tenant=$(keystone tenant-list | awk '/service/ {print $2}')
$ neutron router-create router01
$ neutron net-create --tenant-id $tenant public01 \
--provider:network_type flat \
--provider:physical_network physnet1 \
--router:external=True
$ neutron subnet-create --tenant-id $tenant --name public01_subnet01 \
--gateway 10.64.201.254 public01 10.64.201.0/24 --disable-dhcp
$ neutron router-gateway-set router01 public01Under the demo user tenant, create the private network
net01 and corresponding subnet, and connect it to the
router01 router. Configure it to use VLAN ID 101 on the
physical
switch.
$ tenant=$(keystone tenant-list|awk '/demo/ {print $2}'
$ neutron net-create --tenant-id $tenant net01 \
--provider:network_type vlan \
--provider:physical_network physnet2 \
--provider:segmentation_id 101
$ neutron subnet-create --tenant-id $tenant --name net01_subnet01 net01 192.168.101.0/24
$ neutron router-interface-add router01 net01_subnet01Similarly, for net02, using VLAN ID 102 on the physical
switch:
$ neutron net-create --tenant-id $tenant net02 \
--provider:network_type vlan \
--provider:physical_network physnet2 \
--provider:segmentation_id 102
$ neutron subnet-create --tenant-id $tenant --name net02_subnet01 net02 192.168.102.0/24
$ neutron router-interface-add router01 net02_subnet01