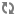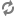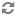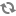The OpenStack Compute API allows the user to specify an admin password when creating (or rebuilding) a server instance. If no password is specified, a randomly generated password is used. The password is returned in the API response.
In practice, the handling of the admin password depends on the hypervisor in use, and may require additional configuration of the instance, such as installing an agent to handle the password setting. If the hypervisor and instance configuration do not support the setting of a password at server create time, then the password returned by the create API call will be misleading, since it was ignored.
To prevent this confusion, the configuration option
enable_instance_password can be used to
disable the return of the admin password for installations
that don't support setting instance passwords.
| Configuration option | Default | Description |
enable_instance_password |
true |
When true, the create and rebuild compute API calls return the server admin password. When false, the server admin password is not included in API responses. |
OpenStack Compute supports API rate limiting for the OpenStack API. The rate limiting allows an administrator to configure limits on the type and number of API calls that can be made in a specific time interval.
When API rate limits are exceeded, HTTP requests will return a error with a status code of 413 "Request entity too large", and will also include a 'Retry-After' HTTP header. The response body will include the error details, and the delay before the request should be retried.
Rate limiting is not available for the EC2 API.
Limits are specified using five values:
The HTTP method used in the API call, typically one of GET, PUT, POST, or DELETE.
A human readable URI that is used as a friendly description of where the limit is applied.
A regular expression. The limit will be applied to all URI's that match the regular expression and HTTP Method.
A limit value that specifies the maximum count of units before the limit takes effect.
An interval that specifies time frame the limit is applied to. The interval can be SECOND, MINUTE, HOUR, or DAY.
Rate limits are applied in order, relative to the HTTP method, going from least to most specific. For example, although the default threshold for POST to */servers is 50 per day, one cannot POST to */servers more than 10 times within a single minute because the rate limits for any POST is 10/min.
OpenStack compute is normally installed with the following limits enabled:
| HTTP method | API URI | API regular expression | Limit |
| POST | any URI (*) | .* | 10 per minute |
| POST | /servers | ^/servers | 50 per day |
| PUT | any URI (*) | .* | 10 per minute |
| GET | *changes-since* | .*changes-since.* | 3 per minute |
| DELETE | any URI (*) | .* | 100 per minute |
The actual limits are specified in the file
etc/nova/api-paste.ini, as part of the WSGI
pipeline.
To enable limits, ensure the 'ratelimit' filter
is included in the API pipeline specification. If the
'ratelimit' filter is removed from the pipeline,
limiting will be disabled. There should also be a definition for the
ratelimit filter. The lines will appear as follows:
[pipeline:openstack_compute_api_v2]
pipeline = faultwrap authtoken keystonecontext ratelimit osapi_compute_app_v2
[pipeline:openstack_volume_api_v1]
pipeline = faultwrap authtoken keystonecontext ratelimit osapi_volume_app_v1
[filter:ratelimit]
paste.filter_factory = nova.api.openstack.compute.limits:RateLimitingMiddleware.factory
To modify the limits, add a 'limits'
specification to the [filter:ratelimit] section of
the file. The limits are specified in the order HTTP method, friendly
URI, regex, limit, and interval. The following example specifies the
default rate limiting values:
[filter:ratelimit]
paste.filter_factory = nova.api.openstack.compute.limits:RateLimitingMiddleware.factory
limits =(POST, "*", .*, 10, MINUTE);(POST, "*/servers", ^/servers, 50, DAY);(PUT, "*", .*, 10, MINUTE);(GET, "*changes-since*", .*changes-since.*, 3, MINUTE);(DELETE, "*", .*, 100, MINUTE)