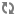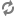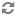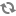| url=ldap://localhost |
The location for the ldap server. |
|
user = dc=Manager,dc=example,dc=com |
(StrOpt) User for the LDAP server to use as default. |
| password = None |
(StrOpt) Password for LDAP server to connect to. |
|
suffix = cn=example,cn=com |
(StrOpt) Default suffix for your LDAP server. |
| use_dumb_member = False |
(Bool) Indicates whether dumb_member settings are in use. |
| allow_subtree_delete = False
|
(Bool) Determine whether to delete LDAP subtrees. |
| dumb_member = cn=dumb,dc=example,dc=com
|
Mockup member as placeholder, for testing purposes. |
| query_scope = one
|
The LDAP scope for queries, this can be either 'one' (onelevel/singleLevel) or 'sub' (subtree/wholeSubtree) |
| user_tree_dn = ou=Users,dc=example,dc=com
|
|
| user_filter =
|
|
| user_objectclass = inetOrgPerson
|
|
| user_id_attribute = cn
|
|
| user_name_attribute = sn
|
|
| user_mail_attribute = email
|
|
| user_pass_attribute = userPassword
|
|
| user_enabled_attribute = enabled
|
Example, userAccountControl. Combines with user_enabled_mask and user_enabled_default settings below to extract the value from an integer
attribute like in Active Directory. |
| user_enabled_mask = 0
|
|
| user_enabled_default = True
|
|
| user_attribute_ignore = tenant_id,tenants
|
|
| user_allow_create = True
|
If the users are managed by another tool and you have only read access, you would set this to False. |
| user_allow_update = True
|
|
| user_allow_delete = True
|
|
| tenant_tree_dn = ou=Groups,dc=example,dc=com
|
|
| tenant_filter =
|
If the backend is providing too much output, you can set a filter to blank so tenants are not passed through. |
| tenant_objectclass = groupOfNames
|
|
| tenant_id_attribute = cn
|
|
| tenant_member_attribute = member
|
|
| tenant_name_attribute = ou
|
|
| tenant_desc_attribute = desc
|
|
| tenant_enabled_attribute = enabled
|
|
| tenant_attribute_ignore =
|
|
| tenant_allow_create = True
|
|
| tenant_allow_update = True
|
|
| tenant_allow_delete = True
|
|
| role_tree_dn = ou=Roles,dc=example,dc=com
|
|
| role_filter =
|
|
| role_objectclass = organizationalRole
|
|
| role_id_attribute = cn
|
|
| role_name_attribute = ou
|
|
| role_member_attribute = roleOccupant
|
|
| role_attribute_ignore =
|
|
| role_allow_create = True
|
|
| role_allow_update = True
|
|
| role_allow_delete = True
|
|
| group_tree_dn =
|
|
| group_filter =
|
|
| group_objectclass = groupOfNames
|
|
| group_id_attribute = cn
|
|
| group_name_attribute = ou
|
|
| group_member_attribute = member
|
|
| group_desc_attribute = desc
|
|
| group_attribute_ignore =
|
|
| group_allow_create = True
|
|
| group_allow_update = True
|
|
| group_allow_delete = True
|
|